|
| 1 | ++++ |
| 2 | +title = "BackendTLSPolicy" |
| 3 | ++++ |
| 4 | + |
| 5 | + |
| 6 | + The `BackendTLSPolicy` resource is GA and has been part of the Standard |
| 7 | + Channel since `v1.4.0`. For more information on release channels, refer |
| 8 | + to our [versioning guide](https://gateway-api.sigs.k8s.io/concepts/versioning). |
| 9 | + |
| 10 | +[BackendTLSPolicy][backendtlspolicy] is a Gateway API type for specifying the TLS configuration |
| 11 | +of the connection from the Gateway to a backend pod/s via the Service API object. |
| 12 | + |
| 13 | +## Background |
| 14 | + |
| 15 | +`BackendTLSPolicy` specifically addresses the configuration of TLS in order to convey HTTPS from the Gateway |
| 16 | +dataplane to the backend. This is referred to as "backend TLS termination" and enables the Gateway to know |
| 17 | +how to connect to a backend pod that has its own certificate. |
| 18 | + |
| 19 | +While there are other API objects provided for TLS to be configured for **passthrough** and **edge** termination, |
| 20 | +this API object allows users to specifically configure **backend** TLS termination. For more information on TLS |
| 21 | +configuration in Gateway API, see [TLS Configuration](https://gateway-api.sigs.k8s.io/guides/tls). |
| 22 | + |
| 23 | +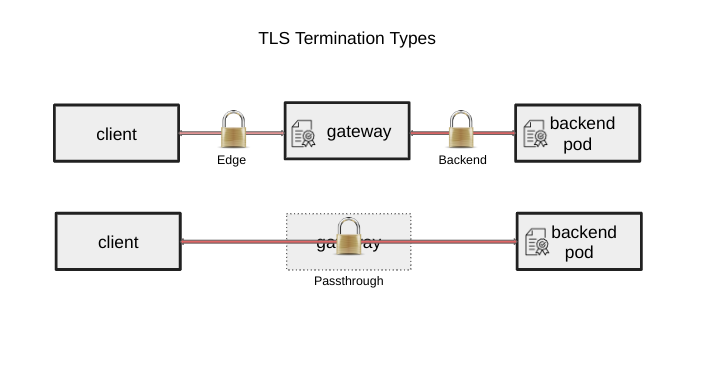 |
| 24 | + |
| 25 | +BackendTLSPolicy is a Direct [PolicyAttachment](https://gateway-api.sigs.k8s.io/reference/policy-attachment) without defaults or overrides, |
| 26 | +applied to a Service that accesses a backend, where the BackendTLSPolicy resides in the same namespace as the |
| 27 | +Service to which it is applied. The BackendTLSPolicy and the Service must reside in the same namespace in order |
| 28 | +to prevent the complications involved with sharing trust across namespace boundaries. |
| 29 | + |
| 30 | +All Gateway API Routes that point to a referenced Service should respect a configured BackendTLSPolicy. |
| 31 | + |
| 32 | +## Spec |
| 33 | + |
| 34 | +The specification of a [BackendTLSPolicy][backendtlspolicy] consists of: |
| 35 | + |
| 36 | +- [TargetRefs][targetRefs] - Defines the targeted API object of the policy. Only Service is allowed. |
| 37 | +- [Validation][validation] - Defines the configuration for TLS, including hostname, CACertificateRefs, and |
| 38 | +WellKnownCACertificates. |
| 39 | +- [Hostname][hostname] - Defines the Server Name Indication (SNI) that the Gateway uses to connect to the backend. |
| 40 | +- [SubjectAltNames][subjectAltNames] - Specifies one or more Subject Alternative Names that the backend certificate must match. When specified, the certificate must have at least one matching SAN. This field enables separation between SNI (hostname) and certificate identity validation. A maximum of 5 SANs are allowed. |
| 41 | +- [CACertificateRefs][caCertificateRefs] - Defines one or more references to objects that contain PEM-encoded TLS certificates, |
| 42 | +which are used to establish a TLS handshake between the Gateway and backend Pod. Either CACertificateRefs or |
| 43 | +WellKnownCACertificates may be specified, but not both. |
| 44 | +- [WellKnownCACertificates][wellKnownCACertificates] - Specifies whether system CA certificates may be used in the TLS |
| 45 | +handshake between the Gateway and backend Pod. Either CACertificateRefs or WellKnownCACertificates may be specified, but not both. |
| 46 | +- [Options][options] - A map of key/value pairs enabling extended TLS configuration for implementations that choose to provide support. Check your implementation's documentation for details. |
| 47 | + |
| 48 | +The following chart outlines the object definitions and relationship: |
| 49 | +```mermaid |
| 50 | +flowchart LR |
| 51 | + backendTLSPolicy[["<b>backendTLSPolicy</b> <hr><align=left>BackendTLSPolicySpec: spec<br>PolicyStatus: status</align>"]] |
| 52 | + spec[["<b>spec</b><hr>PolicyTargetReferenceWithSectionName: targetRefs <br> BackendTLSPolicyValidation: tls"]] |
| 53 | + status[["<b>status</b><hr>[ ]PolicyAncestorStatus: ancestors"]] |
| 54 | + validation[["<b>tls</b><hr>LocalObjectReference: caCertificateRefs<br>wellKnownCACertificatesType: wellKnownCACertificates<br>PreciseHostname: hostname<br>[]SubjectAltName: subjectAltNames"]] |
| 55 | + ancestorStatus[["<b>ancestors</b><hr>AncestorRef: parentReference<br>GatewayController: controllerName<br>[]Condition: conditions"]] |
| 56 | + targetRefs[[<b>targetRefs</b><hr>]] |
| 57 | + service["<b>service</>"] |
| 58 | + backendTLSPolicy -->spec |
| 59 | + backendTLSPolicy -->status |
| 60 | + spec -->targetRefs & validation |
| 61 | + status -->ancestorStatus |
| 62 | + targetRefs -->service |
| 63 | + note[<em>choose only one<hr> caCertificateRefs OR wellKnownCACertificates</em>] |
| 64 | + style note fill:#fff |
| 65 | + validation -.- note |
| 66 | +``` |
| 67 | + |
| 68 | +The following illustrates a BackendTLSPolicy that configures TLS for a Service serving a backend: |
| 69 | +```mermaid |
| 70 | +flowchart LR |
| 71 | + client(["client"]) |
| 72 | + gateway["Gateway"] |
| 73 | + httproute["HTTP<BR>Route"] |
| 74 | + service["Service"] |
| 75 | + pod1["Pod"] |
| 76 | + pod2["Pod"] |
| 77 | + client -.->|HTTP <br> request| gateway |
| 78 | + gateway --> httproute |
| 79 | + httproute -.->|BackendTLSPolicy|service |
| 80 | + service --> pod1 & pod2 |
| 81 | +``` |
| 82 | + |
| 83 | +### Targeting backends |
| 84 | + |
| 85 | +A BackendTLSPolicy targets a backend Pod (or set of Pods) via one or more TargetRefs to a Service. This TargetRef is a |
| 86 | +required object reference that specifies a Service by its Name, Kind (Service), and optionally its Namespace and Group. |
| 87 | +TargetRefs identify the Service/s for which your HTTPRoute requires TLS. |
| 88 | + |
| 89 | + |
| 90 | + - Cross-namespace certificate references are not allowed. |
| 91 | + |
| 92 | +### BackendTLSPolicyValidation |
| 93 | + |
| 94 | +A BackendTLSPolicyValidation is the specification for the BackendTLSPolicy and defines the configuration for TLS, |
| 95 | +including hostname (for server name indication) and certificates. |
| 96 | + |
| 97 | +#### Hostname |
| 98 | + |
| 99 | +Hostname defines the server name indication (SNI) the Gateway should use in order to connect to the backend, and must |
| 100 | +match the certificate served by the backend pod. A hostname is the fully qualified domain name of a network host, as |
| 101 | +defined by [RFC 3986][rfc-3986]. Note the following deviations from the “host” part of the URI as defined in the RFC: |
| 102 | + |
| 103 | +- IP addresses are not allowed. |
| 104 | + |
| 105 | +Also note: |
| 106 | + |
| 107 | + |
| 108 | + - Wildcard hostnames are not allowed. |
| 109 | + |
| 110 | +#### Subject Alternative Names |
| 111 | + |
| 112 | + |
| 113 | + This field was added to BackendTLSPolicy in `v1.2.0` |
| 114 | +The subjectAltNames field enables basic mutual TLS configuration between Gateways and backends, as well as the optional use of SPIFFE. When subjectAltNames is specified, the certificate served by the backend must have at least one Subject Alternative Name matching one of the specified values. This is particularly useful for SPIFFE implementations where URI-based SANs may not be valid SNIs. |
| 115 | +Subject Alternative Names may contain one of either a Hostname or URI field, and must contain a Type specifying whether Hostname or URI is chosen. |
| 116 | + |
| 117 | + |
| 118 | + - IP addresses and wildcard hostnames are not allowed. (see the description for Hostname above for more details). |
| 119 | + - Hostname: DNS name format |
| 120 | + - URI: URI format (e.g., SPIFFE ID) |
| 121 | + |
| 122 | +#### TLS Options |
| 123 | + |
| 124 | + |
| 125 | + This field was added to BackendTLSPolicy in `v1.2.0` |
| 126 | +The options field allows specification of implementation-specific TLS configurations. This can include: |
| 127 | + |
| 128 | +- Vendor-specific mutual TLS automation configuration |
| 129 | +- Minimum supported TLS version restrictions |
| 130 | +- Supported cipher suite configurations |
| 131 | + |
| 132 | +Check your implementation documentation for details. |
| 133 | + |
| 134 | +### |
| 135 | +#### Certificates |
| 136 | + |
| 137 | +The BackendTLSPolicyValidation must contain a certificate reference of some kind, and contains two ways to configure the |
| 138 | +certificate to use for backend TLS, CACertificateRefs and WellKnownCACertificates. Only one of these may be used per |
| 139 | +BackendTLSPolicyValidation. |
| 140 | + |
| 141 | +##### CACertificateRefs |
| 142 | + |
| 143 | +CACertificateRefs refer to one or more PEM-encoded TLS certificates. |
| 144 | + |
| 145 | + |
| 146 | + - Cross-namespace certificate references are not allowed. |
| 147 | + |
| 148 | +##### WellKnownCACertificates |
| 149 | + |
| 150 | +If you are working in an environment where specific TLS certificates are not required, and your Gateway API |
| 151 | +implementation allows system or default certificates to be used, e.g. in a development environment, you may |
| 152 | +set WellKnownCACertificates to "System" to tell the Gateway to use a set of trusted CA Certificates. There may be |
| 153 | +some variation in which system certificates are used by each implementation. Refer to documentation from your |
| 154 | +implementation of choice for more information. |
| 155 | + |
| 156 | +### PolicyStatus |
| 157 | + |
| 158 | +Status defines the observed state of the BackendTLSPolicy and is not user-configurable. Check status in the same |
| 159 | +way you do for other Gateway API objects to verify correct operation. Note that the status in BackendTLSPolicy |
| 160 | +uses `PolicyAncestorStatus` to allow you to know which parentReference set that particular status. |
| 161 | + |
| 162 | +[backendtlspolicy]: https://gateway-api.sigs.k8s.io/reference/1.4/spec/#backendtlspolicy |
| 163 | +[validation]: https://gateway-api.sigs.k8s.io/reference/1.4/spec/#backendtlspolicyvalidation |
| 164 | +[caCertificateRefs]: https://gateway-api.sigs.k8s.io/reference/1.4/spec/#localobjectreference |
| 165 | +[wellKnownCACertificates]: https://gateway-api.sigs.k8s.io/reference/1.4/spec/#localobjectreference |
| 166 | +[hostname]: https://gateway-api.sigs.k8s.io/reference/1.4/spec/#precisehostname |
| 167 | +[rfc-3986]: https://tools.ietf.org/html/rfc3986 |
| 168 | +[targetRefs]: https://gateway-api.sigs.k8s.io/reference/1.4/spec/#localpolicytargetreferencewithsectionname |
| 169 | +[subjectAltNames]: https://gateway-api.sigs.k8s.io/reference/1.4/spec/#subjectaltname |
| 170 | +[options]: https://gateway-api.sigs.k8s.io/reference/1.4/spec/#backendtlspolicyspec |
0 commit comments