You signed in with another tab or window. Reload to refresh your session.You signed out in another tab or window. Reload to refresh your session.You switched accounts on another tab or window. Reload to refresh your session.Dismiss alert
Copy file name to clipboardExpand all lines: CWE-338/README.md
+31-19Lines changed: 31 additions & 19 deletions
Display the source diff
Display the rich diff
Original file line number
Diff line number
Diff line change
@@ -1,23 +1,32 @@
1
-
# Detect CWE-338 in Android Application (pivva.apk)
1
+
# Detect CWE-338 in Android Application
2
2
3
-
This scenario aims to detect the **Use of Cryptographically Weak
4
-
Pseudo-Random Number Generator (PRNG).** See
5
-
[CWE-338](https://cwe.mitre.org/data/definitions/338.html) for more
6
-
details.
3
+
This scenario seeks to find **Use of Cryptographically Weak Pseudo-Random Number Generator (PRNG)**.
7
4
8
-
To demonstrate how the Quark script finds this vulnerability, we will
9
-
use the [pivaa](https://github.com/HTBridge/pivaa) APK file and the
10
-
above APIs.
5
+
## CWE-338: Use of Cryptographically Weak Pseudo-Random Number Generator (PRNG)
11
6
12
-
First, we design a detection rule `useMethodOfPRNG.json` to spot on
13
-
behavior that uses Pseudo Random Number Generator (PRNG). Then, we use
14
-
API `methodInstance.getXrefFrom()` to get the caller method of PRNG.
15
-
Finally, we use some keywords such as "token", "password", and "encrypt"
16
-
to check if the PRNG is for credential usage.
7
+
We analyze the definition of CWE-338 and identify its characteristics.
8
+
9
+
See [CWE-338](https://cwe.mitre.org/data/definitions/338.html) for more details.
10
+
11
+

12
+
13
+
## Code of CWE-338 in pivaa.apk
14
+
15
+
We use the [pivaa.apk](https://github.com/HTBridge/pivaa) sample to explain the vulnerability code of CWE-338.
16
+
17
+
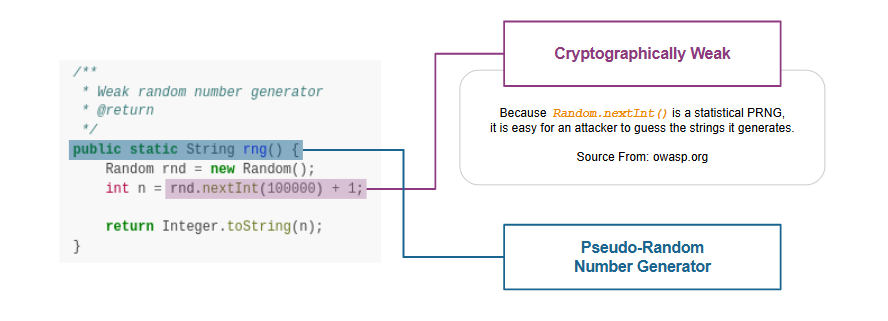
18
+
19
+
## CWE-338 Detection Process Using Quark Script API
20
+
21
+

22
+
23
+
First, we design a detection rule `useMethodOfPRNG.json` to spot on behavior that uses Pseudo Random Number Generator (PRNG). Then, we use API `methodInstance.getXrefFrom()` to get the caller method of PRNG. Finally, we use some keywords such as "token", "password", and "encrypt" to check if the PRNG is for credential usage.
[pivaa.apk](https://github.com/HTBridge/pivaa), and the above APIs to
11
-
show how the Quark script finds this vulnerability.
7
+
We analyze the definition of CWE-489 and identify its characteristics.
12
8
13
-
First, we use Quark API `getApplication(samplePath)` to get the
14
-
application element in the manifest file. Then we use
15
-
`applicationInstance.isDebuggable()` to check if the application element
16
-
sets the attribute `android:debuggable` to true. If **Yes**, that causes
17
-
CWE-489 vulnerabilities.
9
+
See [CWE-489](https://cwe.mitre.org/data/definitions/489.html) for more details.
10
+
11
+

12
+
13
+
## Code of CWE-489 in allsafe.apk
14
+
15
+
We use the [allsafe.apk](https://github.com/t0thkr1s/allsafe) sample to explain the vulnerability code of CWE-489.
16
+
17
+

18
+
19
+
## CWE-489 Detection Process Using Quark Script API
20
+
21
+

22
+
23
+
First, we use Quark API ``getApplication(samplePath)`` to get the application element in the manifest file. Then we use ``applicationInstance.isDebuggable()`` to check if the application element sets the attribute ``android:debuggable`` to true. If **Yes**, that causes CWE-489 vulnerabilities.
18
24
19
25
## Quark Script CWE-489.py
20
26
21
-
The Quark Script below uses allsafe.apk to demonstrate. You can change
22
-
the `SAMPLE_PATH` to the sample you want to detect. For example,
23
-
`SAMPLE_PATH = AndroGoat.apk` or `SAMPLE_PATH = pivaa.apk`.
27
+

24
28
25
-
```python
29
+
```python
26
30
from quark.script import getApplication
27
31
28
32
SAMPLE_PATH="allsafe.apk"
@@ -33,23 +37,7 @@ if getApplication(SAMPLE_PATH).isDebuggable():
# Detect CWE-532 in Android Application (dvba.apk)
1
+
# Detect CWE-532 in Android Application
2
2
3
-
This scenario seeks to find **insertion of sensitive information into
4
-
Log file**. See
5
-
[CWE-532](https://cwe.mitre.org/data/definitions/532.html) for more
6
-
details.
3
+
This scenario seeks to find **insertion of sensitive information into Log file** in the APK file.
7
4
8
-
Let's use this
9
-
[APK](https://github.com/rewanthtammana/Damn-Vulnerable-Bank) and the
10
-
above APIs to show how the Quark script finds this vulnerability.
5
+
## CWE-532: Insertion of Sensitive Information into Log File
11
6
12
-
First, we use API `findMethodInAPK(samplePath, targetMethod)` to locate
13
-
`log.d` method. Then we use API `methodInstance.getArguments()` to get
14
-
the argument that input to `log.d`. Finally, we use some keywords such
15
-
as \"token\", \"password\", and \"decrypt\" to check if arguments
16
-
include sensitive data. If the answer is YES, that may cause sensitive
17
-
data leakage into log file.
7
+
We analyze the definition of CWE-532 and identify its characteristics.
18
8
19
-
You can use your own keywords in the keywords list to detect sensitive
20
-
data.
9
+
See [CWE-532](https://cwe.mitre.org/data/definitions/532.html) for more details.
21
10
22
-
## Quark Script CWE-532.py
11
+

23
12
24
-
```python
13
+
## Code of CWE-532 in dvba.apk
14
+
15
+
We use the [dvba.apk](https://github.com/rewanthtammana/Damn-Vulnerable-Bank) sample to explain the vulnerability code of CWE-532.
16
+
17
+

18
+
19
+
## CWE-532 Detection Process Using Quark Script API
20
+
21
+

22
+
23
+
Let's use the above APIs to show how the Quark script finds this vulnerability.
24
+
25
+
First, we use the API ``findMethodInAPK(samplePath, targetMethod)`` to locate ``log.d`` method. Then we use API ``methodInstance.getArguments()`` to get the argument that input to ``log.d``. Finally, we use some keywords such as "token", "password", and "decrypt" to check if arguments include sensitive data. If the answer is **YES**, that may cause sensitive data leakage into log file.
26
+
27
+
You can use your own keywords in the keywords list to detect sensitive data.
28
+
29
+
## Quark Script: CWE-532.py
30
+
31
+

32
+
33
+
```python
25
34
from quark.script import findMethodInAPK
26
35
27
36
SAMPLE_PATH="dvba.apk"
@@ -48,7 +57,7 @@ for debugLogger in methodsFound:
48
57
49
58
## Quark Script Result
50
59
51
-
```TEXT
60
+
```TEXT
52
61
$ python CWE-532.py
53
62
CWE-532 is detected in method, Lcom/google/firebase/auth/FirebaseAuth; d (Lc/c/b/h/o;)V
0 commit comments