|
| 1 | +--- |
| 2 | +page_id: 00aa9631-5633-4b25-a75d-9263092a233f |
| 3 | +title: Use LastPass as a SAML identity provider |
| 4 | +sidebar: |
| 5 | + order: 13 |
| 6 | +relatedArticles: |
| 7 | + - 17559023-5b50-4690-ba7b-fd1df4b78664 |
| 8 | + - fcf28a71-c3a8-4474-9564-ad089d3f2105 |
| 9 | + - e100d77b-530b-4327-8216-93c955657e0c |
| 10 | + - 66b2a627-b24a-4ccf-a792-80a6a9fe35ef |
| 11 | +description: Step-by-step guide to integrating LastPass as a SAML identity provider with Kinde for enterprise authentication and access control. |
| 12 | +metadata: |
| 13 | + topics: [authenticate] |
| 14 | + sdk: [] |
| 15 | + languages: [] |
| 16 | + audience: [developer, enterprise-admin, security-engineer] |
| 17 | + complexity: advanced |
| 18 | + keywords: [LastPass, SAML, identity provider, IdP, enterprise auth, SSO, access policies] |
| 19 | + updated: 2025-01-16 |
| 20 | +featured: false |
| 21 | +deprecated: false |
| 22 | +--- |
| 23 | + |
| 24 | +If you use LastPass to centralize authentication and authorization in your business, you can integrate Kinde as a service provider for these processes. This gives you the benefits of Kinde’s robust auth capabilities, while keeping the familiar LastPass structure. |
| 25 | + |
| 26 | +## Before you begin |
| 27 | + |
| 28 | +Here's what you need to do before you add the connection: |
| 29 | + |
| 30 | +- Sign up for a LastPass business account to add a LastPass application. |
| 31 | +- Generate a SAML Metadata XML file as LastPass does not support hosting this for you (more information below). |
| 32 | + |
| 33 | +## Recommendations |
| 34 | + |
| 35 | +- Open the Kinde Enterprise connection in one browser tab, and the LastPass app configuration in another tab, as you will need to copy connection information across between them. |
| 36 | +- Set up and testing the connection in a non-production environment before making available to users. |
| 37 | + |
| 38 | +## Advanced configurations |
| 39 | + |
| 40 | +Depending on your SAML set up, you may need to include advanced configurations for your connection. See [Advanced SAML configurations](/authenticate/enterprise-connections/advanced-saml-configurations/) |
| 41 | + |
| 42 | +## Step 1: Add the connection in Kinde |
| 43 | + |
| 44 | +<Aside> |
| 45 | + |
| 46 | +You can make a connection available only to a specific organization, or you can create it so it can be used across any organization in your business. |
| 47 | + |
| 48 | +</Aside> |
| 49 | + |
| 50 | +### Add a connection for a specific organization |
| 51 | + |
| 52 | +1. Go to **Organizations** and open the organization. |
| 53 | +2. In the menu, select **Authentication**, then select **Add connection**. |
| 54 | +3. In the **Add connection** window, select **New enterprise connection**, then click **Next**. |
| 55 | +4. Select the LastPass connection and then select **Next**. |
| 56 | +5. Next: 'Step 2: Configure the connection'. |
| 57 | + |
| 58 | +### Add a connection that can be shared across multiple organizations |
| 59 | + |
| 60 | +1. Go to **Settings > Environment > Authentication**. |
| 61 | +2. Scroll to the **Enterprise connection** section and select **Add connection**. The **Add connection** window opens. |
| 62 | +3. Select the LastPass connection and then select **Next**. |
| 63 | +4. Next: 'Step 2: Configure the connection'. |
| 64 | + |
| 65 | +## Step 2: Configure the connection |
| 66 | + |
| 67 | +1. Enter a name for the connection. It should match the connection name in LastPass. |
| 68 | +2. Enter a random string value for Entity ID, for e.g. `870sa9fbasfasdas23aghkhc12zasfnasd`. |
| 69 | +3. Enter the **IdP metadata URL**. This URL comes from your identity provider. |
| 70 | + |
| 71 | + 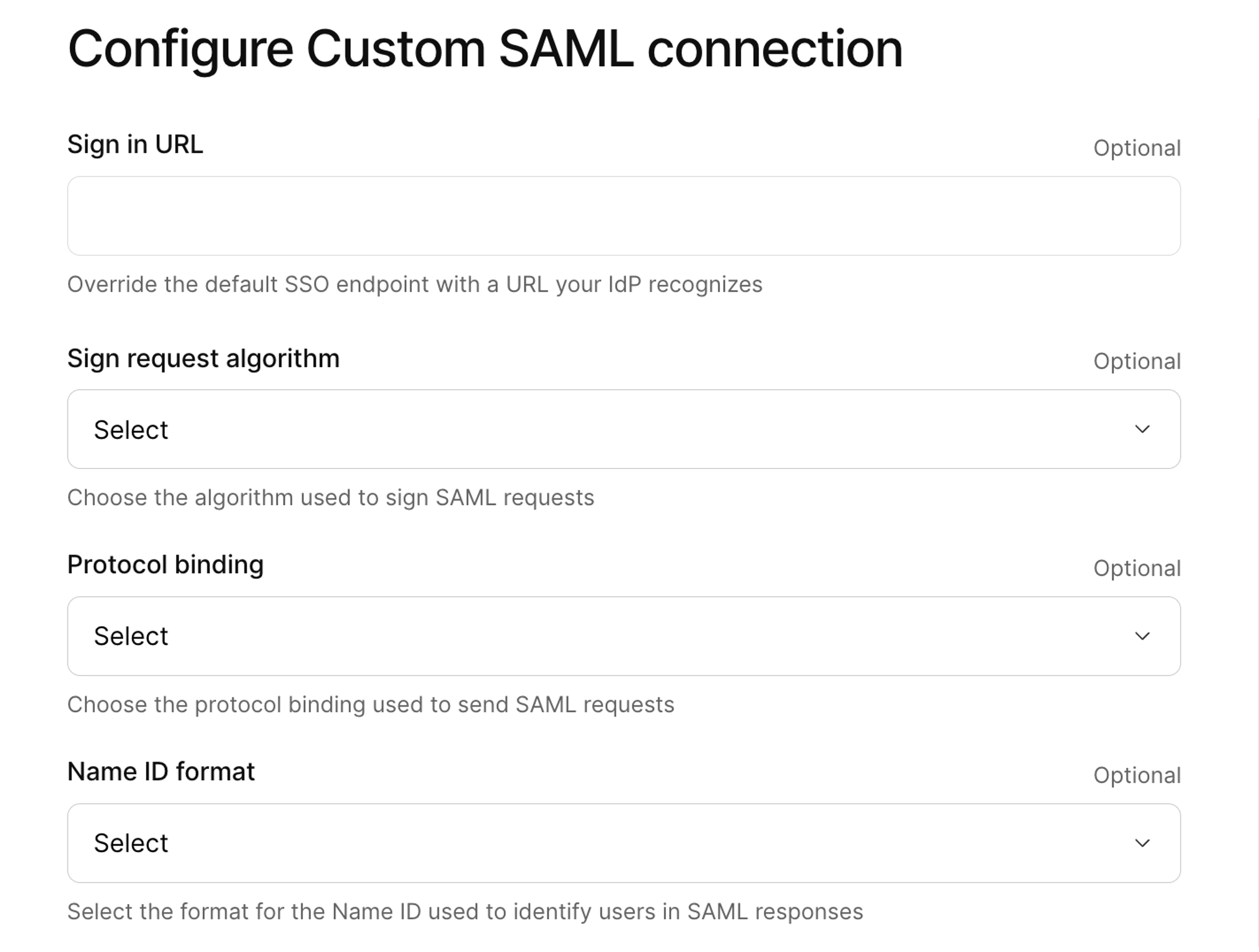 |
| 72 | + |
| 73 | +4. Enter a **sign in URL** if your IdP requires a specific URL. |
| 74 | +5. If you want, select the **Sign request algorithm** and **Protocol binding**. The options you choose will depend on what your identity provider prefers or requires. |
| 75 | +6. Select `Email` as the **Name ID** format. This helps identify and link user identities between your IdP and Kinde. |
| 76 | +7. Enter `emailAddress` as the **Email key attribute**. This is the attribute in the SAML token that contains the user’s email. Setting this value ensures that the email address returned in the SAML response is correctly retrieved. |
| 77 | +8. (Optional) Add a first name and last name key attribute. This is not necessary for LastPass. |
| 78 | + |
| 79 | + 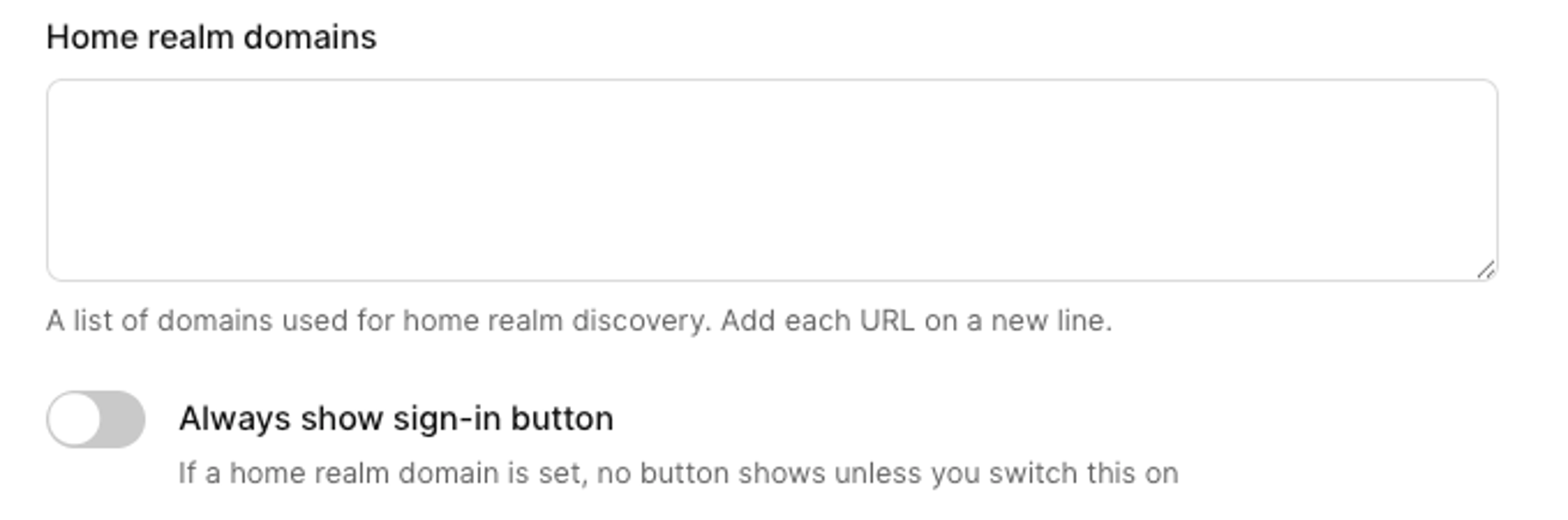 |
| 80 | + |
| 81 | +9. Enter any relevant **Home realm domains**. This is how SAML recognizes a user’s credentials and routes them to the correct sign in page. Note that home realm domains need to be unique across all connections in an environment. [Read more about home realm domains](/authenticate/enterprise-connections/home-realm-discovery/). |
| 82 | +10. If you use home realm domains, the sign in button is hidden on the auth screen by default. To show the SSO button, select the **Always show sign-in button** option. |
| 83 | + |
| 84 | + 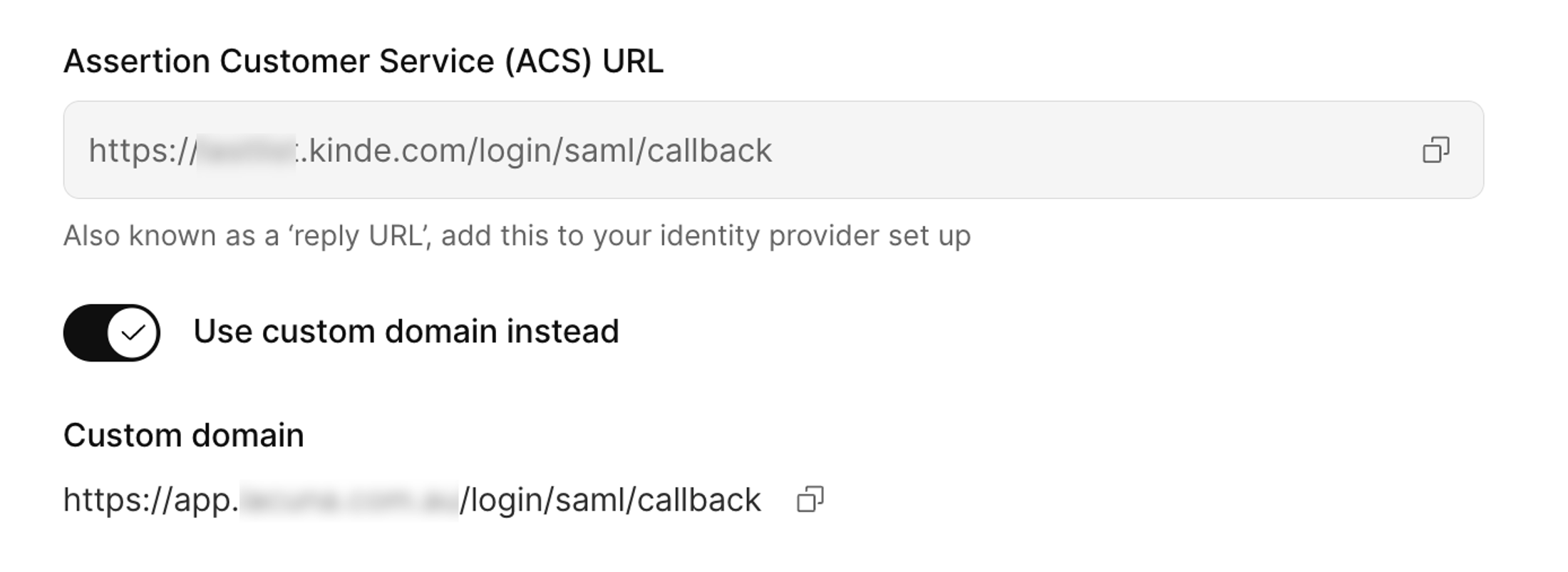 |
| 85 | + |
| 86 | +11. Copy the relevant reply URL: |
| 87 | + 1. If you don't use a custom domain, copy the **ACS URL**. |
| 88 | + 2. If you do use a custom domain, select the **Use custom domain instead** option and copy the custom domain URL. |
| 89 | + Later, add this URL to the LastPass configuration. |
| 90 | +12. If you want to enable just-in-time (JIT) provisioning for users, select the **Create a user record in Kinde** option. This saves time adding users manually or via API later. |
| 91 | + |
| 92 | + 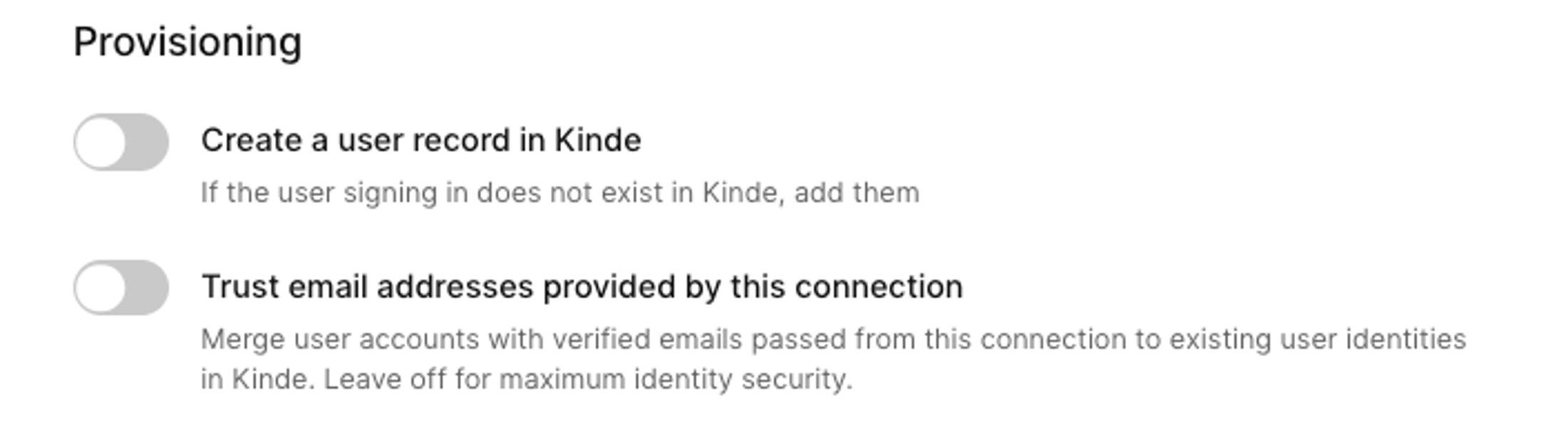 |
| 93 | + |
| 94 | +13. (Temporary feature) Select if you want to treat this connection as a trusted provider. A [trusted provider](/authenticate/about-auth/identity-and-verification/) is one that guarantees the email they issue is verified. |
| 95 | +14. (Optional) In the **Sign SAML request** section, paste in the **Signed certificate** and **Private key**. You may have got these from your IdP or you may have generated yourself (see procedure above). |
| 96 | +15. Enter any [upstream params](/authenticate/enterprise-connections/advanced-saml-configurations/#upstream-parameters) that you want to pass to the identity provider. Not all providers support this, so check their documentation first. |
| 97 | +16. Select **Save**. |
| 98 | + |
| 99 | +## Step 3: Add and configure your LastPass application |
| 100 | + |
| 101 | +View the [LastPass docs](https://support.lastpass.com/s/document-item?language=en_US&bundleId=lastpass&topicId=LastPass/uac_applications_sso_apps.html&_LANG=enus) for the full procedure. |
| 102 | + |
| 103 | +1. Sign in to your LastPass business account. |
| 104 | +2. In the menu, select **AdminConsole**. |
| 105 | +3. Go to **Applications**, then select **SSO apps**. |
| 106 | +4. Select **Search the catalogue**. A side panel slides out. |
| 107 | + |
| 108 | +  |
| 109 | + |
| 110 | +6. Follow the prompt to initialize SAML keys. This will take up to 15 minutes to process. |
| 111 | +7. Refresh the page and select **Search the catalogue** again. The side panel slides out showing a list. |
| 112 | +8. Scroll and select **Custom service**. |
| 113 | +9. Select **Add a new domain** if prompted. The configuration panel opens. |
| 114 | + |
| 115 | +  |
| 116 | + |
| 117 | +10. Enter a **Name** and select which groups will be able to sign in using this SSO connection. |
| 118 | +11. At the top of the **Configuration section** select **Export SAML IdP Metadata**. |
| 119 | +12. Select Copy or download, then select **OK**. |
| 120 | + |
| 121 | +  |
| 122 | + |
| 123 | +13. In the **Service Provider entity ID** field, enter the random ID you generated for the **Entity ID** in Kinde. |
| 124 | +14. In the **Assertion consumer service** field, enter the **ACS URL** or your custom domain, from Kinde. |
| 125 | +15. Make sure the **Name ID format** is `emailAddress` and the **Name ID** is `Email address'. |
| 126 | +16. Enter any custom attributes required. |
| 127 | + |
| 128 | +  |
| 129 | + |
| 130 | +17. Select **View key** under the **Key field**. |
| 131 | +18. Copy the key. You will need this to finishe setting up the Kinde connection. |
| 132 | +19. Make sure the **Service is enabled** option is selected. |
| 133 | +20. Select **Save**. |
| 134 | + |
| 135 | +## Step 4: Finish setting up your LastPass connection in Kinde |
| 136 | + |
| 137 | +1. Open the connection in Kinde. Go to **Organization > Authentication** or via **Settings > Authentication**. |
| 138 | +2. In the **IdP metadata URL** field paste the **IDP Entity ID** you copied from LastPass. |
| 139 | +3. In the **Sign-in URL** field paste the **Single Sign-on URL** you copied from LastPass. |
| 140 | +4. In the **Signing certificate** field paste the **IDP Metadata XML** file content. [@Viv not sure about this - is this where hosting the certificate is advised??] |
| 141 | +5. In the **Private key** field paste in the **Key** you copied from LastPass. |
| 142 | +6. Switch on the connection. This will make it instantly available to users if this is your production environment. |
| 143 | + 1. For environment-level connections, scroll down and select the apps that will use the auth method. |
| 144 | + 2. For organization-level connections, scroll down and select if you want to switch this on for the org. Note that it will be automatically available for all apps if you choose this option. |
| 145 | +7. Select **Save**. |
| 146 | + |
| 147 | +Test the connection works by trying to sign in to your test environment using this method. |
| 148 | +Re-test when you deploy the option to users. |
0 commit comments