Replies: 1 comment 4 replies
-
|
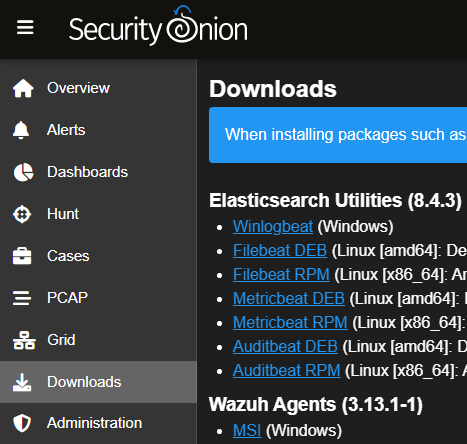
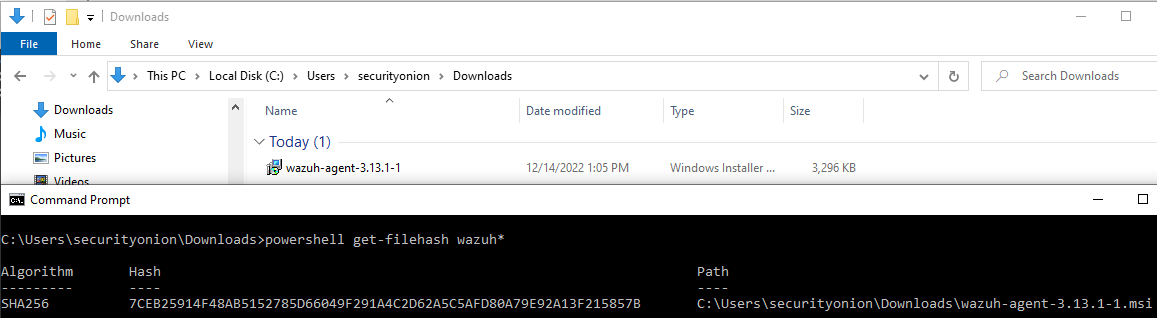
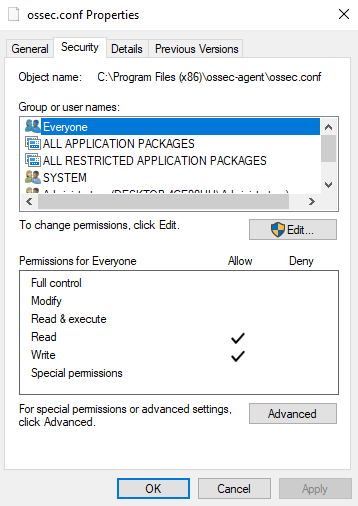
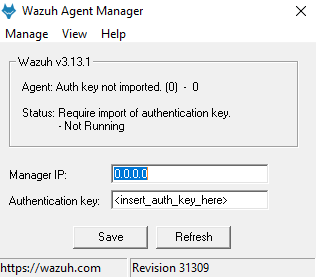
Hi @jakko10, We've tested this on a few different machines and here are our findings. We downloaded the Wazuh agent: We then installed the agent and verified that the permissions on ossec.conf allowed all users to write: We then ran the Wazuh Agent Manager: and configured the agent to connect to the Wazuh server. Saving the configuration locks down the permissions on ossec.conf: Can you confirm that saving the configuration locks down the permissions on ossec.conf for you? |
Beta Was this translation helpful? Give feedback.
4 replies
Sign up for free
to join this conversation on GitHub.
Already have an account?
Sign in to comment
Uh oh!
There was an error while loading. Please reload this page.
Uh oh!
There was an error while loading. Please reload this page.
-
Hi!
Looks like Security Onion still uses the old Wazuh agent version 3.13.1-1 that has an (in my personal opinion) critical level security hole in it.
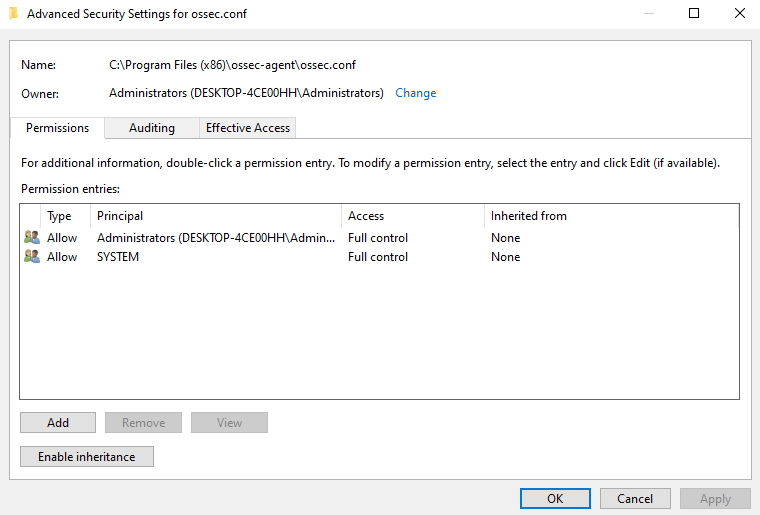
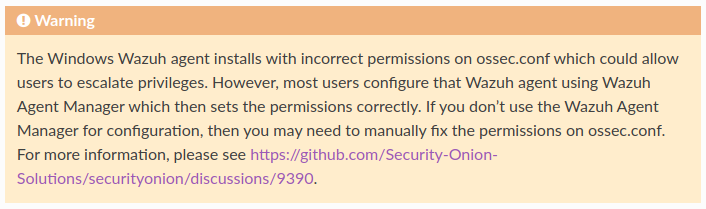
The ossec.conf file permissions are incorrect. The Everyone user group has read and write permissions. The latter is the critical one.
Due to this bug, any user who is not an administrator could easily elevate to administrator/system asses rights.
Why and how:
The why: Wazuh agent service rus as local system account.
The how: If one adds a script wodle to Wazuh agent conf (ossec.conf) the script will run in the system context and can do pretty much anything. After the next reboot, the script gets loaded and magic happens.
Beta Was this translation helpful? Give feedback.
All reactions