Security Onion 2.3.210 WinLogBeat's agent traffic traversing NAT #10083
Replies: 4 comments 2 replies
-
|
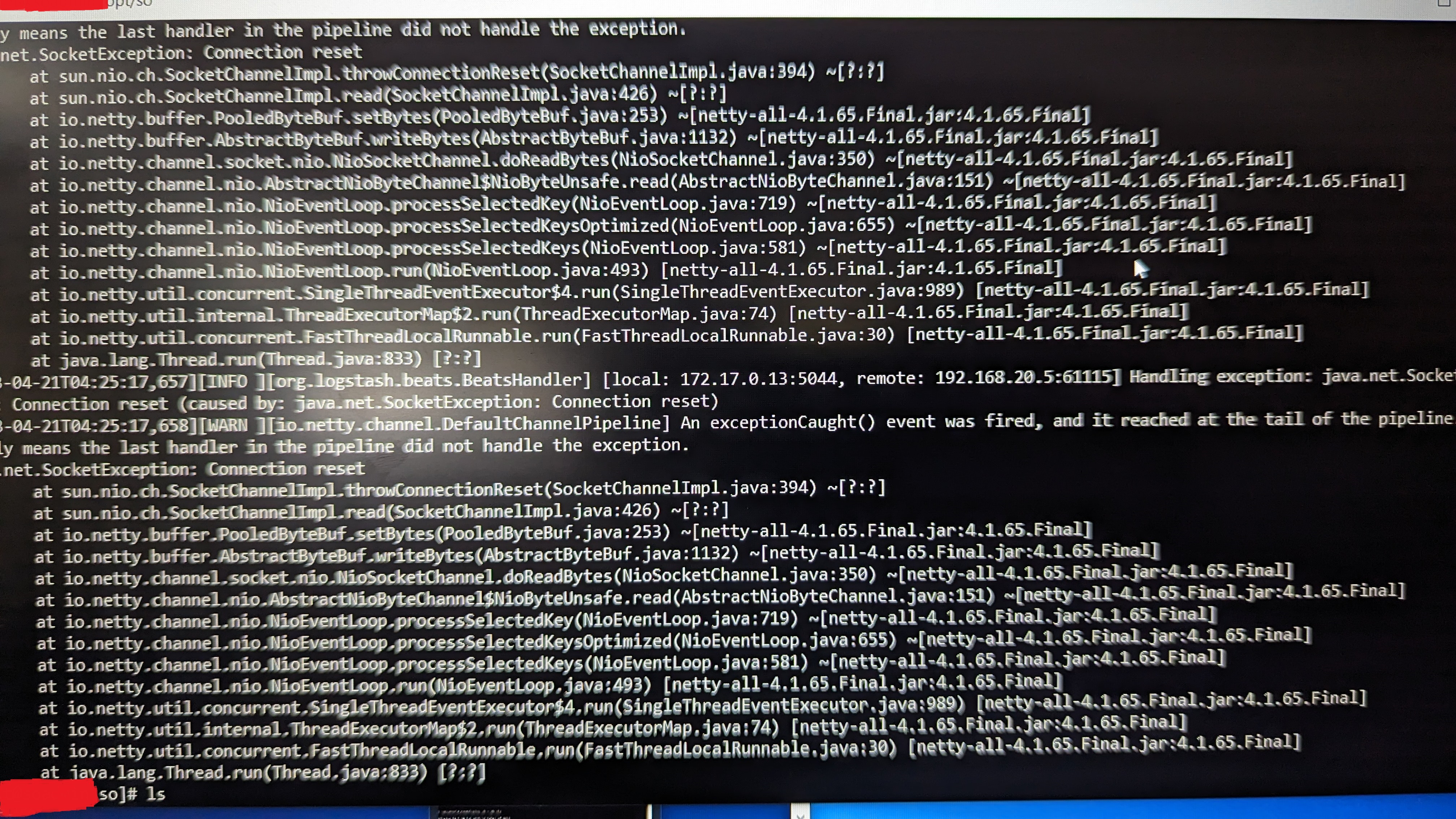
Is there anything useful in the Logstash logs on the standalone (/opt/so/logs/logstash/logstash.log) indicating a connection error or other misconfiguration? |
Beta Was this translation helpful? Give feedback.
-
|
bump? |
Beta Was this translation helpful? Give feedback.
-
|
bump? |
Beta Was this translation helpful? Give feedback.
-
|
This is a head-scratcher, for sure. What version of SO are you running? Is it the version of Winlogbeat from the SOC Downloads screen? Can you share your winlogbeat.yml file? |
Beta Was this translation helpful? Give feedback.
Uh oh!
There was an error while loading. Please reload this page.
Uh oh!
There was an error while loading. Please reload this page.
-
Good day,
I have been trying to setup Security Onion (SO) WinLogBeat agents, and Wazuh agents, with the PFSense firewall that is all hosted via ESXI. The problem I keep on having is that SO is not responding to the forwarded agent traffic, so the agent times out trying to reach the SO manager.
The network looks like the following:
External - [ Enterprise Network 192.168.0.0/24 ] - [ MS Windows 10 Pro : Workstation 192.168.0.4 ] --- [ MS Windows 2019 Server : 192.168.0.3 ] || [ PFSense : 192.168.0.2 (WAN) ] Internal -[ : 10.0.0.1 (LAN) ] [ SO : 10.0.0.2 ]External and Internal are vSwitches and port groups assigned to those networks and hosts. The SO configuration is setup in a standalone air-gapped config.
On the PFSense firewall I have tried the following:
Each of the NAT rules in PFSense automatically generate firewall allow rules. In addition for testing purposes I allowed all traffic from the the WAN to the LAN network and I have verified from the SO manager interface, via tcpdump, that SO is in fact receiving traffic from the PFSense. This was also checked via capturing traffic on PFSense.
When testing the PNAT configuration on both the Workstation and the Server, in the Enterprise Network, the IP set for the manager IP was 192.168.0.2:9200 for elasticsearch and 192.168.0.2:5044 for logstash. Do note that either configuration was tried separately (elasticsearch versus logstash). During this config the traffic was being forwarded as stated before. What was noticed via PFSense's state view was that all the sessions going from 192.168.0.3 to 10.0.0.2 were labelled SYN/WAIT meaning that the endpoint (SO) never responded.
When testing the SNAT configuration on both the Workstation and the Server, in the Enterprise Network, the IP set for the manager IP was 192.168.0.5:9200 for elasticsearch and 192.168.0.5:5044 for logstash. Do note that either configuration was tried separately (elasticsearch versus logstash). During this config the traffic was being forwarded as stated before. What was noticed via PFSense's state view was that all sessions going from 192.168.0.5 to 10.0.0.2 were labelled as FIN & TIME_WAIT meaning that the endpoint received traffic, and responded by closing the connection.
Also noting for the SNAT config that the traffic sniffed from the manager interface on SO included the HTTP data from WinLogBeats (from the Server) that varied in having it's Host header set to 192.168.0.5. This seemed to be part of the problem on why the traffic was not being sent back. But what is crazy is that not traffic was being sent back at all from Security Onion. SO seemed like it was just choosing to not respond.
Please note that IPtables on SO was updated to allow:
For both NAT configurations while testing the deployment of the Wazuh agent the same behavior occurred. What was even more crazy was that the OSSEC config manager window, after entering in the base64 encoded agent key, actually pulled the agent name and id from the SO server! But subsequently recorded in it's logs that the service couldn't reach the SO manager by timing out.
I'm at a loss for what to try now next to adding another interface to SO and hooking it up to the External vSwitch, which defeats the purpose of NAT'ing SO behind a firewall. I've read a lot of setup blogs for configurations for WinLogBeats, Wazuh and Sysmon. Watched the instructional videos on YouTube that Security Onion Solutions provides, even referenced the Security Onion book we've received and I just can't make it work.
Please also note that we use Velociraptor for the beginning portion of our IR and those agents work just fine with the PNAT config. I also am able to SSH into SO from the External network but can't reach the web interface.
Beta Was this translation helpful? Give feedback.
All reactions