Alguém poderia me ajudar ??? #2325
Unanswered
Joao-vitor-090
asked this question in
Perguntas e Respostas
Replies: 1 comment 7 replies
-
|
Você pode passar o seu package.json, apenas a parte de dependencies e devDependencies? |
Beta Was this translation helpful? Give feedback.
7 replies
Sign up for free
to join this conversation on GitHub.
Already have an account?
Sign in to comment
Uh oh!
There was an error while loading. Please reload this page.
-
Estou a um tempo com esse problema de vulnerabilidade no node(npm), não consigo utilizar nenhuma biblioteca externa e muito menos usar um simples "npm install". Já tentei reinstalar e nada. Segue o que aparece, ao inserir "npm install"
=>
npm install
up to date, audited 777 packages in 14s
34 vulnerabilities (1 low, 10 moderate, 16 high, 7 critical)
To address issues that do not require attention, run:
npm audit fix
To address all issues possible (including breaking changes), run:
npm audit fix --force
Some issues need review, and may require choosing
a different dependency.
Run
npm auditfor details.Após isso fiz "npm audit fix" e tenho o seguinte retorno =>
up to date, audited 777 packages in 2s
npm audit report
bl <1.2.3
Severity: moderate
Remote Memory Exposure in bl - GHSA-pp7h-53gx-mx7r
fix available via
npm audit fix --forceWill install [email protected], which is a breaking change
node_modules/bl
request 2.16.0 - 2.86.0
Depends on vulnerable versions of bl
Depends on vulnerable versions of hawk
Depends on vulnerable versions of qs
Depends on vulnerable versions of tunnel-agent
node_modules/request
firebase-tools <=3.19.0
Depends on vulnerable versions of open
Depends on vulnerable versions of optimist
Depends on vulnerable versions of request
Depends on vulnerable versions of tar
node_modules/firebase-tools
clean-css <4.1.11
Regular Expression Denial of Service in clean-css - GHSA-wxhq-pm8v-cw75
fix available via
npm audit fixnode_modules/clean-css
pacman >=0.10.5
Depends on vulnerable versions of clean-css
Depends on vulnerable versions of express
Depends on vulnerable versions of mime
Depends on vulnerable versions of uglify-js
Depends on vulnerable versions of underscore
node_modules/pacman
connect <=2.30.2
Severity: high
methodOverride Middleware Reflected Cross-Site Scripting in connect - GHSA-3fw8-66wf-pr7m
Depends on vulnerable versions of cookie-signature
Depends on vulnerable versions of fresh
Depends on vulnerable versions of qs
Depends on vulnerable versions of send
fix available via
npm audit fixnode_modules/connect
express <=4.15.4 || 5.0.0-alpha.1 - 5.0.0-alpha.5
Depends on vulnerable versions of connect
Depends on vulnerable versions of cookie-signature
Depends on vulnerable versions of fresh
Depends on vulnerable versions of send
node_modules/express
cookie-signature <1.0.4
Severity: moderate
Timing Attack in cookie-signature - GHSA-92vm-wfm5-mxvv
fix available via
npm audit fixnode_modules/cookie-signature
cryptiles <=4.1.1
Severity: critical
Insufficient Entropy in cryptiles - GHSA-rq8g-5pc5-wrhr
Depends on vulnerable versions of boom
fix available via
npm audit fix --forceWill install [email protected], which is a breaking change
node_modules/cryptiles
hawk <=9.0.0
Depends on vulnerable versions of boom
Depends on vulnerable versions of cryptiles
Depends on vulnerable versions of hoek
Depends on vulnerable versions of sntp
node_modules/hawk
dicer *
Severity: high
Crash in HeaderParser in dicer - GHSA-wm7h-9275-46v2
No fix available
node_modules/dicer
busboy <=0.3.1
Depends on vulnerable versions of dicer
node_modules/busboy
co-busboy *
Depends on vulnerable versions of busboy
node_modules/co-busboy
egg-multipart >=1.0.0
Depends on vulnerable versions of co-busboy
node_modules/egg-multipart
egg >=0.0.8
Depends on vulnerable versions of egg-multipart
node_modules/egg
ssr-types 5.4.1 - 6.1.42
Depends on vulnerable versions of egg
node_modules/ssr-types
ssr-client-utils 5.4.1 - 5.6.42
Depends on vulnerable versions of ssr-types
node_modules/ssr-client-utils
my-vue-app *
Depends on vulnerable versions of ssr-client-utils
node_modules/my-vue-app
fresh <0.5.2
Severity: high
Regular Expression Denial of Service in fresh - GHSA-9qj9-36jm-prpv
fix available via
npm audit fixnode_modules/fresh
send <=0.15.6
Depends on vulnerable versions of fresh
Depends on vulnerable versions of mime
node_modules/send
got <11.8.5
Severity: moderate
Got allows a redirect to a UNIX socket - GHSA-pfrx-2q88-qq97
fix available via
npm audit fix --forceWill install [email protected], which is a breaking change
node_modules/got
download >=4.0.0
Depends on vulnerable versions of got
node_modules/download
hoek <4.2.1
Severity: moderate
Prototype Pollution in hoek - GHSA-jp4x-w63m-7wgm
fix available via
npm audit fix --forceWill install [email protected], which is a breaking change
node_modules/hoek
boom <=3.1.2
Depends on vulnerable versions of hoek
node_modules/boom
sntp 0.0.0 || 0.1.1 - 2.0.0
Depends on vulnerable versions of hoek
node_modules/sntp
mime <1.4.1
Severity: moderate
Regular Expression Denial of Service in mime - GHSA-wrvr-8mpx-r7pp
fix available via
npm audit fixnode_modules/mime
node_modules/send/node_modules/mime
minimist <=1.2.5
Severity: critical
Prototype Pollution in minimist - GHSA-xvch-5gv4-984h
Prototype Pollution in minimist - GHSA-vh95-rmgr-6w4m
fix available via
npm audit fix --forceWill install [email protected], which is a breaking change
node_modules/optimist/node_modules/minimist
optimist >=0.6.0
Depends on vulnerable versions of minimist
node_modules/optimist
open <6.0.0
Severity: critical
Command Injection in open - GHSA-28xh-wpgr-7fm8
fix available via
npm audit fix --forceWill install [email protected], which is a breaking change
node_modules/open
qs <=6.0.3
Severity: high
Prototype Pollution Protection Bypass in qs - GHSA-gqgv-6jq5-jjj9
Denial-of-Service Extended Event Loop Blocking in qs - GHSA-f9cm-p3w6-xvr3
Denial-of-Service Memory Exhaustion in qs - GHSA-jjv7-qpx3-h62q
fix available via
npm audit fix --forceWill install [email protected], which is a breaking change
node_modules/qs
node_modules/request/node_modules/qs
tar <=4.4.17
Severity: high
Arbitrary File Overwrite in tar - GHSA-j44m-qm6p-hp7m
Symlink Arbitrary File Overwrite in tar - GHSA-gfjr-3jmm-4g9v
Arbitrary File Creation/Overwrite on Windows via insufficient relative path sanitization - GHSA-5955-9wpr-37jh
Arbitrary File Creation/Overwrite via insufficient symlink protection due to directory cache poisoning using symbolic links - GHSA-qq89-hq3f-393p
Arbitrary File Creation/Overwrite via insufficient symlink protection due to directory cache poisoning using symbolic links - GHSA-9r2w-394v-53qc
Arbitrary File Creation/Overwrite due to insufficient absolute path sanitization - GHSA-3jfq-g458-7qm9
Arbitrary File Creation/Overwrite via insufficient symlink protection due to directory cache poisoning - GHSA-r628-mhmh-qjhw
fix available via
npm audit fix --forceWill install [email protected], which is a breaking change
node_modules/tar
tunnel-agent <0.6.0
Severity: moderate
Memory Exposure in tunnel-agent - GHSA-xc7v-wxcw-j472
fix available via
npm audit fix --forceWill install [email protected], which is a breaking change
node_modules/tunnel-agent
uglify-js <=2.5.0
Severity: critical
Incorrect Handling of Non-Boolean Comparisons During Minification in uglify-js - GHSA-34r7-q49f-h37c
Regular Expression Denial of Service in uglify-js - GHSA-c9f4-xj24-8jqx
fix available via
npm audit fixnode_modules/uglify-js
underscore 1.3.2 - 1.12.0
Severity: high
Arbitrary Code Execution in underscore - GHSA-cf4h-3jhx-xvhq
fix available via
npm audit fixnode_modules/underscore
34 vulnerabilities (1 low, 10 moderate, 16 high, 7 critical)
To address issues that do not require attention, run:
npm audit fix
To address all issues possible (including breaking changes), run:
npm audit fix --force
Some issues need review, and may require choosing
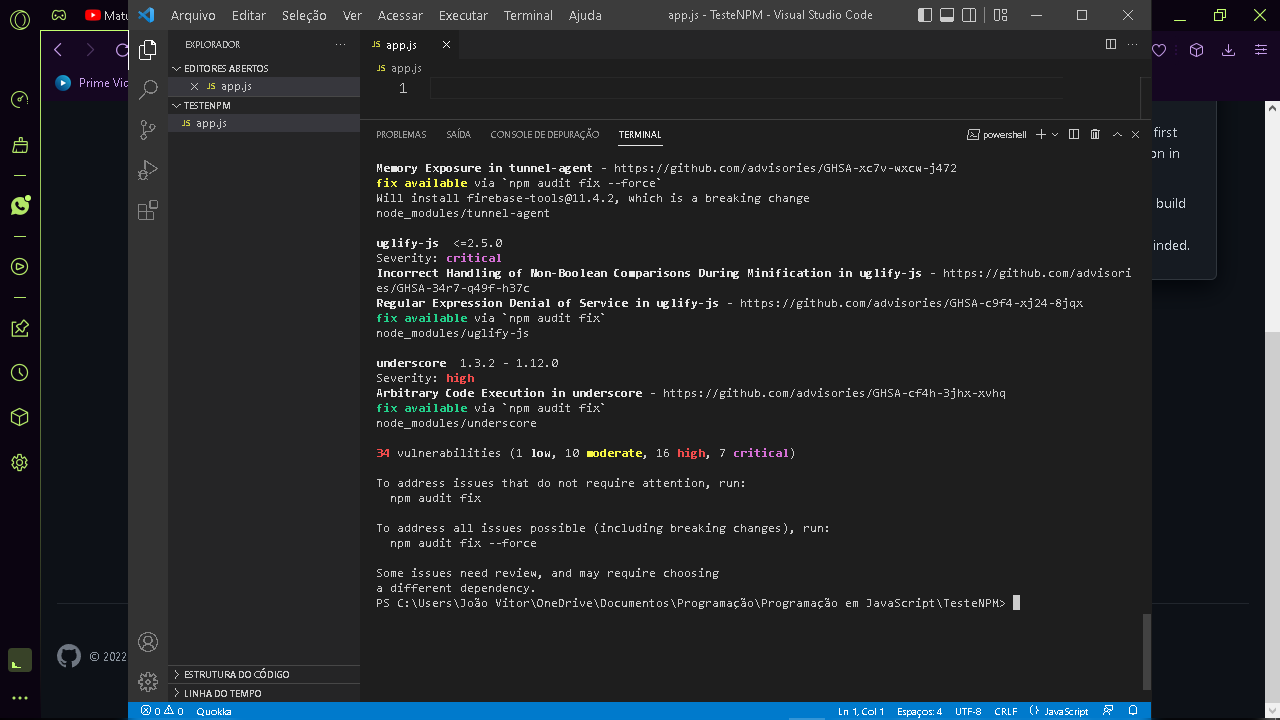
a different [dependency.]
Beta Was this translation helpful? Give feedback.
All reactions