You signed in with another tab or window. Reload to refresh your session.You signed out in another tab or window. Reload to refresh your session.You switched accounts on another tab or window. Reload to refresh your session.Dismiss alert
Copy file name to clipboardExpand all lines: README.md
+3-3Lines changed: 3 additions & 3 deletions
Display the source diff
Display the rich diff
Original file line number
Diff line number
Diff line change
@@ -27,15 +27,15 @@ _CrowdSec is an open-source and participative security solution offering crowdso
27
27
28
28
[CrowdSec Security Engine](https://doc.crowdsec.net/docs/next/intro/) is an all-in-one [IDS/IPS](https://doc.crowdsec.net/docs/next/log_processor/intro) and [WAF](https://doc.crowdsec.net/docs/next/appsec/intro).
29
29
30
-
It detects bad behaviors by analyzing log sources and HTTP requests, and allows active remedation thanks to the [Remediation Components](https://doc.crowdsec.net/u/bouncers/intro).
30
+
It detects bad behaviors by analyzing log sources and HTTP requests, and allows active remediation thanks to the [Remediation Components](https://doc.crowdsec.net/u/bouncers/intro).
31
31
32
32
[Detection rules are available on our hub](https://hub.crowdsec.net) under MIT license.
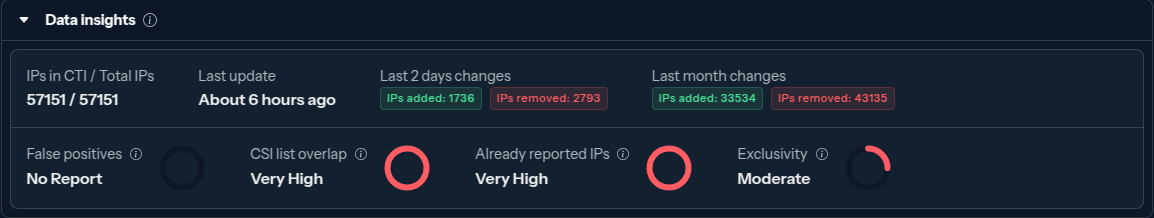
The "Community Blocklist" is a curated list of IP addresses identified as malicious by CrowdSec. The Security Engine proactively block the IP addresses of this blocklist, preventing malevolent IPs from reaching your systems.
38
+
The "Community Blocklist" is a curated list of IP addresses identified as malicious by CrowdSec. The Security Engine proactively blocks the IP addresses of this blocklist, preventing malevolent IPs from reaching your systems.
39
39
40
40
[](https://doc.crowdsec.net/docs/next/central_api/community_blocklist)
41
41
@@ -52,7 +52,7 @@ The "Community Blocklist" is a curated list of IP addresses identified as malici
52
52
53
53
## Outnumbering hackers all together
54
54
55
-
By sharing the threat they faced, all users are protecting each-others (hence the name Crowd-Security). Crowdsec is designed for modern infrastructures, with its "*Detect Here, Remedy There*" approach, letting you analyze logs coming from several sources in one place and block threats at various levels (applicative, system, infrastructural) of your stack.
55
+
By sharing the threat they faced, all users are protecting each other (hence the name Crowd-Security). Crowdsec is designed for modern infrastructures, with its "*Detect Here, Remedy There*" approach, letting you analyze logs coming from several sources in one place and block threats at various levels (applicative, system, infrastructural) of your stack.
56
56
57
57
CrowdSec ships by default with scenarios (brute force, port scan, web scan, etc.) adapted for most contexts, but you can easily extend it by picking more of them from the **[HUB](https://hub.crowdsec.net)**. It is also easy to adapt an existing one or create one yourself.
Copy file name to clipboardExpand all lines: SECURITY.md
+2-2Lines changed: 2 additions & 2 deletions
Display the source diff
Display the rich diff
Original file line number
Diff line number
Diff line change
@@ -7,9 +7,9 @@ This security policy applies to :
7
7
- Crowdsec Local API
8
8
- Crowdsec bouncers **developed and maintained** by the Crowdsec team [1]
9
9
10
-
Reports regarding developements of community members that are not part of the crowdsecurity organization will be thoroughly investigated nonetheless.
10
+
Reports regarding developments of community members that are not part of the crowdsecurity organization will be thoroughly investigated nonetheless.
11
11
12
-
[1] Projects developed and maintained by the Crowdsec team are under the **crowdsecurity** github organization. Bouncers developed by community members that are not part of the Crowdsec organization are explictely excluded.
12
+
[1] Projects developed and maintained by the Crowdsec team are under the **crowdsecurity** github organization. Bouncers developed by community members that are not part of the Crowdsec organization are explicitly excluded.
Copy file name to clipboardExpand all lines: test/bats/crowdsec-acquisition.bats
+4-4Lines changed: 4 additions & 4 deletions
Original file line number
Diff line number
Diff line change
@@ -24,7 +24,7 @@ teardown() {
24
24
25
25
#----------
26
26
27
-
@test "malformed acqusition file" {
27
+
@test "malformed acquisition file" {
28
28
cat >"$ACQUIS_DIR/file.yaml"<<-EOT
29
29
filename:
30
30
- /path/to/file.log
@@ -36,14 +36,14 @@ teardown() {
36
36
assert_stderr --partial "crowdsec init: while loading acquisition config: configuring datasource of type file from $ACQUIS_DIR/file.yaml (position 0): cannot parse FileAcquisition configuration: [2:1] cannot unmarshal []interface {} into Go struct field Configuration.Filename of type string"
0 commit comments