diff --git a/docs-v2/pages/connected-accounts/api.mdx b/docs-v2/pages/connected-accounts/api.mdx
deleted file mode 100644
index af2808e0ae63a..0000000000000
--- a/docs-v2/pages/connected-accounts/api.mdx
+++ /dev/null
@@ -1,176 +0,0 @@
-import Callout from '@/components/Callout'
-import { Tabs } from 'nextra/components'
-
-# Accessing credentials via API
-
-When you [connect an account](/connected-accounts/#connecting-accounts), you can use its credentials in workflows, authorizing requests to any app. Pipedream manages the OAuth process for [OAuth apps](/connected-accounts/#oauth), ensuring you always have a fresh access token for requests.
-
-You can also access account credentials from the Pipedream API, using them in any other tool or app where you need auth.
-
-
-The credentials API is in beta
-
-Accessing credentials via API is in **beta**, and we're looking for feedback. Please [let us know](https://pipedream.com/support) how you're using it, what's not working, and what else you'd like to see.
-
-During the beta:
-
-- All API calls to `/v1/accounts/*` are free.
-- The API is subject to change.
-
-
-## Using the credentials API
-
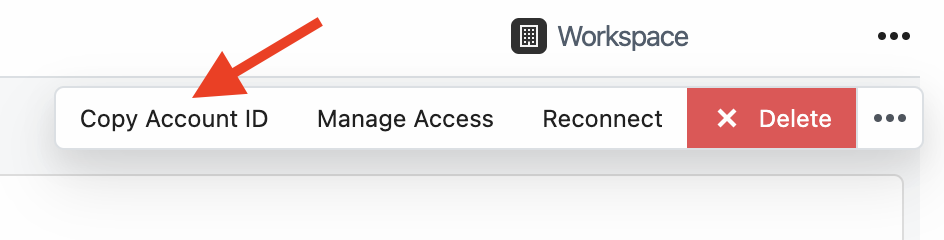
-1. [Connect your account](/connected-accounts/#connecting-a-new-account)
-2. On [https://pipedream.com/accounts](https://pipedream.com/accounts), find your account and click the `...` to the right of the account,
-3. **Copy Account ID**
-
-
-
-4. Make a request to the [**Get account credentials** endpoint](/rest-api/#get-account).
-
-
-
-
-```javascript
-export default defineComponent({
- props: {
- pipedream: {
- type: "app",
- app: "pipedream",
- },
- accountId: {
- type: "string",
- label: "Account ID",
- },
- },
- async run({ steps, $ }) {
- const url = `https://api.pipedream.com/v1/accounts/${this.accoundId}?include_credentials=1`;
- const headers = {
- "Content-Type": "application/json",
- Authorization: `Bearer ${this.pipedream.$auth.api_key}`,
- };
-
- const response = await fetch(url, {
- method: "GET",
- headers,
- });
- if (!response.ok) throw new Error(`API request failed: ${response.status}`);
- return await response.json();
- },
-});
-```
-
-
-
-
-```python
-import requests
-
-def handler(pd: "pipedream"):
- headers = {
- 'Content-Type': 'application/json',
- 'Authorization': f'Bearer {pd.inputs["pipedream"]["$auth"]["api_key"]}',
- };
- r = requests.get("https://api.pipedream.com/v1/accounts/?include_credentials=1", headers=headers)
- return r.json()
-```
-
-
-
-
-```bash
-curl 'https://api.pipedream.com/v1/accounts/?include_credentials=1' \
- -H "Authorization: Bearer "
-```
-
-
-
-
-```javascript
-const url = `https://api.pipedream.com/v1/accounts/?include_credentials=1`;
-const headers = {
- "Content-Type": "application/json",
- Authorization: `Bearer `,
-};
-
-const response = await fetch(url, {
- method: "GET",
- headers,
-});
-if (!response.ok) throw new Error(`API request failed: ${response.status}`);
-
-// Credentials are in data.credentials
-const { data } = await response.json();
-```
-
-:::
-
-
-
-
-```python
-import requests
-
-headers = {
- 'Content-Type': 'application/json',
- 'Authorization': f'Bearer ',
-};
-r = requests.get("https://api.pipedream.com/v1/accounts/?include_credentials=1", headers=headers)
-
-# Credentials are in data.data.credentials
-data = r.json()
-```
-
-
-
-
-5. It's not necessary to fetch credentials on every request to your app. You should [cache credentials in your own DB](#caching-credentials), refreshing them only when necessary.
-
-## Caching credentials
-
-Access tokens for most OAuth services are valid for at least one hour. Some tokens have a longer expiry, and some are static until rotated or revoked.
-
-The response from `/v1/accounts/:id?include_credentials=1` contains an `expires_at` field, an ISO timestamp representing the expiry of the current token. This maps to the `expires_at` timestamp in the OAuth access token response. While tokens are not guaranteed to be valid until expiry, they are for most APIs in practice. We recommend caching credentials with the `expires_at` timestamp, using the tokens until expiry, retrieving new credentials only after expiry or when you encounter auth errors when making your API request.
-
-If `expires_at` is missing or `null`, the credentials do not expire.
-
-```javascript
-/*** PSEUDO-CODE — use this as a guide ***/
-
-// Fetch the most-recent token and expiry from cache / DB
-const cache = Cache();
-const { oauth_access_token, expires_at } = await cache.get("credentials");
-
-// Only fetch new tokens when expired
-let token = oauth_access_token;
-if (expires_at && new Date(expires_at) < new Date()) {
- const url = `https://api.pipedream.com/v1/accounts/?include_credentials=1`;
- const headers = {
- "Content-Type": "application/json",
- Authorization: `Bearer `,
- };
-
- const response = await fetch(url, {
- method: "GET",
- headers,
- });
- if (!response.ok)
- throw new Error(`Unable to fetch token: ${response.status}`);
-
- const { data } = await response.json();
- const newToken = data?.credentials?.oauth_access_token;
- if (!newToken) throw new Error("No access token");
- token = newToken;
-}
-
-// Use `token` in API requests. Handle credentials errors and
-// fetch new credentials from Pipedream as necessary
-```
-
-Since these credentials are sensitive, you should encrypt them in the DB or data store you're using, decrypting them only at runtime when authorizing API requests.
-
-## Security
-
-[See our security docs](/privacy-and-security/#third-party-oauth-grants-api-keys-and-environment-variables) for details on how Pipedream secures your credentials.
-
-Connected accounts are private by default. You can [manage access control](/connected-accounts/#managing-access) to expose them to other members of your workspace.
diff --git a/docs-v2/pages/connected-accounts/index.mdx b/docs-v2/pages/connected-accounts/index.mdx
index a3f6c814259d4..714b13d61144d 100644
--- a/docs-v2/pages/connected-accounts/index.mdx
+++ b/docs-v2/pages/connected-accounts/index.mdx
@@ -9,7 +9,6 @@ Pipedream provides native integrations for [{process.env.PUBLIC_APPS}+ APIs](htt
- [Link that account to any step of a workflow](#connecting-accounts), using the associated credentials to make API requests to any service.
- [Manage permissions](#managing-connected-accounts), limiting access to sensitive accounts
-- [Access credentials via API](#accessing-credentials-via-api), letting you build services anywhere and use Pipedream to handle auth
Pipedream handles OAuth for you, ensuring you always have a fresh access token to authorize requests, and [credentials are tightly-secured](/privacy-and-security/#third-party-oauth-grants-api-keys-and-environment-variables).
@@ -39,6 +38,10 @@ For example, if you add a new connected account for **Sendgrid**, you'll be aske
## Connecting accounts
+
+This section discusses connecting **your own account** within the Pipedream UI. If you're looking to use the connected accounts for your customers, check out the [Connect docs](/connect).
+
+
### From an action
Prebuilt actions that connect to a specific service require you connect your account for that service before you run your workflow. Click the **Connect [APP]** button to get started.
diff --git a/docs-v2/pages/rest-api/index.mdx b/docs-v2/pages/rest-api/index.mdx
index 4141edad1e8b6..efdf6723b0bf4 100644
--- a/docs-v2/pages/rest-api/index.mdx
+++ b/docs-v2/pages/rest-api/index.mdx
@@ -193,12 +193,6 @@ The ID of the custom [OAuth app](/connect/quickstart#create-a-pipedream-oauth-cl
---
-`external_user_id` **string** (_optional_)
-
-[The external user ID](/connect/api/#external-users) in your system that you want to retrieve accounts for.
-
----
-
`include_credentials` **boolean** (_optional_)
Pass `include_credentials=true` as a query-string parameter to include the account credentials in the response
@@ -233,7 +227,7 @@ curl 'https://api.pipedream.com/v1/accounts' \
### Get account
-By default, this route returns metadata for a specific connected account. Set `include_credentials=true` to return credentials that you can use in any app where you need auth. [See this guide](/connected-accounts/api/) to learn more.
+By default, this route returns metadata for a specific connected account. Set `include_credentials=true` to return credentials that you can use in any app where you need the actual credentials (API key or OAuth access token for example).
#### Endpoint
diff --git a/docs-v2/vercel.json b/docs-v2/vercel.json
index ba236fcbf937b..47a7da8e3ed6f 100644
--- a/docs-v2/vercel.json
+++ b/docs-v2/vercel.json
@@ -277,6 +277,10 @@
{
"source": "/docs/workflows/networking",
"destination": "/docs/databases#connecting-to-restricted-databases"
+ },
+ {
+ "source": "/docs/connected-accounts/api",
+ "destination": "/docs/connect/api#accounts"
}
]
}