Using AzureAD JWT Access Tokens To Access OrchardCore API #10632
-
|
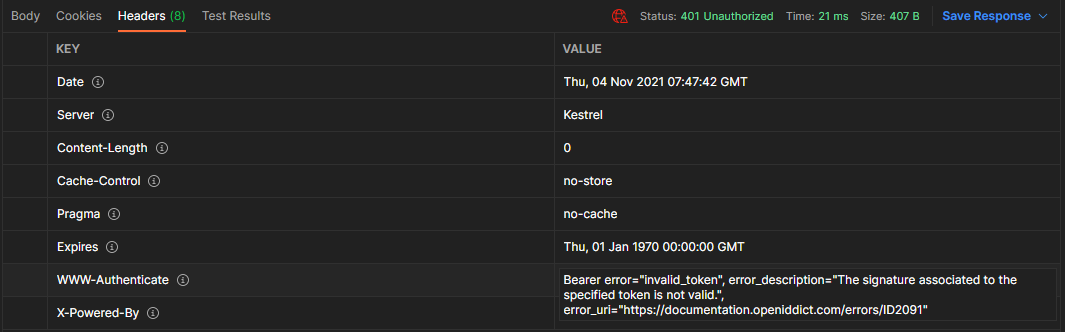
I have successfully setup AzureAD authentication on an OC tenant following the guide in the documentation. I can use an AzureAD account from my organization (belonging to a security group mapped to the Administrator role) to login to the admin site without prior registration. My question is how would I go about using JWT access tokens generated from the same AzureAD account directly to access the built-in OC API endpoints (such as /api/content/{contentItemId})? I have successfully granted API access before using the same OC tenant as the OpenId Server (by enabling the associated features) and registering an application in the same tenant. Essentially, I would like to do the same but using AzureAD as the issuer of the JWT access token. I have tried enabling the OpenId Validation feature and adding the AzureAD sts URL as authority (https://sts.windows.net/{tenantId}/) and the App ID registered in AzureAD as the Audience value. When trying to access the /api/content/{contentItemId} endpoint from the OC tenant passing in the JWT token obtained from AzureAD, I get the following error response: I'm not sure if this is a misconfiguration on my end (maybe with reading the signing key certificate?) or if the scenario is not possible / incorrect. Would appreciate help with the matter. Thanks! |
Beta Was this translation helpful? Give feedback.
Replies: 1 comment
-
|
Was able to solve this issue, adding the steps here for reference:
{
"name": "OpenIdValidationSettings",
"Audience": "{App ID URI}",
"Authority": "https://sts.windows.net/{tenantId}/",
"DisableTokenTypeValidation": true
}
The issue above was caused by sending the wrong scope value. The request was generating tokens for the Microsoft Graph API instead of the AzureAD registration for the OC instance because the App ID URI was not yet generated. Access tokens for the AzureAD registration required the generated App ID URI and user impersonation scope to generate the correct tokens. |
Beta Was this translation helpful? Give feedback.
Was able to solve this issue, adding the steps here for reference:
AzureAD App Registration configuration (to be done after following the guide in the documentation)
{OC base URL}/signin-oidc)api://{client id})user_impersonationscope will be generatedOC configuration