You signed in with another tab or window. Reload to refresh your session.You signed out in another tab or window. Reload to refresh your session.You switched accounts on another tab or window. Reload to refresh your session.Dismiss alert
Copy file name to clipboardExpand all lines: src/content/docs/authenticate/enterprise-connections/advanced-saml-configurations.mdx
+3-1Lines changed: 3 additions & 1 deletion
Display the source diff
Display the rich diff
Original file line number
Diff line number
Diff line change
@@ -62,6 +62,8 @@ Only configure key attributes if supported by your IdP.
62
62
63
63
You can pass provider-specific parameters to an Identity Provider (IdP) during authentication. These are also known as 'upstream params'. The values your pass can either be static per connection or dynamic per user.
64
64
65
-
You can use upstream paramsto create a smoother sign in experience - by passing the email through, or to offer an account switcher (such as the Google account switcher) during sign in.
65
+
You can use upstream params to create a smoother sign in experience - by passing the email through, or to offer an account switcher (such as the Google account switcher) during sign in.
66
66
67
67
Note that every identity provider has their own set of supported parameters and values, so you'll need to check their documentation to determine which URL parameters are supported.
68
+
69
+
For more information, see [Pass parameters to identity providers](/authenticate/auth-guides/pass-params-idp/).
Copy file name to clipboardExpand all lines: src/content/docs/authenticate/enterprise-connections/cloudflare-saml.mdx
+2-2Lines changed: 2 additions & 2 deletions
Display the source diff
Display the rich diff
Original file line number
Diff line number
Diff line change
@@ -62,8 +62,8 @@ You can make a connection available only to a specific organization, or you can
62
62
63
63
64
64
65
-
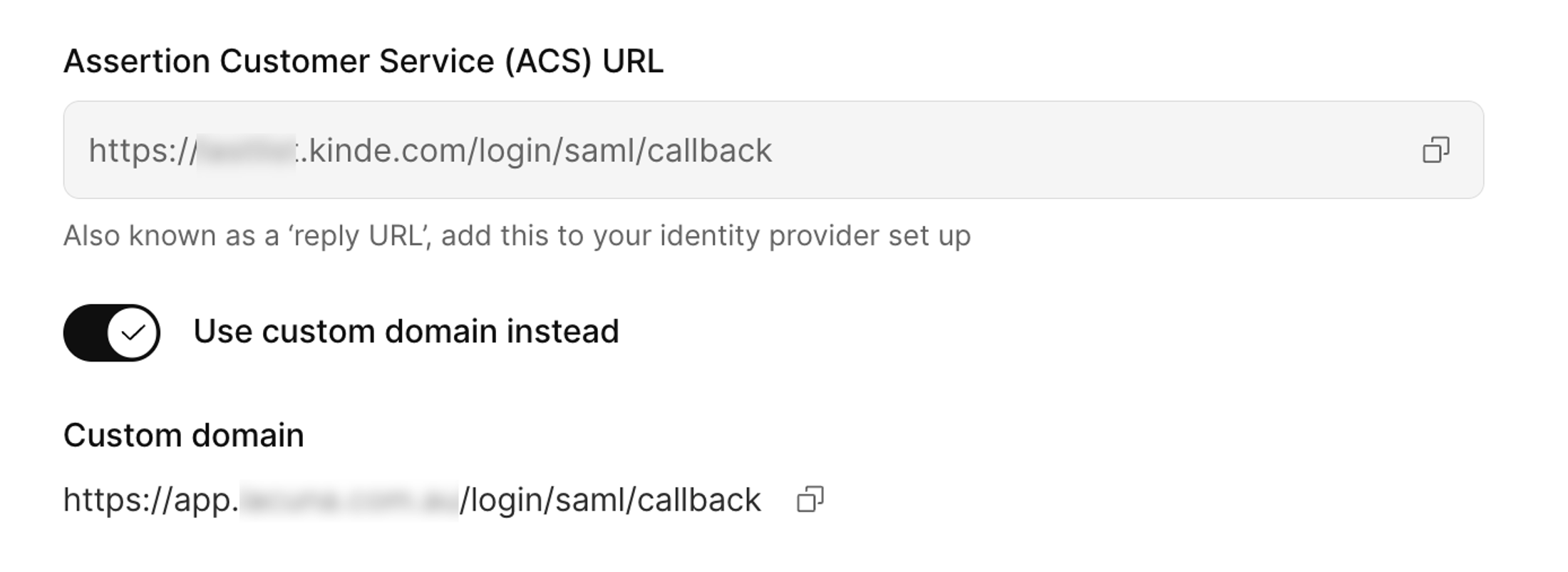
11. Copy the reply relevant URL:
66
-
1. If you don't use a custom domain, copy the **Assertion customer service (ACS) URL**.
65
+
11. Copy the relevant reply URL:
66
+
1. If you don't use a custom domain, copy the **ACS URL**.
67
67
2. If you do use a custom domain, select the **Use custom domain instead** option and copy the custom domain URL.
68
68
Later, add this URL to your identity provider configuration.
69
69
12. If you want to enable just-in-time (JIT) provisioning for users, select the **Create a user record in Kinde** option. This saves time adding users manually or via API later.
Copy file name to clipboardExpand all lines: src/content/docs/authenticate/enterprise-connections/custom-saml-google-workspace.mdx
+2-2Lines changed: 2 additions & 2 deletions
Display the source diff
Display the rich diff
Original file line number
Diff line number
Diff line change
@@ -60,8 +60,8 @@ You can make a connection available only to a specific organization, or you can
60
60
61
61

62
62
63
-
11. Copy the reply relevant URL:
64
-
1. If you don't use a custom domain, copy the **Assertion customer service (ACS) URL**.
63
+
11. Copy the relevant reply URL:
64
+
1. If you don't use a custom domain, copy the **ACS URL**.
65
65
2. If you do use a custom domain, select the **Use custom domain instead** option and copy the custom domain URL.
66
66
Later, add this URL to your identity provider configuration.
67
67
12. If you want to enable just-in-time (JIT) provisioning for users, select the **Create a user record in Kinde** option. This saves time adding users manually or via API later.
Copy file name to clipboardExpand all lines: src/content/docs/authenticate/enterprise-connections/custom-saml.mdx
+2-2Lines changed: 2 additions & 2 deletions
Display the source diff
Display the rich diff
Original file line number
Diff line number
Diff line change
@@ -82,8 +82,8 @@ Depending on your SAML set up, you may need to include advanced configurations f
82
82
83
83

84
84
85
-
12. Copy the reply relevant URL:
86
-
1. If you don't use a custom domain, copy the **Assertion customer service (ACS) URL**.
85
+
12. Copy the relevant reply URL:
86
+
1. If you don't use a custom domain, copy the **ACS URL**.
87
87
2. If you do use a custom domain, select the **Use custom domain instead** option and copy the custom domain URL.
88
88
Later, add this URL to your identity provider configuration.
89
89
13. If you want to enable just-in-time (JIT) provisioning for users, select the **Create a user record in Kinde** option. This saves time adding users manually or via API later.
10. If you use home realm domains, the sign in button is hidden on the auth screen by default. To show the SSO button, select the **Always show sign-in button** option.
80
-
11. Copy the reply relevant URL:
81
-
1. If you don't use a custom domain, copy the **Assertion customer service (ACS) URL**.
80
+
11. Copy the relevant reply URL:
81
+
1. If you don't use a custom domain, copy the **ACS URL**.
82
82
2. If you do use a custom domain, select the **Use custom domain instead** option and copy the custom domain URL.
83
83
Later, add this URL to your identity provider configuration.
3. Enter the **IdP metadata URL**. This URL comes from your identity provider.
46
+
3. Enter the **IdP metadata URL**. This URL comes from your identity provider. If you haven't set up your app yet, you can add this later.
47
47
48
48
49
49
@@ -60,8 +60,8 @@ Depending on your SAML set up, you may need to include advanced configurations f
60
60
61
61

62
62
63
-
11. Copy the reply relevant URL:
64
-
1. If you don't use a custom domain, copy the **Assertion customer service (ACS) URL**.
63
+
11. Copy the relevant reply URL:
64
+
1. If you don't use a custom domain, copy the **ACS URL**.
65
65
2. If you do use a custom domain, select the **Use custom domain instead** option and copy the custom domain URL.
66
66
Later, add this URL to your identity provider configuration.
67
67
12. If you want to enable just-in-time (JIT) provisioning for users, select the **Create a user record in Kinde** option. This saves time adding users manually or via API later.
@@ -95,7 +95,7 @@ Depending on your SAML set up, you may need to include advanced configurations f
95
95
3.**Name ID format:** Select **EmailAddress**.
96
96
4.**Application username**: Select **Email**.
97
97
5. Leave all other options to their default value and select **Next**.
98
-
7.In the next screen, select **I'm a software vendor. I'd like to integrate my app with Okta**, then select**Finish**. You will be redirected to the newly created application in Okta.
98
+
7.Select**Finish**. You will be redirected to the newly created application in Okta.
99
99
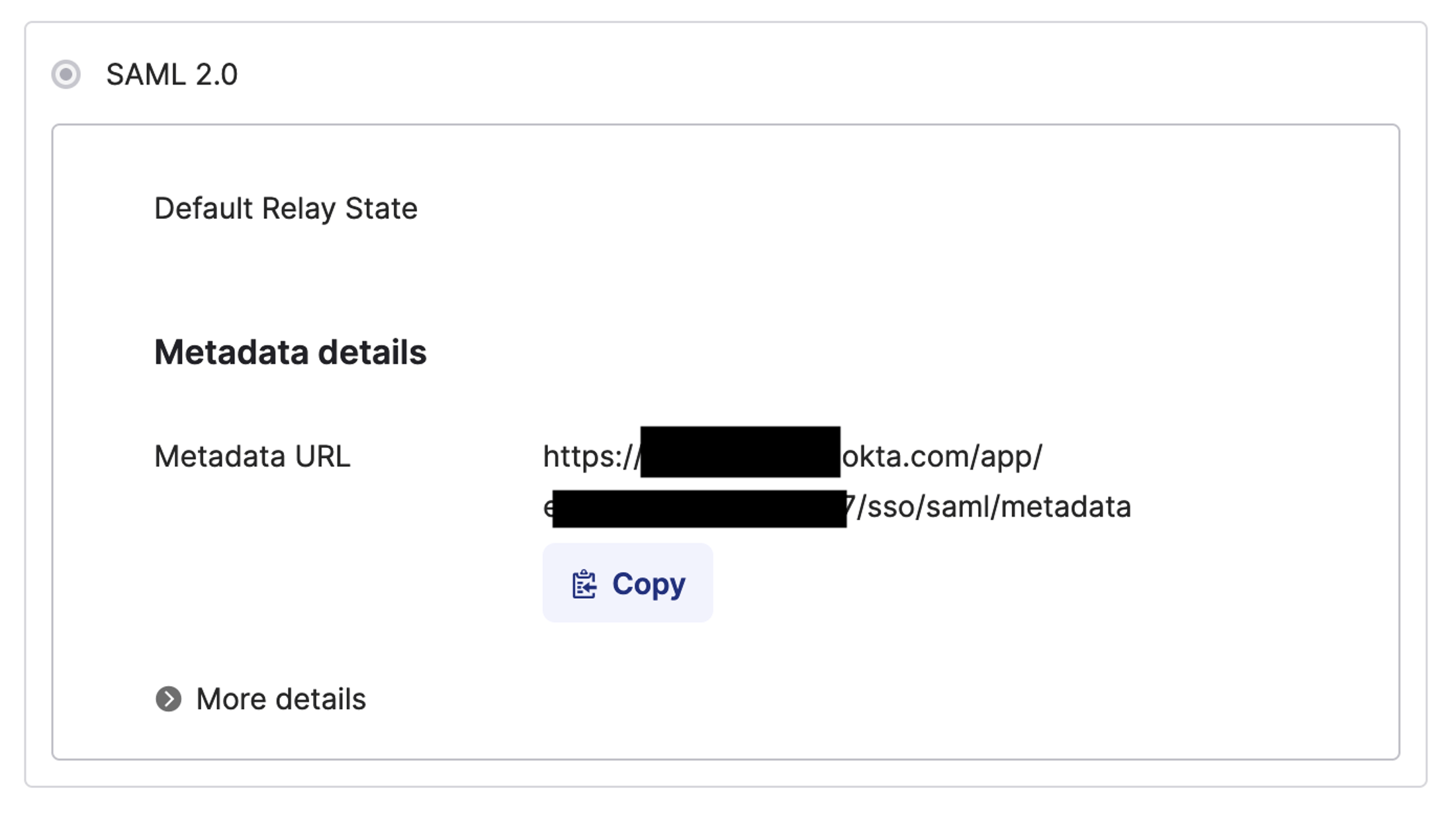
8. Select the **Sign on** tab and copy the metadata URL.
100
100
101
101
@@ -109,3 +109,13 @@ Depending on your SAML set up, you may need to include advanced configurations f
109
109
1. For environment-level connections, scroll down and select the apps that will use the auth method.
110
110
2. For organization-level connections, scroll down and select if you want to switch this on for the org.
111
111
5. Select **Save**. You can now use Okta as an IdP for the selected applications.
112
+
113
+
## Troubleshooting the connection
114
+
115
+
If you get an error in Okta that says **User is not assigned to this application**, it means you need to assign a user or group to your Okta application.
116
+
117
+
1. Go to the **Applications** section in your Okta Admin Console.
118
+
2. Select the SAML 2.0 app you set up.
119
+
3. Under the **Assignments** tab, click **Assign > Assign to People or Assign to Groups**.
120
+
4. Choose the user or group you want to assign to this application and save your changes.
Copy file name to clipboardExpand all lines: src/content/docs/workflows/example-workflows/new-password-provided-workflow.mdx
-2Lines changed: 0 additions & 2 deletions
Display the source diff
Display the rich diff
Original file line number
Diff line number
Diff line change
@@ -96,7 +96,6 @@ if (!isMinCharacters) {
96
96
"Provide a password at least 50 characters long"
97
97
);
98
98
}
99
-
100
99
```
101
100
102
101
The field names for the widget binding in this workflow are:
@@ -112,4 +111,3 @@ See examples on GitHub:
112
111
113
112
-[Sync passwords to another system](https://github.com/kinde-starter-kits/workflow-examples/blob/main/newPassword/securelySyncPasswordWorkflow.ts) - Use encryption keys to securely keep passwords in sync between systems.
114
113
-[Custom password validation](https://github.com/kinde-starter-kits/workflow-examples/blob/main/newPassword/customPasswordValidationWorkflow.ts) - Shows how to validate a password against your own rules.
0 commit comments