-
Notifications
You must be signed in to change notification settings - Fork 0
Open
Description
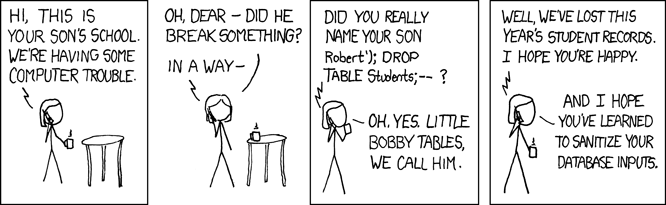
You're using string concatenation instead of using a structured query / preparted statement.
https://github.com/fmohican/SQL-WhiteList/blob/master/src/main/java/ga/fmohican/sql/SQLWL.java#L59
ResultSet rs = stmt.executeQuery("select `"+SQLConfig.susers+"` from `"+SQLConfig.stabname+"` where ( `"+SQLConfig.susers+"`='" + newname + "' AND `"+SQLConfig.swhitelist+"` = 1 );");Odds are that someone isn't going to use a ');drop table users;-- as a name, but it's a good habit to wrap any user input in a prepared statement`.
Metadata
Metadata
Assignees
Labels
No labels