+ })
+Databricks Audit
+Analyze your organization's security practices to identify emerging threats and compliance risks.
+}) | [DarkOwl](https://www.darkowl.com/) | Automation integration: [DarkOwl](/docs/platform-services/automation-service/app-central/integrations/darkowl/) |
|
| [DarkOwl](https://www.darkowl.com/) | Automation integration: [DarkOwl](/docs/platform-services/automation-service/app-central/integrations/darkowl/) |
| }) | [Darktrace](https://darktrace.com/) | Automation integration: [Darktrace](/docs/platform-services/automation-service/app-central/integrations/darktrace/)
| [Darktrace](https://darktrace.com/) | Automation integration: [Darktrace](/docs/platform-services/automation-service/app-central/integrations/darktrace/) }) | [Datto](https://www.datto.com/) | Automated integration: [Datto RMM](/docs/platform-services/automation-service/app-central/integrations/datto-rmm/)
| [Datto](https://www.datto.com/) | Automated integration: [Datto RMM](/docs/platform-services/automation-service/app-central/integrations/datto-rmm/)  +
+### Security Overview
+
+The **Databricks Audit - Security Overview** dashboard provides targeted insights into key security events and potential risk exposures across your Databricks environment. It enables proactive detection of suspicious activity by visualizing failed API calls over time, authentication method usage, and API response codes that may indicate unauthorized access attempts or configuration issues.
+
+Security teams can easily track trends in failed authentications and API errors, investigate root causes, and identify patterns that signal emerging threats or compliance violations. The dashboard also includes a geographic overview of audit activities, highlighting events originating from embargoed or high-risk regions to help monitor potential data exfiltration or policy breaches.
+
+By consolidating these critical security indicators, including summaries of failed API attempts and geographic context, the dashboard empowers teams to rapidly investigate incidents, respond to evolving risks, and maintain strong security and compliance across all Databricks workspaces.
+
+### Security Overview
+
+The **Databricks Audit - Security Overview** dashboard provides targeted insights into key security events and potential risk exposures across your Databricks environment. It enables proactive detection of suspicious activity by visualizing failed API calls over time, authentication method usage, and API response codes that may indicate unauthorized access attempts or configuration issues.
+
+Security teams can easily track trends in failed authentications and API errors, investigate root causes, and identify patterns that signal emerging threats or compliance violations. The dashboard also includes a geographic overview of audit activities, highlighting events originating from embargoed or high-risk regions to help monitor potential data exfiltration or policy breaches.
+
+By consolidating these critical security indicators, including summaries of failed API attempts and geographic context, the dashboard empowers teams to rapidly investigate incidents, respond to evolving risks, and maintain strong security and compliance across all Databricks workspaces. 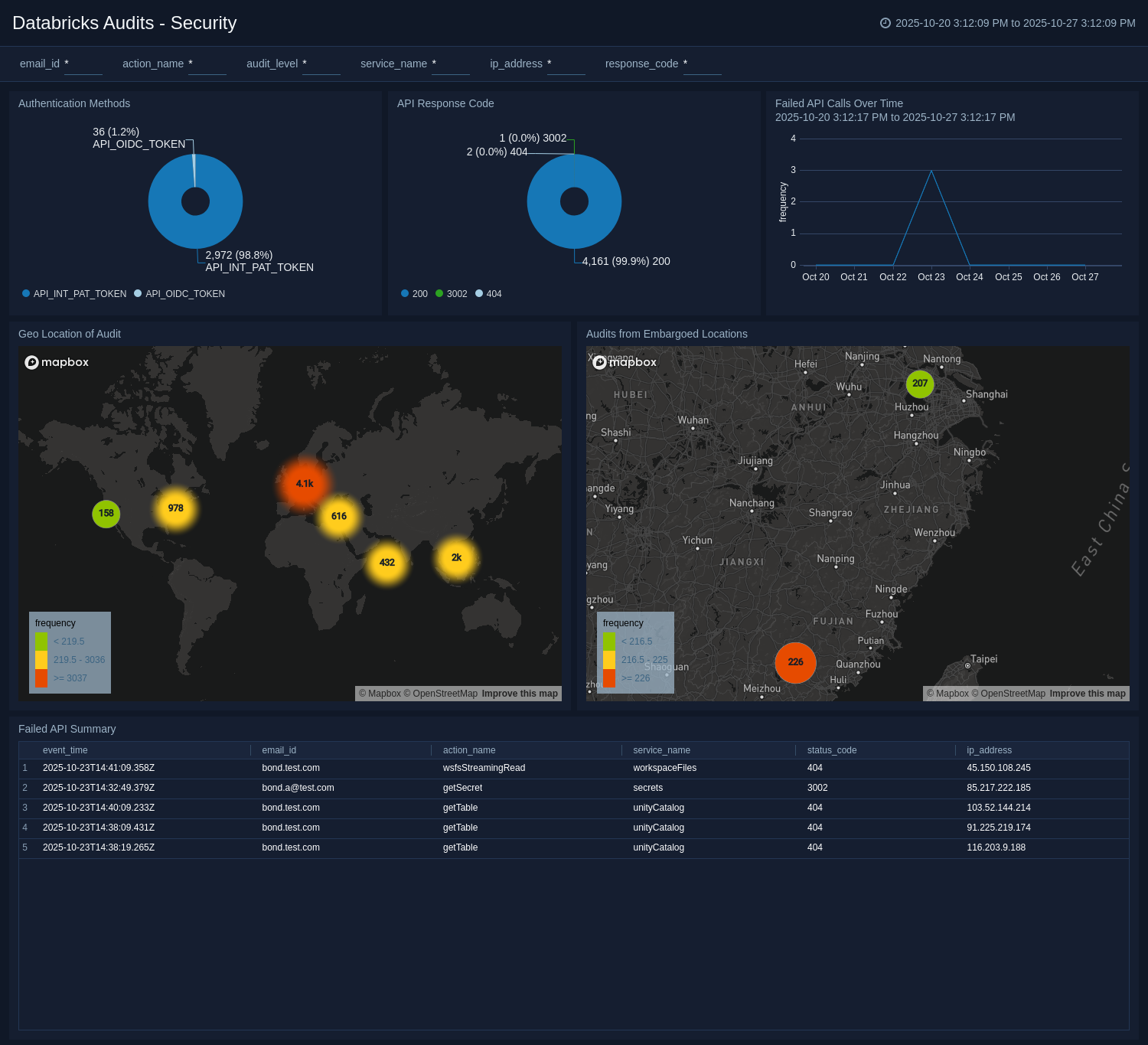 +
+## Create monitors for Databricks Audit app
+
+import CreateMonitors from '../../reuse/apps/create-monitors.md';
+
+
+
+## Create monitors for Databricks Audit app
+
+import CreateMonitors from '../../reuse/apps/create-monitors.md';
+
+Gather information about your organization's cybersecurity practices to strengthen security.
+Analyze your organization's security practices to identify emerging threats and compliance risks.
+