|
| 1 | +# Detect CWE-329 in Android Application |
| 2 | + |
| 3 | + |
| 4 | +This scenario seeks to find **Generation of Predictable IV with CBC Mode** in the APK file. |
| 5 | + |
| 6 | +## CWE-329: Generation of Predictable IV with CBC Mode |
| 7 | + |
| 8 | + |
| 9 | +We analyze the definition of CWE-329 and identify its characteristics. |
| 10 | + |
| 11 | +See [CWE-329](https://cwe.mitre.org/data/definitions/329.html) for more details. |
| 12 | + |
| 13 | +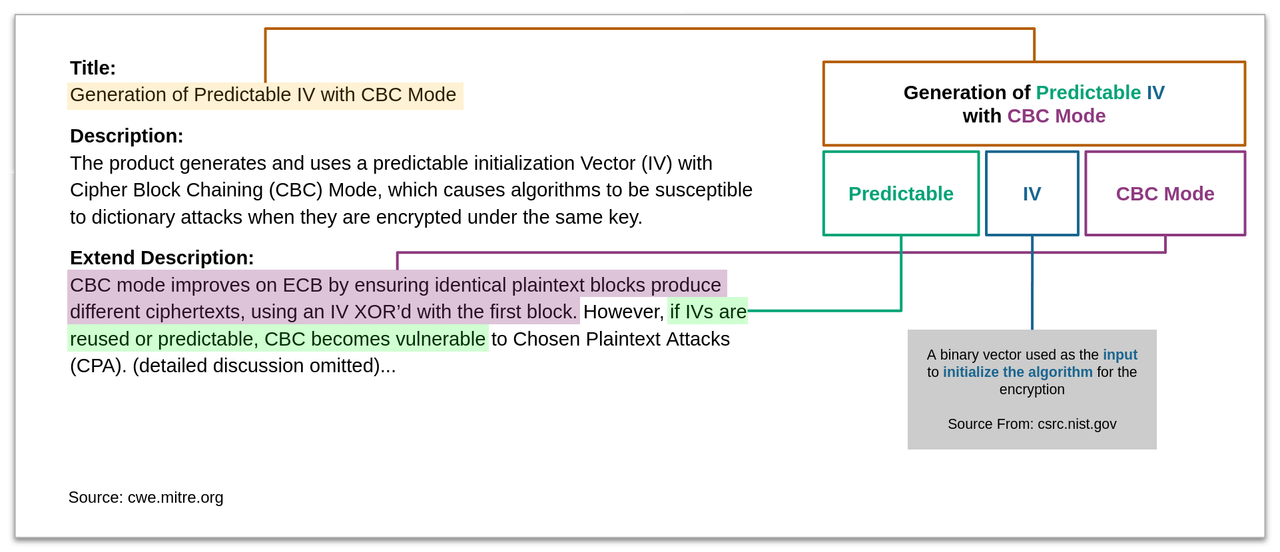 |
| 14 | + |
| 15 | +## Code of CWE-329 in InsecureBankv2.apk |
| 16 | + |
| 17 | + |
| 18 | +We use the [InsecureBankv2.apk](https://github.com/dineshshetty/Android-InsecureBankv2) sample to explain the vulnerability code of CWE-329. |
| 19 | + |
| 20 | +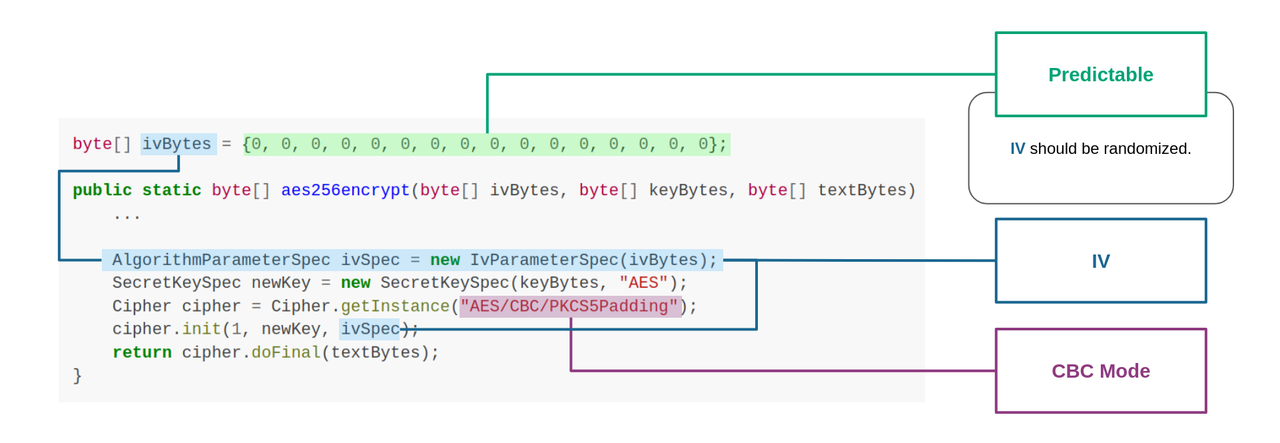 |
| 21 | + |
| 22 | +## CWE-329 Detection Process Using Quark Script API |
| 23 | + |
| 24 | + |
| 25 | +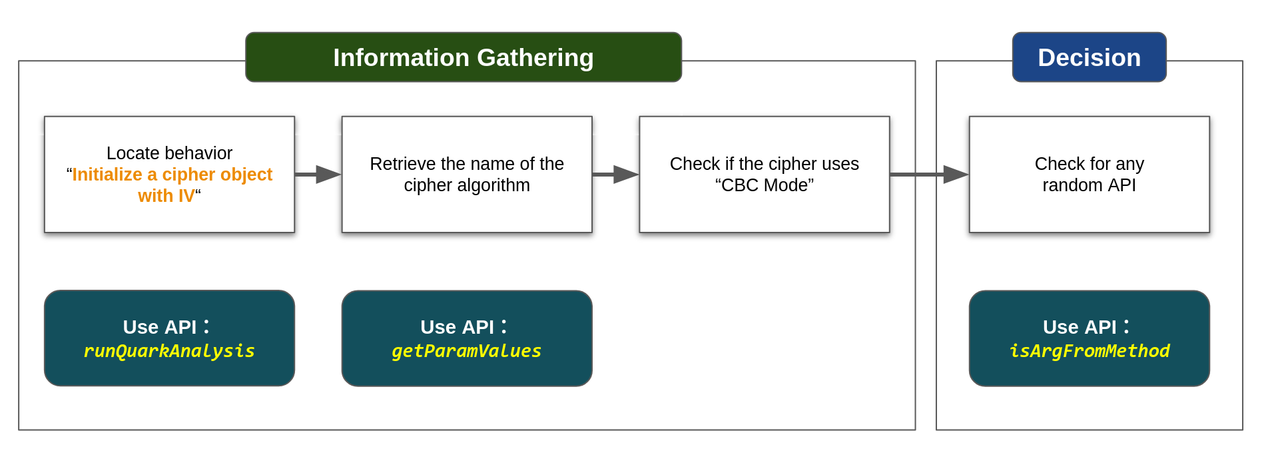 |
| 26 | + |
| 27 | +Let’s use the above APIs to show how the Quark script finds this vulnerability. |
| 28 | + |
| 29 | +To begin with, we created a detection rule named ``initializeCipherWithIV.json`` to identify behaviors that initialize a cipher object with IV. Then, we use API `behaviorInstance.getParamValues()` to check if the cipher object uses CBC mode. |
| 30 | + |
| 31 | +Finally, we use API ``behaviorInstance.isArgFromMethod(targetMethod)`` to check if any random API is applied on the IV used in the cipher object. If **NO**, it could imply that the APK uses a predictable IV in CBC mode cipher, potentially leading to a CWE-329 vulnerability. |
| 32 | + |
| 33 | +## Quark Script CWE-329.py |
| 34 | + |
| 35 | +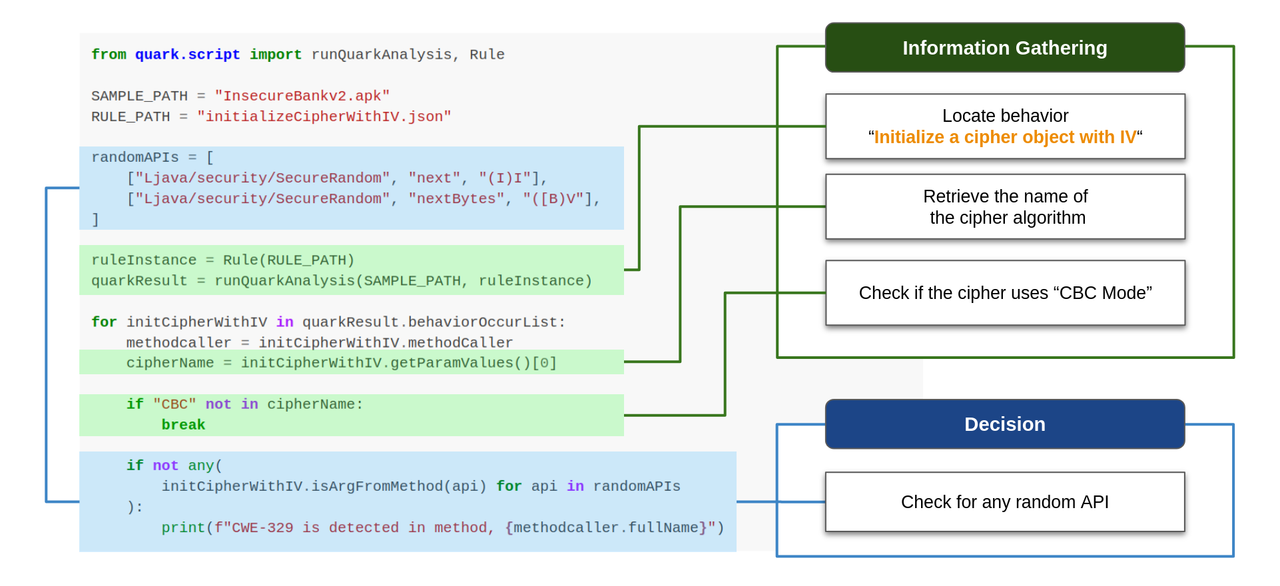 |
| 36 | + |
| 37 | +```python |
| 38 | +from quark.script import runQuarkAnalysis, Rule |
| 39 | + |
| 40 | +SAMPLE_PATH = "InsecureBankv2.apk" |
| 41 | +RULE_PATH = "initializeCipherWithIV.json" |
| 42 | + |
| 43 | +randomAPIs = [ |
| 44 | + ["Ljava/security/SecureRandom", "next", "(I)I"], |
| 45 | + ["Ljava/security/SecureRandom", "nextBytes", "([B)V"], |
| 46 | +] |
| 47 | + |
| 48 | +ruleInstance = Rule(RULE_PATH) |
| 49 | +quarkResult = runQuarkAnalysis(SAMPLE_PATH, ruleInstance) |
| 50 | + |
| 51 | +for initCipherWithIV in quarkResult.behaviorOccurList: |
| 52 | + methodcaller = initCipherWithIV.methodCaller |
| 53 | + cipherName = initCipherWithIV.getParamValues()[0] |
| 54 | + |
| 55 | + if "CBC" not in cipherName: |
| 56 | + break |
| 57 | + |
| 58 | + if not any( |
| 59 | + initCipherWithIV.isArgFromMethod(api) for api in randomAPIs |
| 60 | + ): |
| 61 | + print(f"CWE-329 is detected in method, {methodcaller.fullName}") |
| 62 | +``` |
| 63 | + |
| 64 | +## Quark Rule: initializeCipherWithIV.json |
| 65 | + |
| 66 | +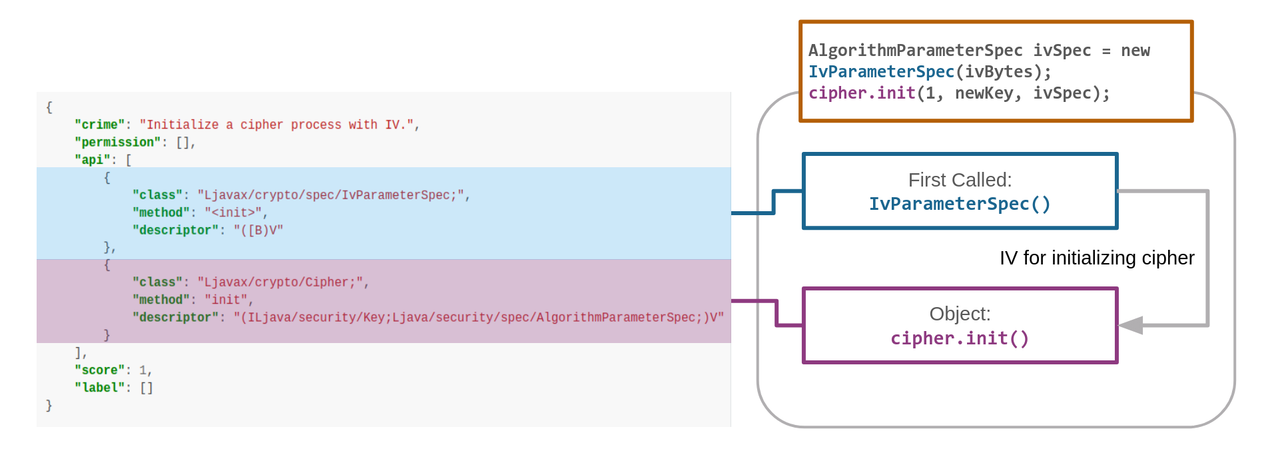 |
| 67 | + |
| 68 | +```json |
| 69 | +{ |
| 70 | + "crime": "Initialize a cipher object with IV", |
| 71 | + "permission": [], |
| 72 | + "api": [ |
| 73 | + { |
| 74 | + "class": "Ljavax/crypto/spec/IvParameterSpec;", |
| 75 | + "method": "<init>", |
| 76 | + "descriptor": "([B)V" |
| 77 | + }, |
| 78 | + { |
| 79 | + "class": "Ljavax/crypto/Cipher;", |
| 80 | + "method": "init", |
| 81 | + "descriptor": "(ILjava/security/Key;Ljava/security/spec/AlgorithmParameterSpec;)V" |
| 82 | + } |
| 83 | + ], |
| 84 | + "score": 1, |
| 85 | + "label": [] |
| 86 | +} |
| 87 | +``` |
| 88 | + |
| 89 | +## Quark Script Result |
| 90 | + |
| 91 | +```text |
| 92 | +$ python CWE-329.py |
| 93 | +CWE-329 is detected in method, Lcom/google/android/gms/internal/zzar; zzc ([B Ljava/lang/String;)[B |
| 94 | +CWE-329 is detected in method, Lcom/android/insecurebankv2/CryptoClass; aes256encrypt ([B [B [B)[B |
| 95 | +CWE-329 is detected in method, Lcom/android/insecurebankv2/CryptoClass; aes256decrypt ([B [B [B)[B |
| 96 | +``` |
| 97 | + |
| 98 | + |
0 commit comments