-
|
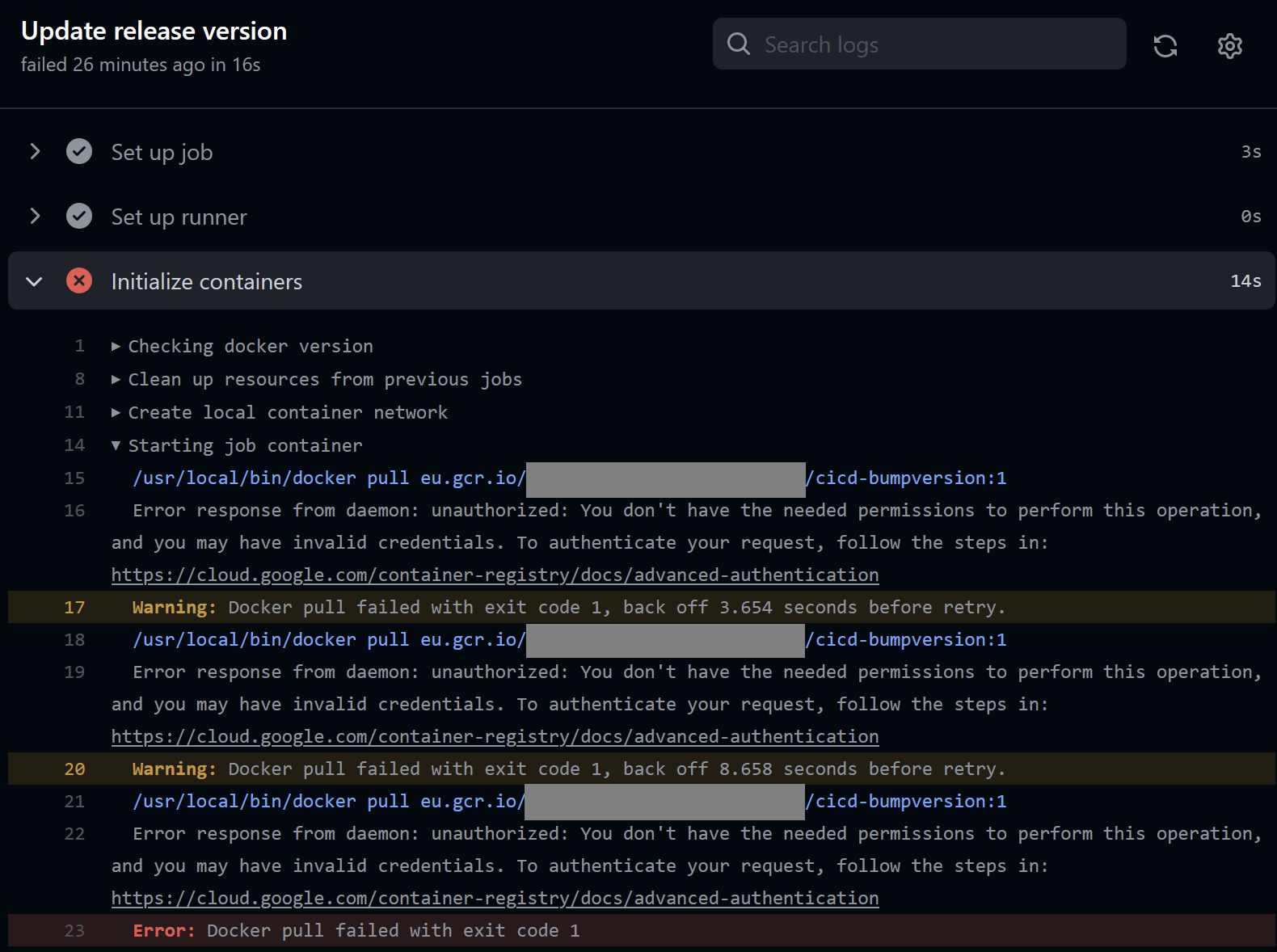
I'm trying to give my runner access to a private Docker registry implemented using Google Container Registry. I need to be able to pull images that are on this Registry server in order to use them for job containers used in my workflows. I'm running the actions runner controller on Google Kubernetes Engine and it's all working fine. IAM is assigned through Workload Identity. The problem: job containers that need images from private Docker registries only accept usernames and passwords (See: https://docs.github.com/en/actions/using-jobs/running-jobs-in-a-container). For Google Container Registry it's best practice to install the gcloud sdk and run the gcloud credential helper using I've set up a Has anyone worked on a problem similar to this? Ideally I would run I've already tried adding a postStart lifecycle hook to the runner pod spec that runs a bash script that simply runs the command, but that kills my runner right after startup with the following error: So I figured that I would have to wait for Docker to have retrieved its' certs, so I added a simple loop in the script that waits for Sadly that still gives the same error. Would love to hear if anyone has some suggestions for how to best tackle this problem or whether it's at all possible to solve! |
Beta Was this translation helpful? Give feedback.
Replies: 2 comments 4 replies
-
|
i created an internal composite action for this |
Beta Was this translation helpful? Give feedback.
-
|
For future reference, I got around to fixing this for myself, and my chosen solution was creating a custom actions runner image that has docker-credential-gcr preinstalled. Dockerfile dockerconfig.json By using this image all docker command invocations automatically pull access tokens from GCR when any of the GCR hostnames are referenced in the image registry name. Now assigning the proper Container Registry IAM roles to your service accounts is enough. |
Beta Was this translation helpful? Give feedback.
For future reference, I got around to fixing this for myself, and my chosen solution was creating a custom actions runner image that has docker-credential-gcr preinstalled.
Dockerfile