You signed in with another tab or window. Reload to refresh your session.You signed out in another tab or window. Reload to refresh your session.You switched accounts on another tab or window. Reload to refresh your session.Dismiss alert
title: Set up network for Azure Monitor for SAP solutions (preview)
3
-
description: This article provides details to consider network setup while setting up Azure monitor for SAP solutions.
3
+
description: Learn how to set up an Azure virtual network for use with Azure Monitor for SAP solutions.
4
4
author: MightySuz
5
5
ms.service: virtual-machines-sap
6
6
ms.subservice: baremetal-sap
7
-
ms.topic: article
8
-
ms.date: 07/21/2022
7
+
ms.topic: how-to
8
+
ms.date: 07/28/2022
9
9
ms.author: sujaj
10
-
10
+
#Customer intent: As a developer, I want to set up an Azure virtual network so that I can use Azure Monitor for SAP solutions.
11
11
---
12
12
# Set up network for Azure monitor for SAP solutions (preview)
13
13
14
14
[!INCLUDE [Azure Monitor for SAP solutions public preview notice](./includes/preview-azure-monitor.md)]
15
15
16
-
Before youcan deploy Azure Monitor for SAP solutions (AMS), you need to configure an Azure virtual network with all necessary settings.
16
+
In this how-to guide, you'll learn how to configure an Azure virtual network so that you can deploy *Azure Monitor for SAP solutions (AMS)*. You'll learn to [create a new subnet](#create-new-subnet) for use with Azure Functions for both versions of the product, *AMS* and *AMS (classic)*. Then, if you're using the current version of AMS, you'll learn to [set up outbound internet access](#configure-outbound-internet-access) to the SAP environment that you want to monitor.
17
17
18
-
## Configure new subnet
18
+
## Create new subnet
19
19
20
+
> [!NOTE]
21
+
> This section applies to both AMS and AMS (classic).
20
22
21
-
> [!IMPORTANT]
22
-
> The following steps apply to both *current* and *classic* versions of AMS.
23
+
Azure Functions is the data collection engine for AMS. You'll need to create a new subnet to host Azure Functions.
23
24
24
-
Create a [new subnet with an **IPv4/28** block or larger](../../../azure-functions/functions-networking-options.md#subnets). Then, make sure there's network connectivity between the new subnet and any target systems that you want to monitor.
25
+
[Create a new subnet](../../../azure-functions/functions-networking-options.md#subnets) with an **IPv4/28** block or larger.
25
26
26
-
You'll use this new subnet to host Azure Functions, which is the telemetry collection engine for AMS. For more information, see how to [integrate your app with an Azure virtual network](../../../app-service/overview-vnet-integration.md).
27
+
For more information, see how to [integrate your app with an Azure virtual network](../../../app-service/overview-vnet-integration.md).
27
28
28
29
## Configure outbound internet access
29
30
30
31
> [!IMPORTANT]
31
-
> The following steps only apply to the *current* version of AMS, and not the *classic* version.
32
+
> This section only applies to the current version of AMS. If you're using AMS (classic), skip this section.
32
33
33
-
34
-
In many use cases, you might choose to restrict or block outbound internet access to your SAP network environment. However, AMS requires network connectivity between the [subnet that you configured](#configure-new-subnet) and the systems that you want to monitor. Before you deploy an AMS resource, you need to configure outbound internet access or the deployment will fail.
34
+
In many use cases, you might choose to restrict or block outbound internet access to your SAP network environment. However, AMS requires network connectivity between the [subnet that you configured](#create-new-subnet) and the systems that you want to monitor. Before you deploy an AMS resource, you need to configure outbound internet access, or the deployment will fail.
35
35
36
36
There are multiple methods to address restricted or blocked outbound internet access. Choose the method that works best for your use case:
37
37
38
38
-[Use the **Route All** feature in Azure functions](#use-route-all)
39
39
-[Use service tags with a network security group (NSG) in your virtual network](#use-service-tags)
40
40
-[Use a private endpoint for your subnet](#use-private-endpoint)
41
41
42
-
43
42
### Use Route All
44
43
45
-
**Route All** is a [standard feature of virtual network integration](../../../azure-functions/functions-networking-options.md#virtual-network-integration) in Azure Functions, which is deployed as part of AMS. Enabling or disabling this setting only impacts traffic from Azure Functions. This setting doesn't impact any other incoming or outgoing traffic within your virtual network.
44
+
**Route All** is a [standard feature of virtual network integration](../../../azure-functions/functions-networking-options.md#virtual-network-integration) in Azure Functions, which is deployed as part of AMS. Enabling or disabling this setting only affects traffic from Azure Functions. This setting doesn't affect any other incoming or outgoing traffic within your virtual network.
46
45
47
46
You can configure the **Route All** setting when you create an AMS resource through the Azure portal. If your SAP environment doesn't allow outbound internet access, disable **Route All**. If your SAP environment allows outbound internet access, keep the default setting to enable **Route All**.
48
47
49
-
> [!NOTE]
50
-
> You can only use this option before you deploy an AMS resource. It's not possible to change the **Route All** setting after you create the AMS resource.
48
+
You can only use this option before you deploy an AMS resource. It's not possible to change the **Route All** setting after you create the AMS resource.
51
49
52
50
### Use service tags
53
51
54
52
If you use NSGs, you can create AMS-related [virtual network service tags](../../../virtual-network/service-tags-overview.md) to allow appropriate traffic flow for your deployment. A service tag represents a group of IP address prefixes from a given Azure service.
55
53
56
-
> [!NOTE]
57
-
> You can use this option after you've deployed an AMS resource.
54
+
You can use this option after you've deployed an AMS resource.
58
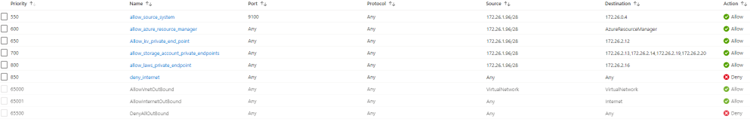
55
59
56
1. Find the subnet associated with your AMS managed resource group:
60
57
1. Sign in to the [Azure portal](https://portal.azure.com).
@@ -71,88 +68,91 @@ If you use NSGs, you can create AMS-related [virtual network service tags](../..
| 660 | deny_internet | Any | Any | Any | Internet | Deny |
79
76
80
77
81
-
AMS subnet IP refers to Ip of subnet associated with AMS resource
82
-
83
-

78
+
The AMS subnet IP address refers to the IP of the subnet associated with your AMS resource. To find the subnet, go to the AMS resource in the Azure portal. On the **Overview** page, review the **vNet/subnet** value.
84
79
85
80
For the rules that you create, **allow_vnet** must have a lower priority than **deny_internet**. All other rules also need to have a lower priority than **allow_vnet**. However, the remaining order of these other rules is interchangeable.
86
81
87
82
### Use private endpoint
88
-
You can enable a private endpoint by creating a new subnet in the same virtual network as the system that you want to monitor. No other resources can use this subnet, so it's not possible to use the same subnet as Azure Functions for your private endpoint.
89
-
To create a private endpoint for AMS:
90
83
84
+
You can enable a private endpoint by creating a new subnet in the same virtual network as the system that you want to monitor. No other resources can use this subnet. It's not possible to use the same subnet as Azure Functions for your private endpoint.
85
+
86
+
To create a private endpoint for AMS:
91
87
92
88
1.[Create a new subnet](../../../virtual-network/virtual-network-manage-subnet.md#add-a-subnet) in the same virtual network as the SAP system that you're monitoring.
93
89
1. In the Azure portal, go to your AMS resource.
94
90
1. On the **Overview** page for the AMS resource, select the **Managed resource group**.
95
-
A private endpoint connection needs to be created for the following resources inside the managed resource group:
96
-
1. Key-vault,
97
-
2. Storage-account, and
98
-
3. Log-analytics workspace
91
+
1. Create a private endpoint connection for the following resources inside the managed resource group.

101
-
102
-
###### Key Vault
96
+
#### Create key vault endpoint
103
97
104
-
Only 1 private endpoint is required for all the key vault resources (secrets, certificates, and keys). Once a private endpoint is created for key vault, the vault resources cannot be accessed from systems outside the given vnet.
98
+
You only need one private endpoint for all the Azure Key Vault resources (secrets, certificates, and keys). Once a private endpoint is created for key vault, the vault resources can't be accessed from systems outside the given vnet.
105
99
106
100
1. On the key vault resource's menu, under **Settings**, select **Networking**.
107
101
1. Select the **Private endpoint connections** tab.
108
102
1. Select **Create** to open the endpoint creation page.
109
103
1. On the **Basics** tab, enter or select all required information.
110
-
1. On the **Resource** tab, enter or select all required information. For the key vault resource, there's only one sub-resource available, the vault.
104
+
1. On the **Resource** tab, enter or select all required information. For the key vault resource, there's only one subresource available, the vault.
111
105
1. On the **Virtual Network** tab, select the virtual network and the subnet that you created specifically for the endpoint. It's not possible to use the same subnet as the Azure Functions app.
112
106
1. On the **DNS** tab, for **Integrate with private DNS zone**, select **Yes**. If necessary, add tags.
113
107
1. Select **Review + create** to create the private endpoint.
114
108
1. On the **Networking** page again, select the **Firewalls and virtual networks** tab.
115
109
1. For **Allow access from**, select **Allow public access from all networks**.
116
110
1. Select **Apply** to save the changes.
117
111
118
-
### Create storage endpoint
112
+
####Create storage endpoint
119
113
120
114
It's necessary to create a separate private endpoint for each Azure Storage account resource, including the queue, table, storage blob, and file. If you create a private endpoint for the storage queue, it's not possible to access the resource from systems outside of the virtual networking, including the Azure portal. However, other resources in the same storage account are accessible.
121
115
122
-
Repeat the following process for each type of storage sub-resource (table, queue, blob, and file):
116
+
Repeat the following process for each type of storage subresource (table, queue, blob, and file):
123
117
124
118
1. On the storage account's menu, under **Settings**, select **Networking**.
125
119
1. Select the **Private endpoint connections** tab.
126
120
1. Select **Create** to open the endpoint creation page.
127
121
1. On the **Basics** tab, enter or select all required information.
128
-
1. On the **Resource** tab, enter or select all required information. For the **Target sub-resource**, select one of the sub-resource types (table, queue, blob, or file).
122
+
1. On the **Resource** tab, enter or select all required information. For the **Target sub-resource**, select one of the subresource types (table, queue, blob, or file).
129
123
1. On the **Virtual Network** tab, select the virtual network and the subnet that you created specifically for the endpoint. It's not possible to use the same subnet as the Azure Functions app.
130
124
1. On the **DNS** tab, for **Integrate with private DNS zone**, select **Yes**. If necessary, add tags.
131
125
1. Select **Review + create** to create the private endpoint.
132
126
1. On the **Networking** page again, select the **Firewalls and virtual networks** tab.
133
127
1. For **Allow access from**, select **Allow public access from all networks**.
134
128
1. Select **Apply** to save the changes.
135
129
136
-
### Create log analytics endpoint
130
+
####Create log analytics endpoint
137
131
138
132
It's not possible to create a private endpoint directly for a Log Analytics workspace. To enable a private endpoint for this resource, you can connect the resource to an [Azure Monitor Private Link Scope (AMPLS)](../../../azure-monitor/logs/private-link-security.md). Then, you can create a private endpoint for the AMPLS resource.
139
133
140
134
If possible, create the private endpoint before you allow any system to access the Log Analytics workspace through a public endpoint. Otherwise, you'll need to restart the Function App before you can access the Log Analytics workspace through the private endpoint.
141
135
136
+
Select a scope for the private endpoint:
137
+
142
138
1. Go to the Log Analytics workspace in the Azure portal.
143
139
1. In the resource menu, under **Settings**, select **Network isolation**.
144
140
1. Select **Add** to create a new AMPLS setting.
145
141
1. Select the appropriate scope for the endpoint. Then, select **Apply**.
146
-
To enable private endpoint for Azure Monitor Private Link Scope, go to Private Endpoint connections tab under configure.
1. Select the **Private endpoint connections** tab.
150
-
1. Select **Create** to open the endpoint creation page.
143
+
Create the private endpoint:
144
+
145
+
1. Go to the AMPLS resource in the Azure portal.
146
+
1. In the resource menu, under **Configure**, select **Private Endpoint connections**.
147
+
1. Select **Private Endpoint** to create a new endpoint.
151
148
1. On the **Basics** tab, enter or select all required information.
152
149
1. On the **Resource** tab, enter or select all required information.
153
150
1. On the **Virtual Network** tab, select the virtual network and the subnet that you created specifically for the endpoint. It's not possible to use the same subnet as the Azure Functions app.
154
151
1. On the **DNS** tab, for **Integrate with private DNS zone**, select **Yes**. If necessary, add tags.
155
152
1. Select **Review + create** to create the private endpoint.
153
+
154
+
Configure the scope:
155
+
156
156
1. Go to the Log Analytics workspace in the Azure portal.
157
157
1. In the resource's menu, under **Settings**, select **Network Isolation**.
158
158
1. Under **Virtual networks access configuration**:
@@ -167,7 +167,7 @@ If you enable a private endpoint after any system accessed the Log Analytics wor
167
167
1. On the managed resource group's page, select the **Function App**.
168
168
1. On the Function App's **Overview** page, select **Restart**.
169
169
170
-
Next, find and note important IP address ranges.
170
+
Find and note important IP address ranges:
171
171
172
172
1. Find the AMS resource's IP address range.
173
173
1. Go to the AMS resource in the Azure portal.
@@ -178,27 +178,29 @@ Next, find and note important IP address ranges.
178
178
1. On the **Overview** page, note the **Private endpoint** in the resource group.
179
179
1. In the resource group's menu, under **Settings**, select **DNS configuration**.
180
180
1. On the **DNS configuration** page, note the **IP addresses** for the private endpoint.
181
+
1. Find the subnet for the log analytics private endpoint.
182
+
1. Go to the private endpoint created for the AMPLS resource.
183
+
2. On the private endpoint's menu, under **Settings**, select **DNS configuration**.
184
+
3. On the **DNS configuration** page, note the associated IP addresses.
185
+
4. Go to the AMS resource in the Azure portal.
186
+
5. On the **Overview** page, select the **vNet/subnet** to go to that resource.
187
+
6. On the virtual network page, select the subnet that you used to create the AMS resource.
181
188
182
-
1. For Log analytics private endpoint: Go to the private endpoint created for Azure Monitor Private Link Scope resource.
183
-
184
-

185
-
186
-
1. On the private endpoint's menu, under **Settings**, select **DNS configuration**.
187
-
1. On the **DNS configuration** page, note the associated IP addresses.
188
-
1. Go to the AMS resource in the Azure portal.
189
-
1. On the **Overview** page, select the **vNet/subnet** to go to that resource.
190
-
1. On the virtual network page, select the subnet that you used to create the AMS resource.
189
+
Add outbound security rules:
191
190
192
191
1. Go to the NSG resource in the Azure portal.
193
192
1. In the NSG menu, under **Settings**, select **Outbound security rules**.
194
-
The below image contains the required security rules for AMS resource to work.
195
-
196
-
193
+
1. Add the following required security rules.
194
+
195
+
| Priority | Description |
196
+
| -------- | ------------- |
197
+
| 550 | Allow the source IP for making calls to source system to be monitored. |
198
+
| 600 | Allow the source IP for making calls Azure Resource Manager service tag. |
199
+
| 650 | Allow the source IP to access key-vault resource using private endpoint IP. |
200
+
| 700 | Allow the source IP to access storage-account resources using private endpoint IP. (Include IPs for each of storage account sub resources: table, queue, file, and blob) |
201
+
| 800 | Allow the source IP to access log-analytics workspace resource using private endpoint IP. |
202
+
203
+
## Next steps
197
204
198
-
| Priority | Description |
199
-
| -------- | ------------- |
200
-
| 550 | Allow the source IP for making calls to source system to be monitored. |
201
-
| 600 | Allow the source IP for making calls AzureResourceManager service tag. |
202
-
| 650 | Allow the source IP to access key-vault resource using private endpoint IP. |
203
-
| 700 | Allow the source IP to access storage-account resources using private endpoint IP. (Include IPs for each of storage account sub resources: table, queue, file, and blob) |
204
-
| 800 | Allow the source IP to access log-analytics workspace resource using private endpoint IP. |
205
+
-[Quickstart: set up AMS through the Azure portal](azure-monitor-sap-quickstart.md)
206
+
-[Quickstart: set up AMS with PowerShell](azure-monitor-sap-quickstart-powershell.md)
0 commit comments