|
| 1 | +--- |
| 2 | +layout: home |
| 3 | +title: "Configuring authentication in OpenAM via Yandex Cloud using the SAML protocol" |
| 4 | +landing-title2: "Configuring authentication in OpenAM via Yandex Cloud using the SAML protocol" |
| 5 | +description: "Step-by-step guide to configure SAML 2.0 federation between Yandex Cloud (IdP) and OpenAM / Open Identity Platform (SP). Includes Docker deployment, certificate import, realm setup, and full working SSO test" |
| 6 | +keywords: 'SAML Yandex Cloud, OpenAM SAML integration, Yandex Cloud Identity Provider, OpenAM as Service Provider, Open Identity Platform SAML, Yandex Cloud SSO, OpenAM federation setup, SAML 2.0 Yandex, OpenAM Docker deployment, Yandex Cloud IdP configuration, single sign-on Yandex OpenAM, OpenAM external IdP, Yandex Cloud SAML metadata, OpenAM hosted SP, SAML authentication tutorial, OpenAM auto-federation, Yandex Cloud user pool SAML, OpenIG SSO preparation, Open Identity Platform documentation' |
| 7 | +imageurl: 'openam-og.png' |
| 8 | +share-buttons: true |
| 9 | +products: |
| 10 | +- openam |
| 11 | +--- |
| 12 | + |
| 13 | +# Configuring authentication in OpenAM via Yandex Cloud using the SAML protocol |
| 14 | + |
| 15 | + |
| 16 | +## Introduction |
| 17 | + |
| 18 | +In this article, we will configure authentication in OpenAM using user accounts via Yandex Cloud. This will allow you to configure authentication in your corporate applications via OpenAM using Yandex Cloud as the Identity Provider (IdP) and OpenAM as the Service Provider (SP). |
| 19 | + |
| 20 | +## Configuring Yandex Cloud |
| 21 | + |
| 22 | +1. Go to the [Yandex Cloud Organization](https://org.cloud.yandex.ru/) service. |
| 23 | +2. Open the **Identity Hub** tab. |
| 24 | +3. In the left pane, select the [Applications](https://center.yandex.cloud/organization/apps) section. |
| 25 | +4. Click the **Create Application** button |
| 26 | +5. Select the SAML (Security Assertion Markup Language) application type |
| 27 | +6. Enter the application name, for example, **openam-saml** |
| 28 | +7. Click the **Create Application** button |
| 29 | + |
| 30 | + |
| 31 | + |
| 32 | + |
| 33 | +After creating the application, open its settings and click the **Download Certificate** button. We will need it for further configuration of OpenAM. |
| 34 | + |
| 35 | +### Service Provider Configuration |
| 36 | + |
| 37 | +1. Open the Yandex settings for the **openam-saml** application and configure the settings: |
| 38 | +1. **SP Entity ID:** `http://localhost:8080/openam` |
| 39 | +2. **ACS URL:** `http://localhost:8080/openam/Consumer/metaAlias/sp` |
| 40 | +2. Save the changes. |
| 41 | + |
| 42 | +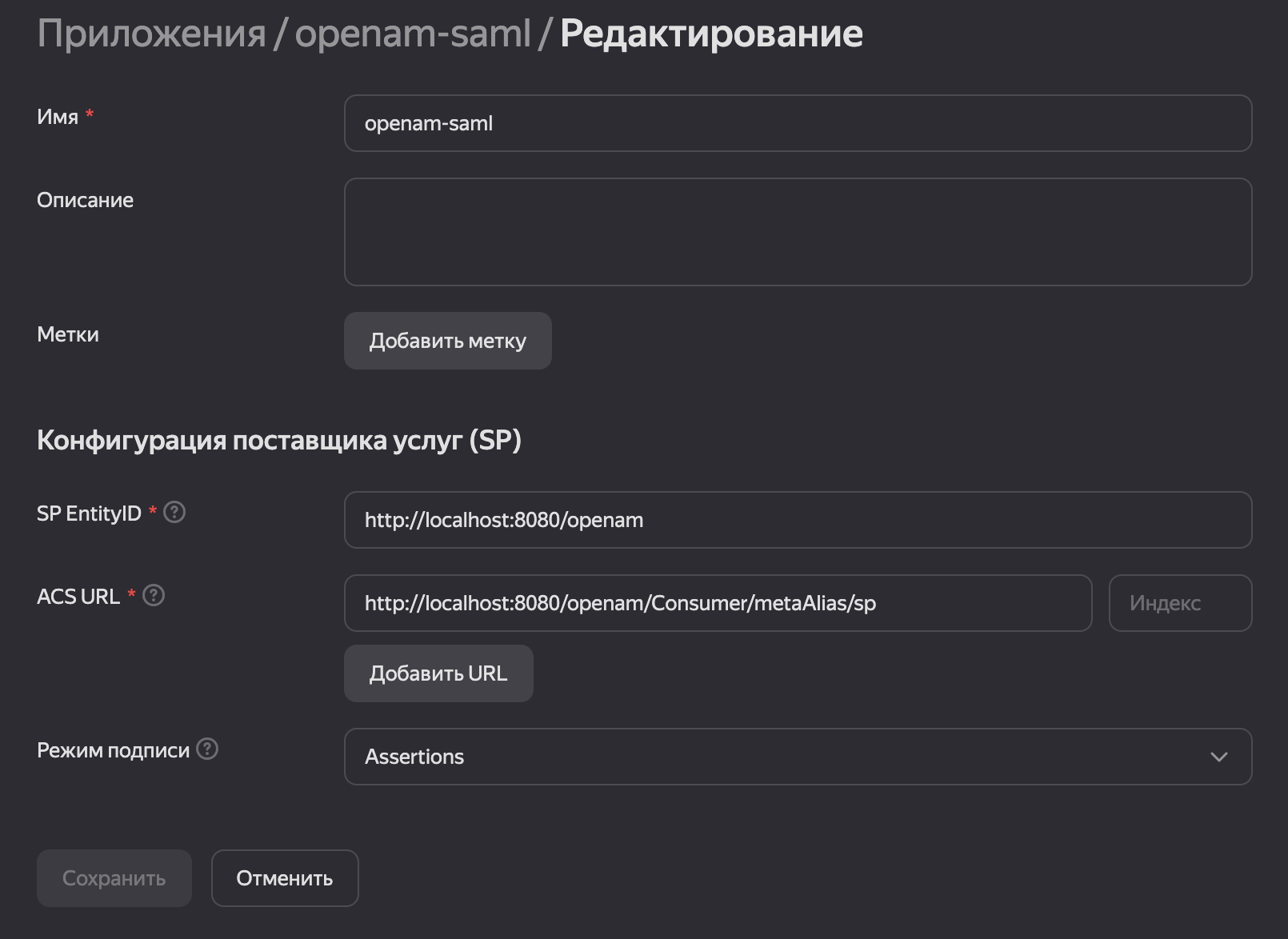 |
| 43 | + |
| 44 | +### Adding users |
| 45 | + |
| 46 | +Add a user pool: |
| 47 | + |
| 48 | +1. In the **Identity Hub** section, select **User Pools** from the menu on the left. |
| 49 | +2. Click the **Create User Pool** button. |
| 50 | +3. Enter the pool details and click **Create User Pool**. |
| 51 | + |
| 52 | +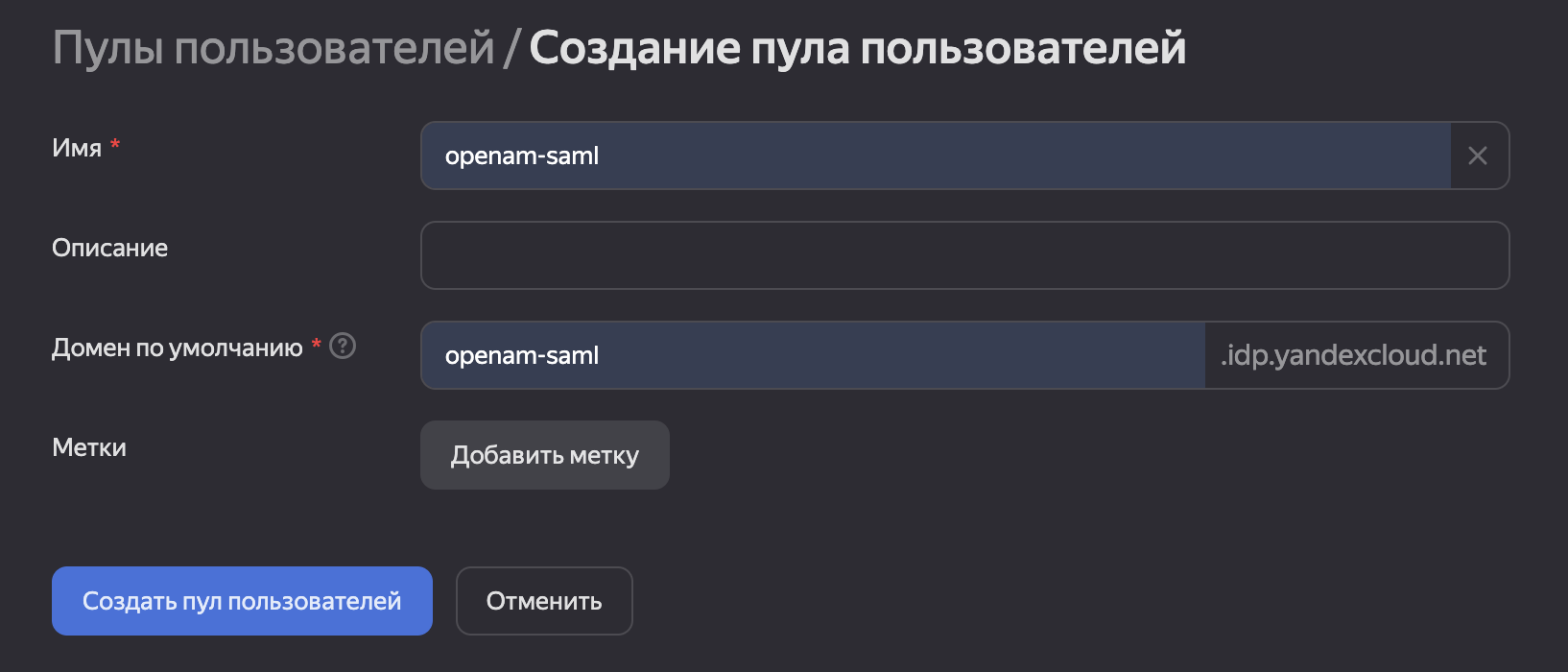 |
| 53 | + |
| 54 | +Add a user to the pool |
| 55 | + |
| 56 | +1. In the **Identity Hub** section of the left-hand menu, select **Users** |
| 57 | +2. Click the **Add User** button |
| 58 | +3. In the pop-up menu, select **Create New User** |
| 59 | +4. Remember the password, as you will need it to log in to OpenAM |
| 60 | +5. Enter the user details and click **Add User** |
| 61 | + |
| 62 | +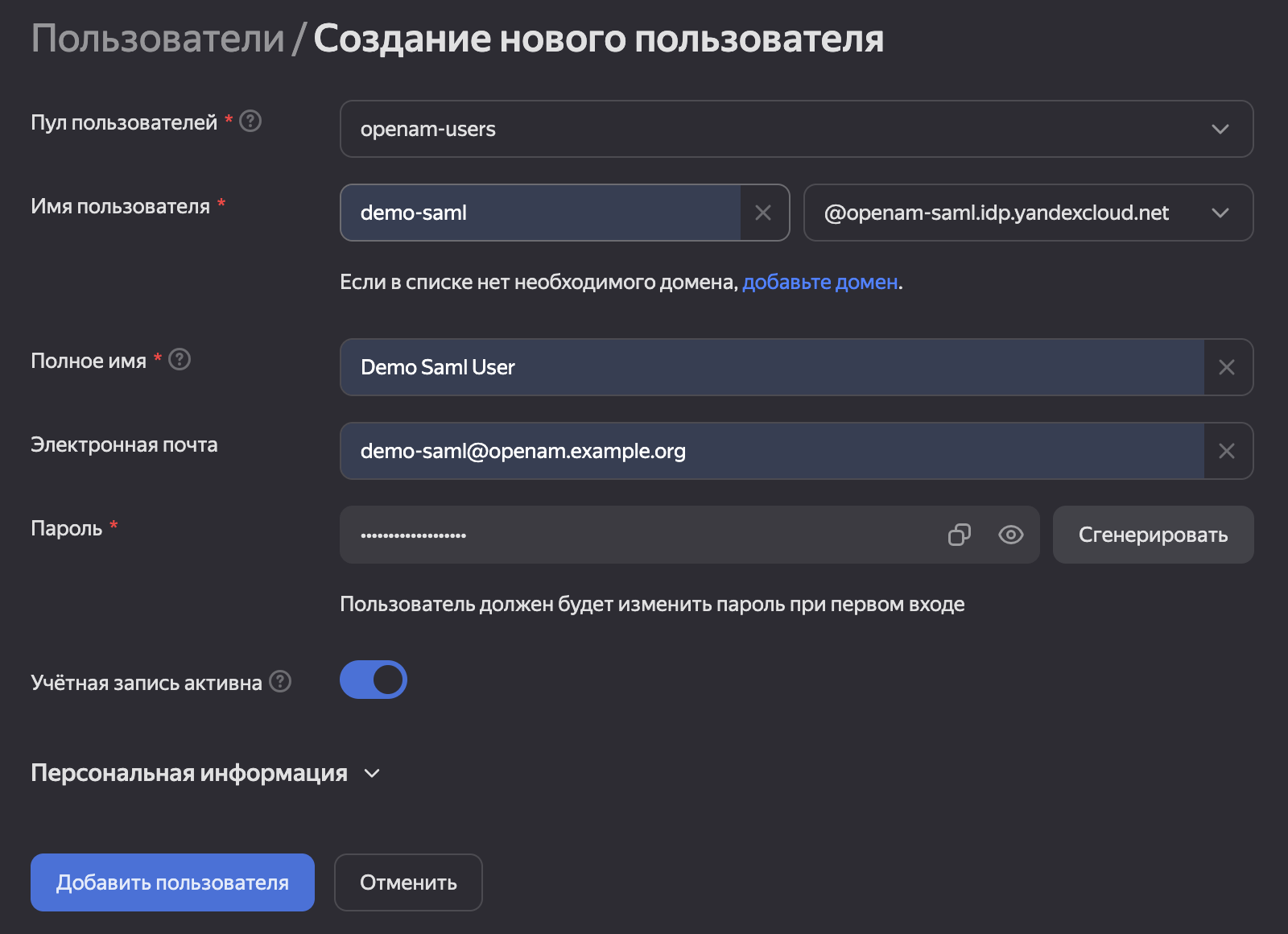 |
| 63 | + |
| 64 | +## Configuring OpenAM |
| 65 | + |
| 66 | +### Installing OpenAM |
| 67 | + |
| 68 | +For simplicity, deploy OpenAM in a Docker container with the command |
| 69 | + |
| 70 | +```bash |
| 71 | +docker run -p 8080:8080 --name openam openidentityplatform/openam |
| 72 | +``` |
| 73 | + |
| 74 | +And perform the initial setup |
| 75 | + |
| 76 | +```bash |
| 77 | +docker exec -w '/usr/openam/ssoconfiguratortools' openam bash -c \ |
| 78 | +'echo "ACCEPT_LICENSES=true |
| 79 | +SERVER_URL=http://localhost:8080 |
| 80 | +DEPLOYMENT_URI=/$OPENAM_PATH |
| 81 | +BASE_DIR=$OPENAM_DATA_DIR |
| 82 | +locale=en_US |
| 83 | +PLATFORM_LOCALE=en_US |
| 84 | +AM_ENC_KEY= |
| 85 | +ADMIN_PWD=passw0rd |
| 86 | +AMLDAPUSERPASSWD=p@passw0rd |
| 87 | +COOKIE_DOMAIN=localhost |
| 88 | +ACCEPT_LICENSES=true |
| 89 | +DATA_STORE=embedded |
| 90 | +DIRECTORY_SSL=SIMPLE |
| 91 | +DIRECTORY_SERVER=localhost |
| 92 | +DIRECTORY_PORT=50389 |
| 93 | +DIRECTORY_ADMIN_PORT=4444 |
| 94 | +DIRECTORY_JMX_PORT=1689 |
| 95 | +ROOT_SUFFIX=dc=openam,dc=example,dc=org |
| 96 | +DS_DIRMGRDN=cn=Directory Manager |
| 97 | +DS_DIRMGRPASSWD=passw0rd" > conf.file && java -jar openam-configurator-tool*.jar --file conf.file' |
| 98 | +``` |
| 99 | + |
| 100 | +Add the certificate you downloaded earlier for the Yandex Cloud application you created to the OpenAM keystore. |
| 101 | + |
| 102 | +To do this, copy the certificate to the container. |
| 103 | + |
| 104 | +```bash |
| 105 | +docker cp openam-saml.cer openam:/usr/openam/config/openam |
| 106 | +``` |
| 107 | + |
| 108 | +The password for the keystore is located in the file `/usr/openam/config/openam/.storepass`. |
| 109 | + |
| 110 | +You can view it using the command |
| 111 | + |
| 112 | +```bash |
| 113 | +docker exec openam bash -c 'cat /usr/openam/config/openam/.storepass' |
| 114 | +``` |
| 115 | + |
| 116 | +Import the certificate into the OpenAM keystore |
| 117 | + |
| 118 | +```bash |
| 119 | +docker exec -it -w '/usr/openam/config/openam' openam bash -c 'keytool -importcert \ |
| 120 | + -alias "yandex-cloud-cert" \ |
| 121 | + -keystore keystore.jceks \ |
| 122 | + -storetype JCEKS \ |
| 123 | + -file openam-saml.cer' |
| 124 | +``` |
| 125 | + |
| 126 | +Enter the password and confirm that the certificate is trusted. |
| 127 | + |
| 128 | +Restart the OpenAM container. |
| 129 | + |
| 130 | +```bash |
| 131 | +docker restart openam |
| 132 | +``` |
| 133 | + |
| 134 | +### Realm Configuration |
| 135 | + |
| 136 | +Log in to the administrator console at [http://localhost:8080/openam](http://localhost:8080/openam/). Use the login `amadmin` and password `passw0rd` respectively. |
| 137 | + |
| 138 | +1. Open **Top Level Realm.** |
| 139 | +2. In the menu on the left, go to **Authentication → Settings**. |
| 140 | +3. Go to the **User Profile** tab and set the **User Profile** setting to **Ignore**. |
| 141 | +4. Click **Save Changes.** |
| 142 | + |
| 143 | + 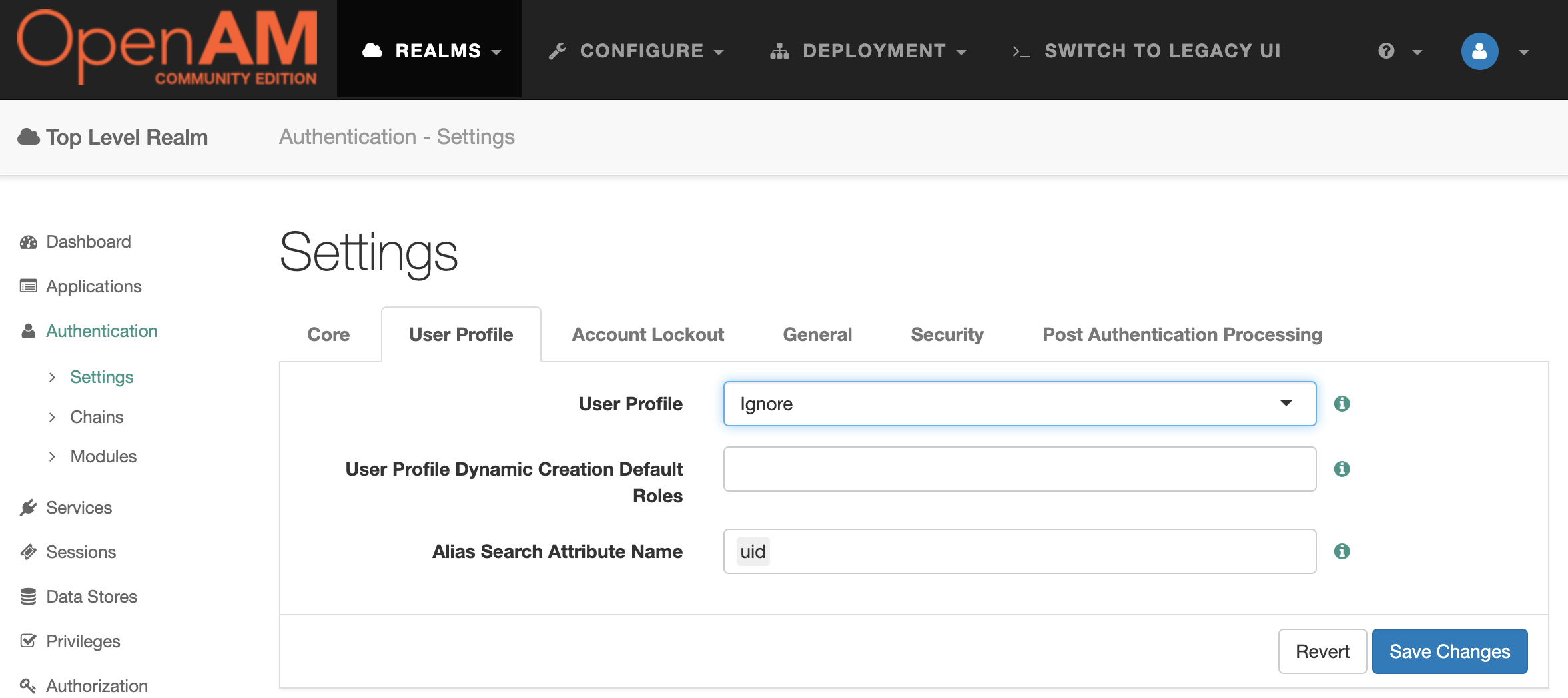 |
| 144 | + |
| 145 | + |
| 146 | +### Configuring the Service Provider |
| 147 | + |
| 148 | +1. In the administrator console, select **Top Level Realm** |
| 149 | +2. On the **Common Tasks** panel, click **Configure SAMLv2 Provider** |
| 150 | +3. Next, click **Create Hosted Service Provider** |
| 151 | +4. Enter any name for **Circle Of Trust**, for example, `openam-yandex`, and click **Configure.** |
| 152 | + |
| 153 | + 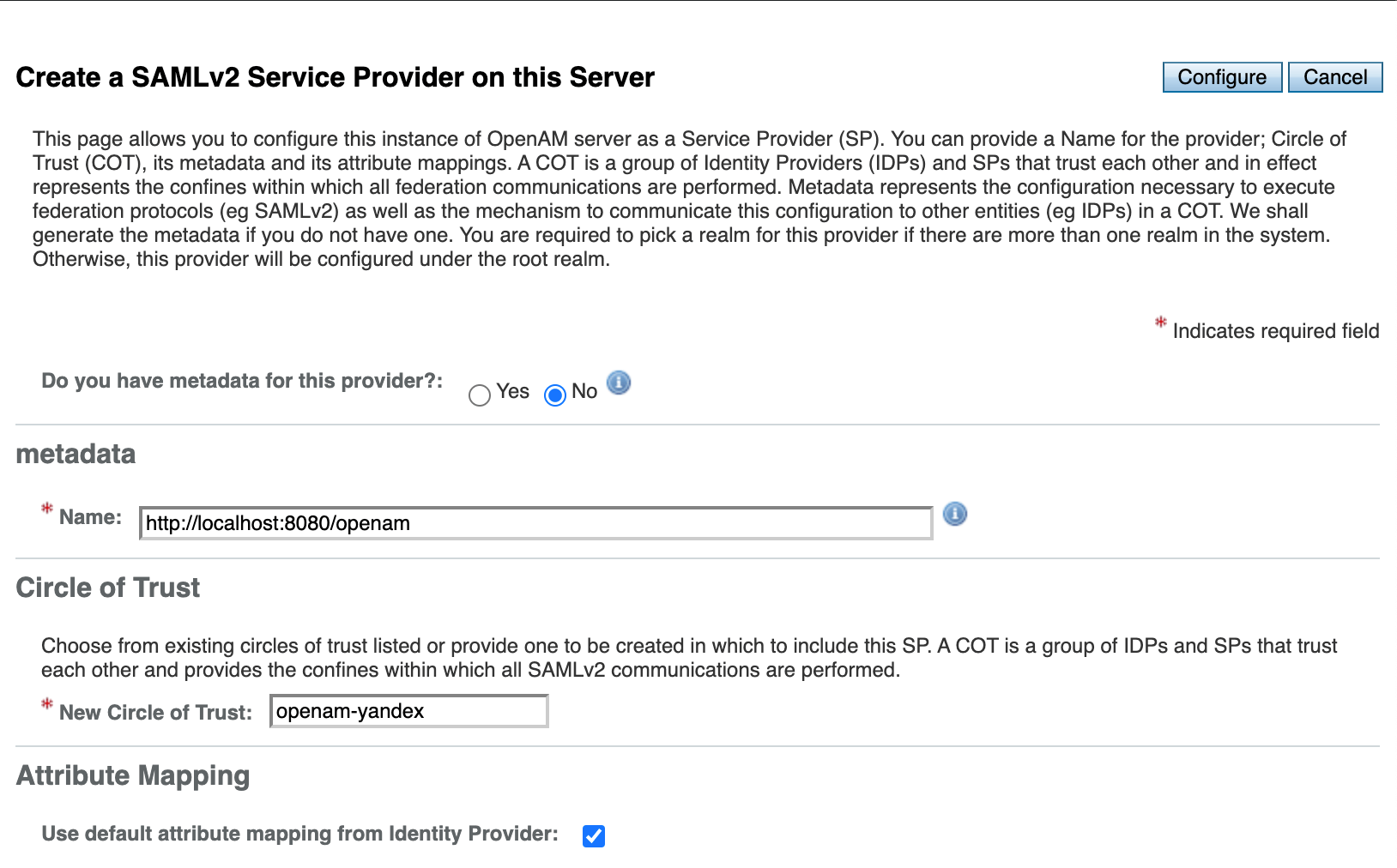 |
| 154 | + |
| 155 | +5. OpenAM will prompt you to configure Remote Identity Provider. Click Yes. |
| 156 | + |
| 157 | + 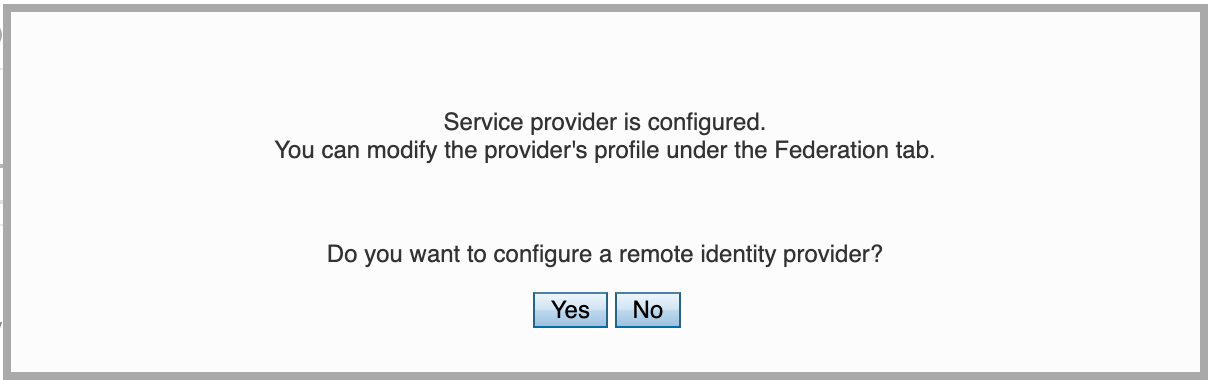 |
| 158 | + |
| 159 | +### Configuring the Identity Provider |
| 160 | + |
| 161 | +1. Enter the metadata URL from the Yandex application settings and click Configure. |
| 162 | + |
| 163 | + 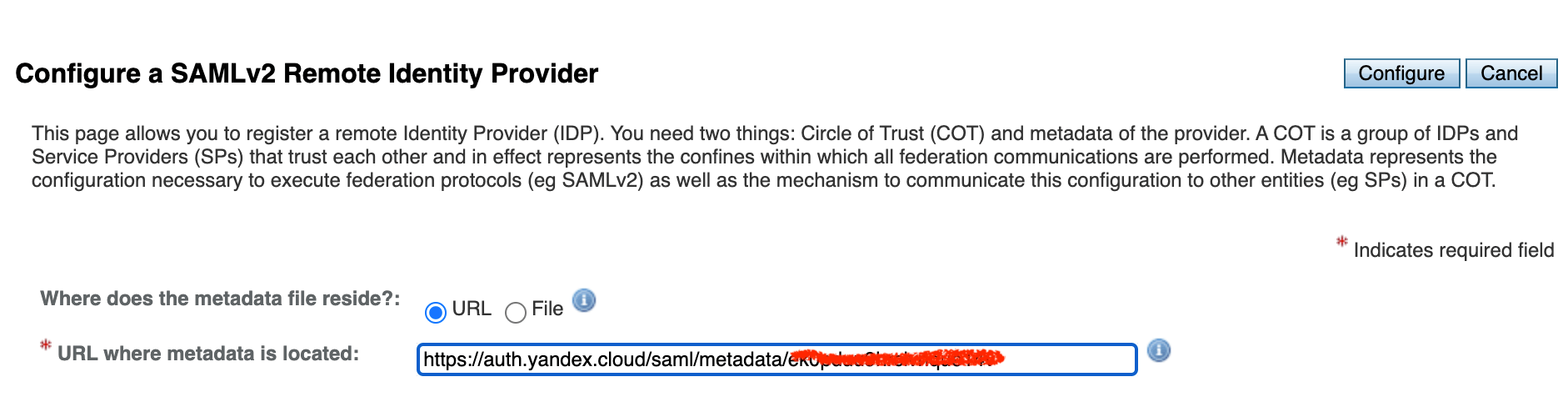 |
| 164 | + |
| 165 | +2. Reopen Top Level Realm |
| 166 | +3. In the left pane, navigate to **Applications → SAML 2.0** |
| 167 | +4. In the **Entity Providers** list, open **http://localhost:8080/openam** |
| 168 | +5. On the **Assertion Content** tab, find the **Authentication Context** section |
| 169 | +6. Set the **Default Authentication Context** setting to `Password` |
| 170 | +7. In the **Authentication Context** table, select the values `Password` and `Password Protected Password` |
| 171 | +8. Click **Save** |
| 172 | +9. Go to the **Assertion Processing** tab |
| 173 | +10. In the **Attribute Mapper** section, set the **Attribute Map** setting to `emailaddress=mail` |
| 174 | +11. In the **Auto Federation** section, select the Enabled checkbox and set Attribute to `emailaddress`. |
| 175 | +12. Click **Save**. |
| 176 | +13. Go to the **Services** tab. |
| 177 | +14. In the **SP Service Attributes** section, in the **Assertion Consumer Service** table, select `HTTP-POST`. |
| 178 | + |
| 179 | + 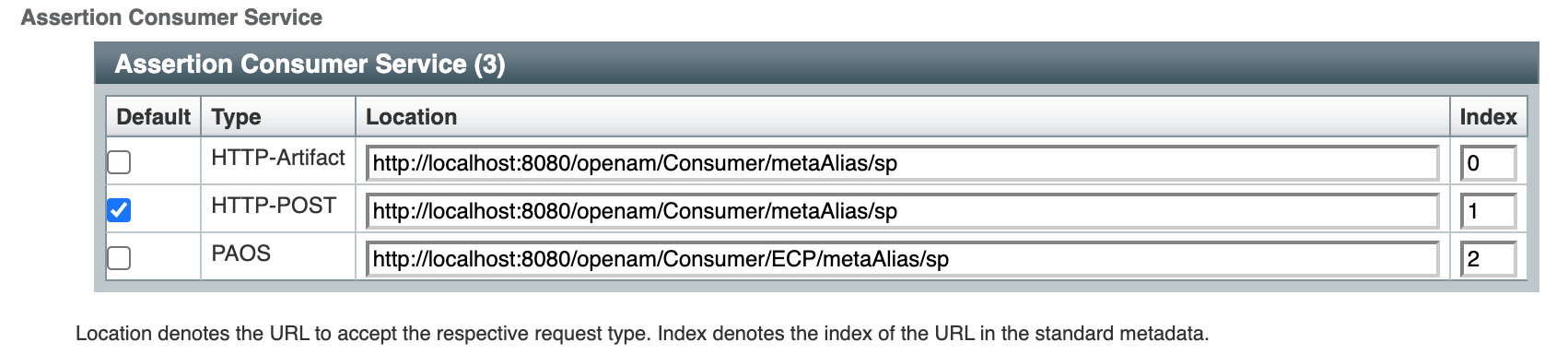 |
| 180 | + |
| 181 | +15. Click **Save** |
| 182 | + |
| 183 | +## Verifying the solution |
| 184 | + |
| 185 | +1. Exit the admin console, Yandex console, or open your browser in incognito mode. |
| 186 | +2. Follow the authentication link: [http://localhost:8080/openam/spssoinit?metaAlias=/sp&idpEntityID=https%3A%2F%2Fauth.yandex.cloud%2Fsaml%2Fek0pduu9hrclvnque14v&RelayState=http%3A%2F%2Flocalhost%3A8080%2Fopenam](http://localhost:8080/openam/spssoinit?metaAlias=/sp&idpEntityID=https%3A%2F%2Fauth.yandex.cloud%2Fsaml%2Fek0pduu9hrclvnque14v&RelayState=http%3A%2F%2Flocalhost%3A8080%2Fopenam) |
| 187 | +3. The Yandex Cloud authentication window will open. |
| 188 | +4. In the email field, enter your user ID: `[email protected]` and click → |
| 189 | +5. In the password field, enter the corresponding password for your account |
| 190 | +6. Click → |
| 191 | + |
| 192 | + 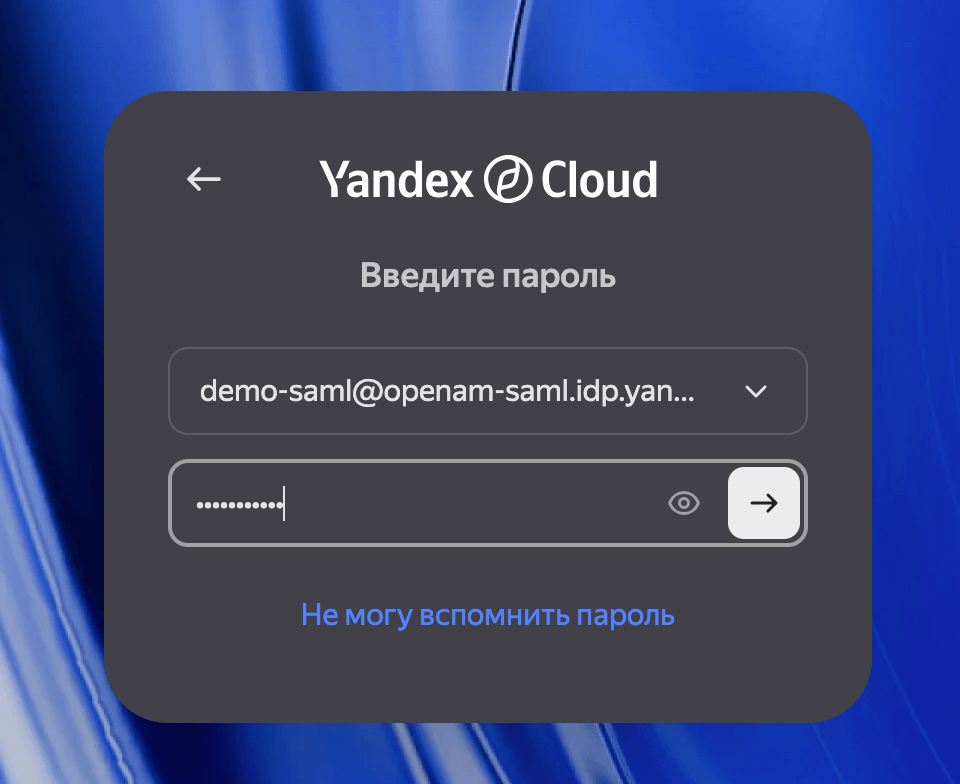 |
| 193 | + |
| 194 | +7. After successful authentication, you will be redirected to the OpenAM console with your Yandex Cloud credentials. |
| 195 | + |
| 196 | + 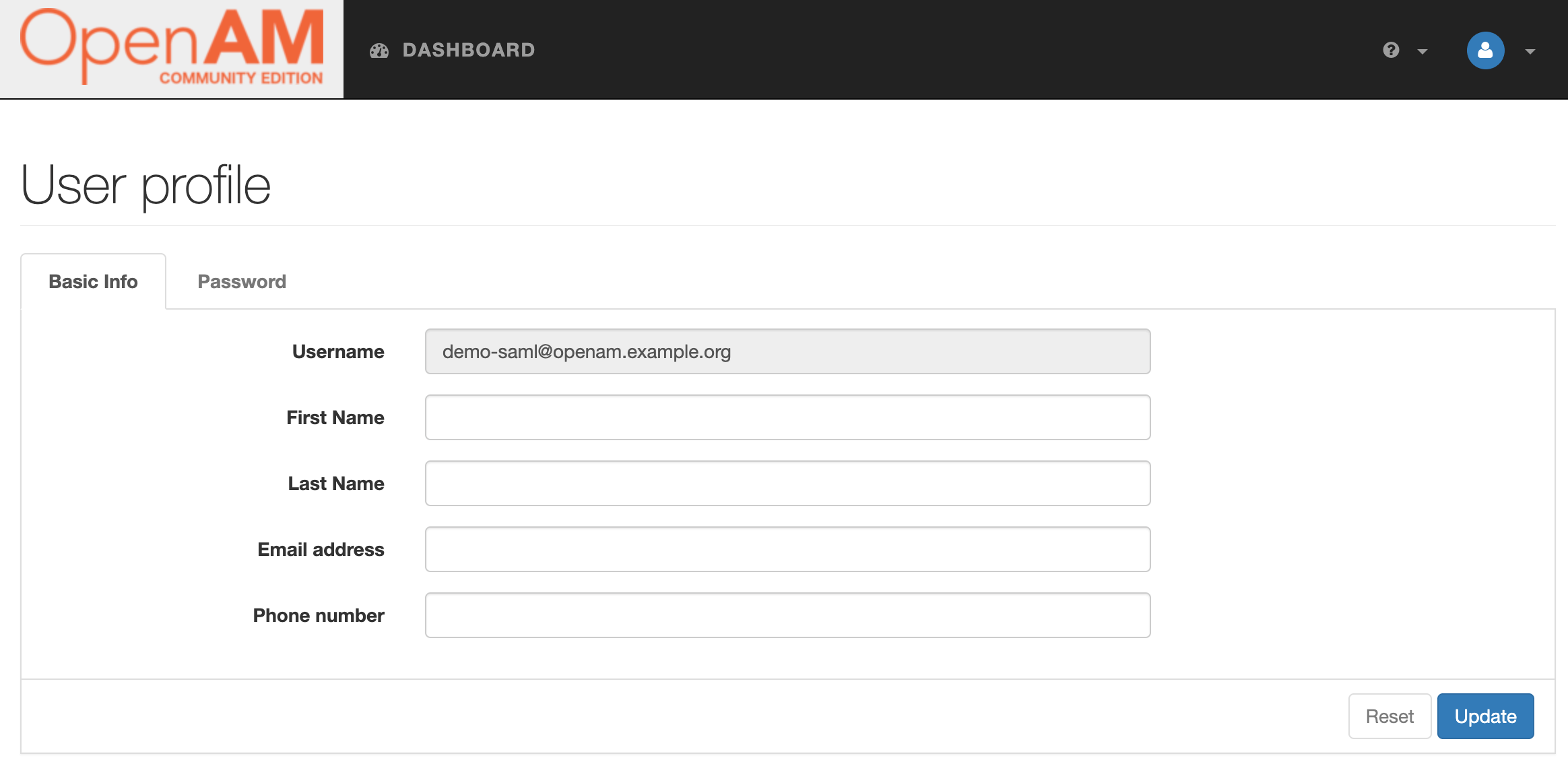 |
| 197 | + |
| 198 | +## What's next |
| 199 | + |
| 200 | +For production use, OpenAM must be deployed using a secure SSL connection, for example on a host and using an FQDN, such as https://openam.example.org/openam. |
| 201 | + |
| 202 | +Next, you can use the OpenIG authorization gateway to set up single sign-on (SSO) for your applications. |
| 203 | + |
| 204 | +For more details on configuring OpenAM and OpenIG, please refer to the documentation at [https://doc.openidentityplatform.org/openam](https://doc.openidentityplatform.org/openam) and [https://doc.openidentityplatform.org/openig](https://doc.openidentityplatform.org/openig). |
0 commit comments