-
Notifications
You must be signed in to change notification settings - Fork 61
Examples
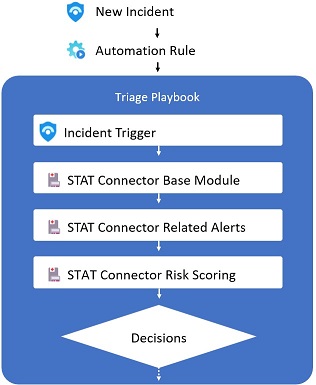
The Sample playbook is a Proof of Concept to demonstrate how STAT can be used to Triage an incident. This sample is not meant to be capable of triaging any type of incident; additional playbooks may need to be built using STAT to handle the unique requirements of different incident types.
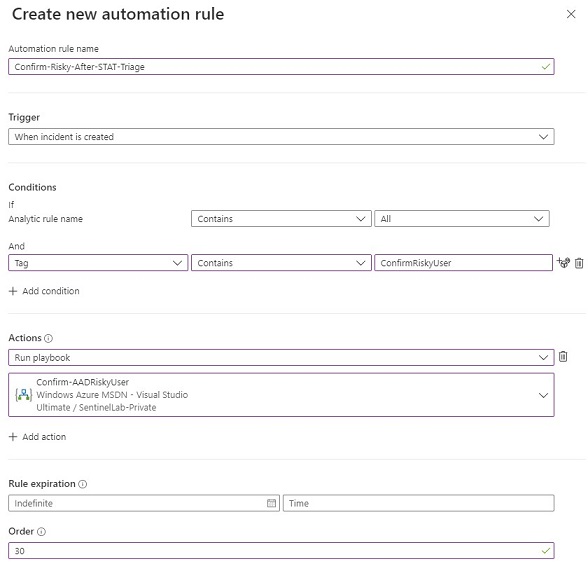
The Playbook starts on a Sentinel Incident creation rule trigger and then starts the triage process using STAT:
- The STAT Base Module is called using the STAT Connector to enrich and prepare the entity data for the STAT Solution
- In parallel, the AAD Risks Module, Related Alerts Module and Threat Intel Module are called
- The AAD Risks Module is configured to pass the Base Module response, and lookback 30 days in the Sentinel data for any MFA Fraud reports related to the entities in the triggering incident
- The Related Alerts Module is configured to pass the Base Module response and check for any Related Sentinel alerts based on matching Account, Host or IP entity data in the last 30 days
- The Threat Intel Module is configured to pass the Base module response and check for any Related Sentinel Threat Intelligence in the last 30 days based on matching Domain, FileHash, IP, and URL entity data
- The Scoring module is then executed using the inputs of the Base, AAD Risks, Related Alerts and Threat Intel modules to determine a risk score for the incident
- A Condition is then evaluated on the calculated risk score to determine if it is greater than or equal to 40
- If it is, the Incident severity is raised and a tag is added with the Triage result
- If not, the Incident severity is lowered and a tag is added with the Triage result
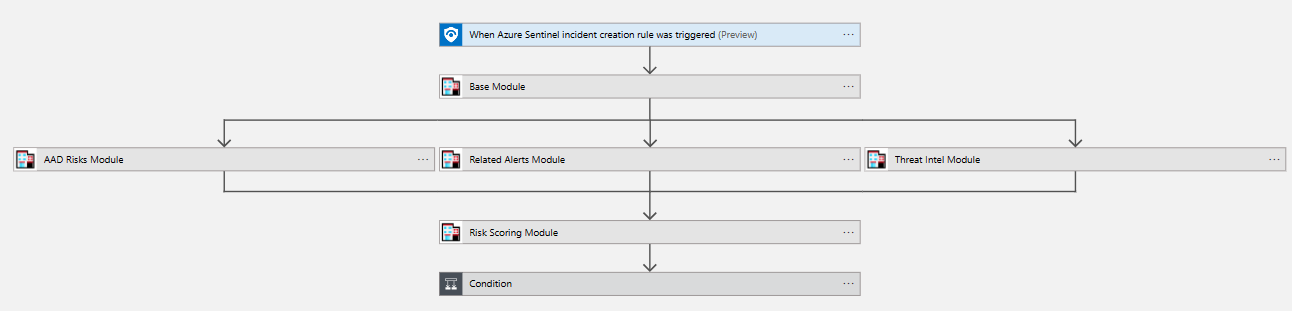
The sample playbook only makes use of a few of the STAT modules available to you. To add additional STAT modules to this, or other playbooks you can add additional actions. When adding a new action, select the Custom tab. Typically, you will see the Sentinel Triage AssistanT right away, but if you have other custom connectors and you cannot locate it, search for Sentinel Triage or STAT to narrow your results.
For this example let's assume you want to make a decision based on the related alerts to an incident. While the Related Alerts module will return information about the amount of alerts, the severity of the alerts and other properties influence the risk of the incident. Without a risk score, it is difficult to analyze these properties in automation. For example, if there are multiple related high risk alerts you may wish to handle that differently than if there are multiple low or information risk alerts.
Passing the Related Alerts Body through the risk scoring module will return a simple cumulative score based on the number of alerts and severity of each alert. So instead of applying multiple conditions based on the number of alerts and severity of alerts, you can evaluate a simple condition such as TotalScore > 20.
Note: While this is useful for a module like Related alerts on its own, the Risk Scoring module provides even greater value as it can combine the risk scores from other modules such as Threat Intel, Watchlist and KQL into a single score that can be easily evaluated.
Without the Risk Scoring Module a triage Logic app would look something like this:
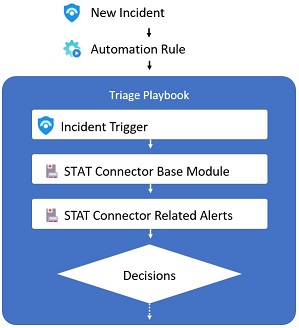
With risk scoring added:
Once you have used STAT to triage your incident and make a decision on the remediation actions you want to take, you may notice that STAT does not include any remediation actions. This is because many common remediation action Playbooks have already been built in the Sentinel Github repo. Since STAT is encouraging reusable automation, it didn't make sense at this time to incorporate remediation directly into STAT. However, that doesn't mean they can't work together.
Let's say you want to use the Confirm-AADRiskyUser playbook on an incident that STAT has triaged as a high risk. How can I run this playbook?
There's actually 3 common ways to accomplish this:
- Run Playbook Module
- Run Playbook API
- Incident Tags and Automation Rules
The easiest way to perform an automated remediation playbook based on a STAT triage is to use the Run Playbook STAT Module. This module allows for you to initiate another automation Playbook using an incident trigger on the incident you are triaging. More information on calling this module can be found here.
Microsoft Sentinel has an API endpoint that allows for the running of a playbook on an incident. In this approach, you would use that API endpoint to trigger the Confirm-AADRiskUser playbook
Incidents - Run Playbook API Documentation
The Run Playbook Module uses this API, but simplifies the inputs and authentication needed to call it.
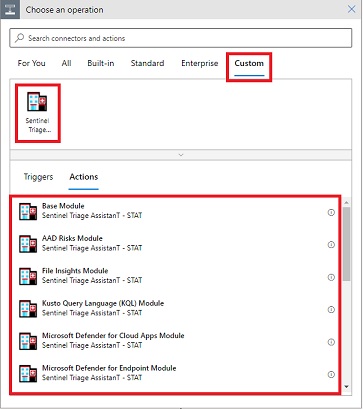
In this approach, you will configure the STAT playbook to tag the incident where you want to run the playbook, and an automation rule to execute the playbook if the Tag is present.
- In your STAT triage playbook add a Sentinel\Update Incident action to the part of your playbook where a high risk has been determined
- In that Update incident action, set a tag on the incident such as 'ConfirmRiskyUser'
- Create a new automation rule that runs after (higher Order #) the STAT triage Playbook which runs the Confirm-AADRiskyUser Playbook
- Set a Condition on the automation rule for Tag Contains 'ConfirmRiskyUser'
With this configuration the STAT playbook will run first, determine if the remediation action is needed, and then only if the tag has been added will the remediation action take place.