-
|
hi, we try to build serious pki with ejbca-ce container (keyfactor/ejbca-ce:7.10.0.2) and using HSM. testing with softhsm2 do quite well, then we try to integrate our ejbca infrastructure with Thales Protect Server 3+ External / Protect ToolKit C 7.2. first we test ejbca with Protect ToolKit C's emurator mode, because the documentation site it seems that but pressing
do you have any idea what I am missing out? or the version of protect toolkit C in explanation of above document site, seems to be a bit old. does ejbca-ce still support latest protect toolkit C's emurator mode? regards, |
Beta Was this translation helpful? Give feedback.
Replies: 9 comments 1 reply
-
|
ProtectServer should be supported. CKR_USER_NOT_LOGGED_IN is a message from the HSM, which makes it sound as if the HSM was not logged into, the session was broken or something like that. Skip auto-activation and activate the crypto token manually. |
Beta Was this translation helpful? Give feedback.
-
|
@primetomas hi, Skip auto-activation does not seem to help. I activated crypto token manually and try to generate key but got same error. any other suggestion? regards, |
Beta Was this translation helpful? Give feedback.
-
|
because softHSM works correctly like this, I have created the exact same objects in the HSM provided by ptk emurator mode using unfortunately still keys are not visible from cryptotoken. ### ptk emurator mode
# pkcs11-tool --module=/opt/safenet/protecttoolkit7/ptk/lib/libcryptoki.so --list-objects -l
Using slot 0 with a present token (0x0)
Logging in to "** slot name is reducted **".
Please enter User PIN:
Certificate Object; type = X.509 cert
label: ca2-signKey
subject: DN: **DN is reducted**
ID: 6361322d7369676e4b6579
Certificate Object; type = X.509 cert
label: ca1-encryptKey
subject: DN: **DN is reducted**
ID: 6361312d656e63727970744b6579
Private Key Object; RSA
label: ca1-signKey
ID: 6361312d7369676e4b6579
Usage: decrypt, sign, unwrap
warning: PKCS11 function C_GetAttributeValue(ALWAYS_AUTHENTICATE) failed: rv = CKR_ATTRIBUTE_TYPE_INVALID (0x12)
Private Key Object; RSA
label: ca2-encryptKey
ID: 6361322d656e63727970744b6579
Usage: decrypt, sign, unwrap
warning: PKCS11 function C_GetAttributeValue(ALWAYS_AUTHENTICATE) failed: rv = CKR_ATTRIBUTE_TYPE_INVALID (0x12)
Certificate Object; type = X.509 cert
label: ca1-signKey
subject: DN: **DN is reducted**
ID: 6361312d7369676e4b6579
Certificate Object; type = X.509 cert
label: ca2-encryptKey
subject: DN: **DN is reducted**
ID: 6361322d656e63727970744b6579
Private Key Object; RSA
label: ca1-encryptKey
ID: 6361312d656e63727970744b6579
Usage: decrypt, sign, unwrap
warning: PKCS11 function C_GetAttributeValue(ALWAYS_AUTHENTICATE) failed: rv = CKR_ATTRIBUTE_TYPE_INVALID (0x12)
Private Key Object; RSA
label: ca2-signKey
ID: 6361322d7369676e4b6579
Usage: decrypt, sign, unwrap
warning: PKCS11 function C_GetAttributeValue(ALWAYS_AUTHENTICATE) failed: rv = CKR_ATTRIBUTE_TYPE_INVALID (0x12)### softHSM
# pkcs11-tool --module=/usr/local/lib/softhsm/libsofthsm2.so --list-objects -l
Using slot 0 with a present token (0x75c81298)
Logging in to "**slot name is reducted**".
Please enter User PIN:
Certificate Object; type = X.509 cert
label: ca2-signKey
subject: DN: **DN is reducted**
ID: 6361322d7369676e4b6579
Certificate Object; type = X.509 cert
label: ca2-encryptKey
subject: DN: **DN is reducted**
ID: 6361322d656e63727970744b6579
Private Key Object; RSA
label: ca2-encryptKey
ID: 6361322d656e63727970744b6579
Usage: decrypt, sign, unwrap
Private Key Object; RSA
label: ca1-encryptKey
ID: 6361312d656e63727970744b6579
Usage: decrypt, sign, unwrap
Private Key Object; RSA
label: ca2-signKey
ID: 6361322d7369676e4b6579
Usage: decrypt, sign, unwrap
Certificate Object; type = X.509 cert
label: ca1-signKey
subject: DN: **DN is reducted**
ID: 6361312d7369676e4b6579
Certificate Object; type = X.509 cert
label: ca1-encryptKey
subject: DN: **DN is reducted**
ID: 6361312d656e63727970744b6579
Private Key Object; RSA
label: ca1-signKey
ID: 6361312d7369676e4b6579
Usage: decrypt, sign, unwrapbut I saw strange error do you think this causes problem? regards, |
Beta Was this translation helpful? Give feedback.
-
|
@primetomas I have enabled ptk library function call logging, with instruction of https://www.thalesdocs.com/gphsm/ptk/protectserver3/docs/ps_ptk_docs/ptkc_programming/logger_library/index.html logs are like this: I checked all log line, but actually C_Login was not called before C_GenerateKeyPair was called. is it expect behaviour of ejbca? if so, how can ejbca avoid |
Beta Was this translation helpful? Give feedback.
-
but does this mean ejbca should call C_Login at least once for interacting HSM, right? the log I checked in #230 (comment), should contains all the pkcs11 operation since ejbca startup. since the log does not contain C_Login, I think ejbca never calls C_Login since startup. is this expected behaviour?
possible. any idea what configuration should I check? I think its not critical one. because we evaluate multiple ca server product and another ca server correctly run on our ptk emurator mode HSM.
I tried to use p11ng like following.
|
Beta Was this translation helpful? Give feedback.
-
|
When using P11NG, you must use the "PKCS11NG Crypto Token" in EJBCA, not the "PKCS11 Crypto Token". "PKCS11 Crypto Token" uses Java PKCS#11 provider where Java/OpenJDK does all the PKCS#11 calls with no control from EJBCA. |
Beta Was this translation helpful? Give feedback.
-
|
@primetomas thanks, but how can I create "PKCS11NG Crypto Token" from command line? I tried could you tell me proper crypto token type to create PKCS11NG backed crypto token? (I checked GUI at https://my.ejcba.deployment/ejbca/adminweb/cryptotoken/cryptotoken.jsf?cryptoTokenId=0&ref=cryptotokens of ejbca ee, but it only shows regards, EDIT: EDIT: adding |
Beta Was this translation helpful? Give feedback.
-
|
@primetomas ok, I can create key with ptk emurator mode, by using |
Beta Was this translation helpful? Give feedback.
-
|
Ah, that was a regression that the Pkcs11NgCryptoToken type does not show up when you do "bin/ejbca.sh cryptotoken --help". But you should be able to do it anyway with the correct type as you noticed. The regression will be fixed in the next release. Thanks for the report. |
Beta Was this translation helpful? Give feedback.

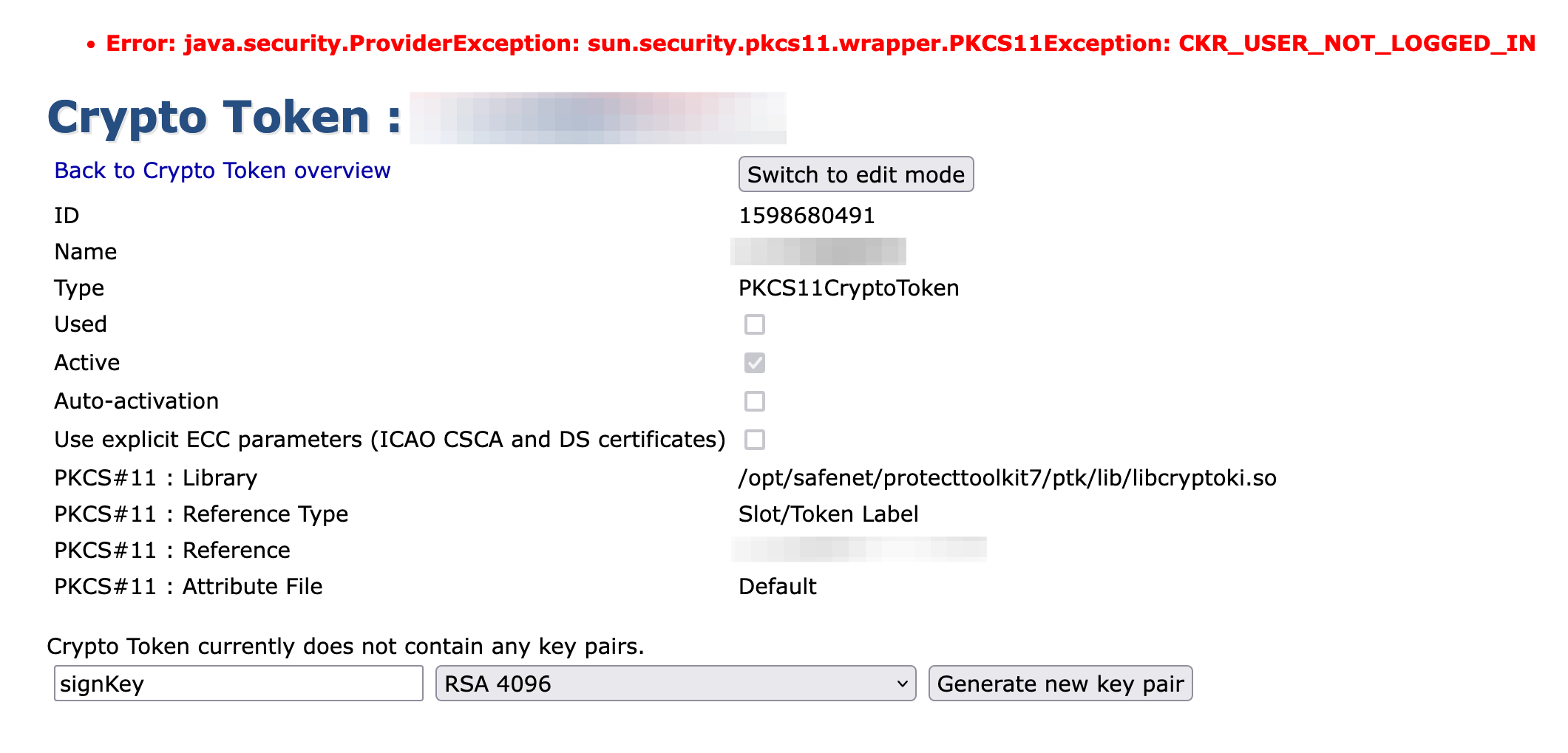
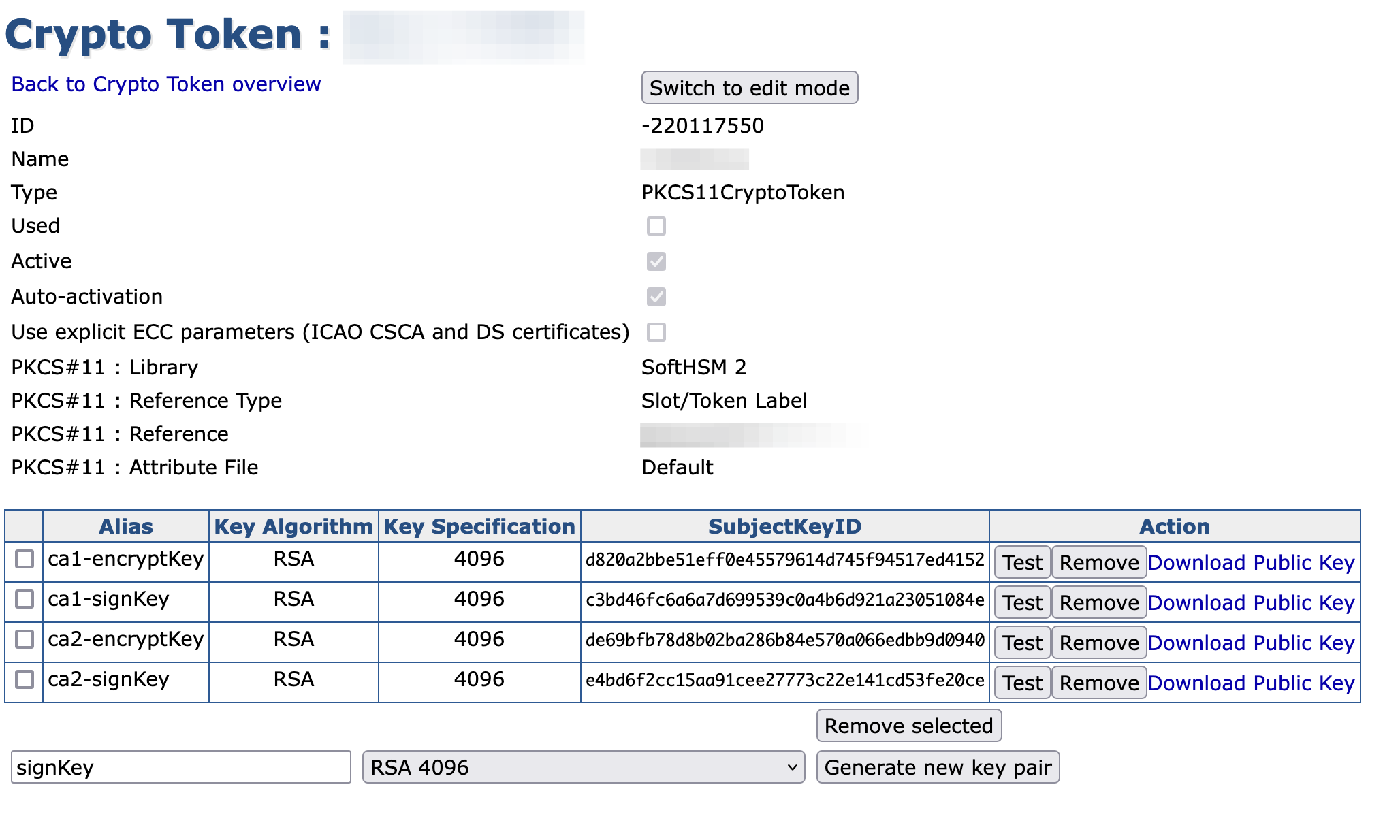
@primetomas thanks, but how can I create "PKCS11NG Crypto Token" from command line? I tried
ejbca.sh cryptotoken create --token ${token_name} --pin ${HSM_PIN} --autoactivate true \ --type PKCS11NGCryptoToken --lib $(crypto_lib) \ --slotlabel "${slot_label}" --slotlabeltype SLOT_LABELbut got errorInvalid CryptoToken type: PKCS11NGCryptoToken.could you tell me proper crypto token type to create PKCS11NG backed crypto token? (I checked GUI at https://my.ejcba.deployment/ejbca/adminweb/cryptotoken/cryptotoken.jsf?cryptoTokenId=0&ref=cryptotokens of ejbca ee, but it only shows
SOFT,Azure Key Vault,AWS KMSin its select box)regards,
EDIT:
--type P11NGCryptoTokenalso does not helpEDIT: …