|
| 1 | +--- |
| 2 | +page_id: a845b386-a747-4e1c-9862-71ede016f1ec |
| 3 | +title: Integrate fraud detection with TrustPath |
| 4 | +sidebar: |
| 5 | + order: 8 |
| 6 | +relatedArticles: |
| 7 | + - a07f8f6b-5d6a-4096-be52-7b13b4a3b0a5 |
| 8 | + - 7fe91aba-930c-4a63-8996-85af6bb605a7 |
| 9 | +--- |
| 10 | + |
| 11 | +This guide shows you how to build a Fraud Detection Workflow that runs after user authentication in **Kinde**, and uses **TrustPath** to detect and block potentially fraudulent sign-ins and sign-ups. |
| 12 | + |
| 13 | +The core idea: **whenever a user signs in or registers**, Kinde sends data to TrustPath. Based on the risk score it returns, Kinde allows or denies access. |
| 14 | + |
| 15 | +TrustPath works with Kinde workflows to trigger certain actions at key points in the authentication journey, using your own code. |
| 16 | + |
| 17 | +## What you need |
| 18 | + |
| 19 | +Here’s what you need to get started. |
| 20 | + |
| 21 | +- **Kinde account** - [Create one](https://app.kinde.com/register) for free if you haven’t already. You’ll also need to set up an application in Kinde. |
| 22 | +- **Kinde M2M application** - Create a [dedicated M2M app](https://docs.kinde.com/developer-tools/kinde-api/connect-to-kinde-api/) for accessing the Kinde Management API |
| 23 | +- **TrustPath account** - [Sign up](https://console.trustpath.io/login) here if you don’t have one. A free account does not require any payment information. |
| 24 | +- **TrustPath API access** - Grab an API key from the [TrustPath console](https://console.trustpath.io). |
| 25 | +- **Git repo for storing your code** - clone [this repository](https://github.com/trust-path/kinde-trustpath-integration-example). It contains integration code that is already prepared for use with this guide. |
| 26 | + |
| 27 | +## Step 1: Set up the workflow and connect your repo |
| 28 | + |
| 29 | +For a workflow to function in Kinde, the workflow files need to be structured and set up in a specific way. Refer to the docs to get this part right. |
| 30 | + |
| 31 | +1. [Create a new workflow](/workflows/getting-started/workflow-files/) or [clone a template workflow](https://github.com/trust-path/kinde-trustpath-integration-example). |
| 32 | +2. [Connect your GitHub repo](/workflows/getting-started/connect-repo-for-workflows/) to execute the workflow. |
| 33 | + |
| 34 | +## Step 2: Define the workflow entry point |
| 35 | + |
| 36 | +The workflow starts with a simple async function triggered after user authentication: |
| 37 | + |
| 38 | +```js |
| 39 | +export default async function FraudDetectionWorkflow(event: |
| 40 | +onPostAuthenticationEvent) { |
| 41 | +} |
| 42 | +``` |
| 43 | + |
| 44 | +The event parameter gives us initial context—such as the user ID, IP address, and whether this is a new user. But we need to enrich this data before we can send it to TrustPath. We’ll do this in the next step. |
| 45 | + |
| 46 | +## Step 3: Fetch full user data from Kinde |
| 47 | + |
| 48 | +To make an informed decision, TrustPath. needs more than a user ID—it also needs the user's email, first name, and last name. To get this data from Kinde, do the following. |
| 49 | + |
| 50 | +1. [Set up an M2M application](/developer-tools/kinde-api/connect-to-kinde-api/) to access the Kinde Management API and switch on the `read:users` scope. |
| 51 | +2. Copy the Client ID and Client secret from the above application. |
| 52 | +3. Create two new [environment variables](/workflows/configuration/environment-variables-and-secrets/) in Kinde. Go to **Settings > Data management > Env variables**. |
| 53 | +4. Add the following variables: |
| 54 | + |
| 55 | + |
| 56 | + | Key | Value | Sensitive | |
| 57 | + | --- | --- | --- | |
| 58 | + | KINDE_WF_M2M_CLIENT_ID | Copy from M2M application | No | |
| 59 | + | KINDE_WF_M2M_CLIENT_SECRET | Copy from M2M application | Yes | |
| 60 | + |
| 61 | +Once these are set up, you can retrieve the additional data you need, using the `createKindeAPI` helper from [@kinde/infrastructure](https://github.com/kinde-oss/infrastructure), which allows us to call the Kinde Management API: |
| 62 | + |
| 63 | +```js |
| 64 | +const kindeAPI = await createKindeAPI(event); |
| 65 | +const user = await getUserData(kindeAPI, event.context.user.id); |
| 66 | +async function getUserData(kindeAPI: any, userId: string) { |
| 67 | +const { data: user } = |
| 68 | +await kindeAPI.get({ endpoint: `user?id=${userId}` }); |
| 69 | +return user; |
| 70 | +} |
| 71 | +``` |
| 72 | + |
| 73 | +## Step 4: Set up your TrustPath API key |
| 74 | + |
| 75 | +**TrustPath** requires an API key to authenticate your requests, in this case a request that originates from the Kinde workflow. To get your API Key: |
| 76 | + |
| 77 | +1. Log in to the [TrustPath Console](https://console.trustpath.io). |
| 78 | +2. On the left-hand menu, go to **[Your Name] > API Keys**. |
| 79 | +3. Copy either one of the API keys provided there. |
| 80 | + |
| 81 | +(Recommended) Store the API key securely as an [environment variable](/workflows/configuration/environment-variables-and-secrets/) in **Kinde**, just like the other variables mentioned above. |
| 82 | + |
| 83 | +```js |
| 84 | +const trustPathAPIKey = getEnvironmentVariable("TRUSTPATH_API_KEY")?.value; |
| 85 | +``` |
| 86 | +
|
| 87 | +This ensures you’re not hardcoding sensitive credentials, and it keeps your app secure and maintainable. |
| 88 | +
|
| 89 | +## Step 5: Determine the event type |
| 90 | +
|
| 91 | +TrustPath evaluates risk differently based on the event type. For example, account creation versus account sign in. |
| 92 | +
|
| 93 | +```js |
| 94 | +const isNewUser = event.context.auth.isNewUserRecordCreated; |
| 95 | +const eventType = isNewUser ? "account_register" : "account_login"; |
| 96 | +``` |
| 97 | +
|
| 98 | +We check whether the user is new and set the event type accordingly: |
| 99 | +
|
| 100 | +- `account_register`: Used for new sign-ups - typically includes more rigorous fraud checks. |
| 101 | +- `account_login`: Used for existing users - can focus on things like account takeover detection. |
| 102 | +
|
| 103 | +By classifying the event properly, you can take advantage of TrustPath's specialized rule sets. |
| 104 | +
|
| 105 | +## Step 6: Define TrustPath threat detection rules |
| 106 | +
|
| 107 | +TrustPath threat detection rules are individual risk assessment criteria designed to identify fraudulent activities. Each rule analyzes specific signals to detect suspicious behavior and assigns a risk score to the event. |
| 108 | +
|
| 109 | +Each risk detected then contributes to the total risk score, which ranges from 0 to 100. |
| 110 | +
|
| 111 | +- A score of 0 means no risk (approve) |
| 112 | +- A score of 100 means very risky (decline) |
| 113 | +
|
| 114 | +You need to set up separate rules for `account_register` and `account_login` events. |
| 115 | +
|
| 116 | +Select **Threat Rules** from the menu and choose the card labeled **Account Register** to configure it. TrustPath offers the flexibility to add your own rules, but it also provides default rules tailored to each event type. |
| 117 | +
|
| 118 | +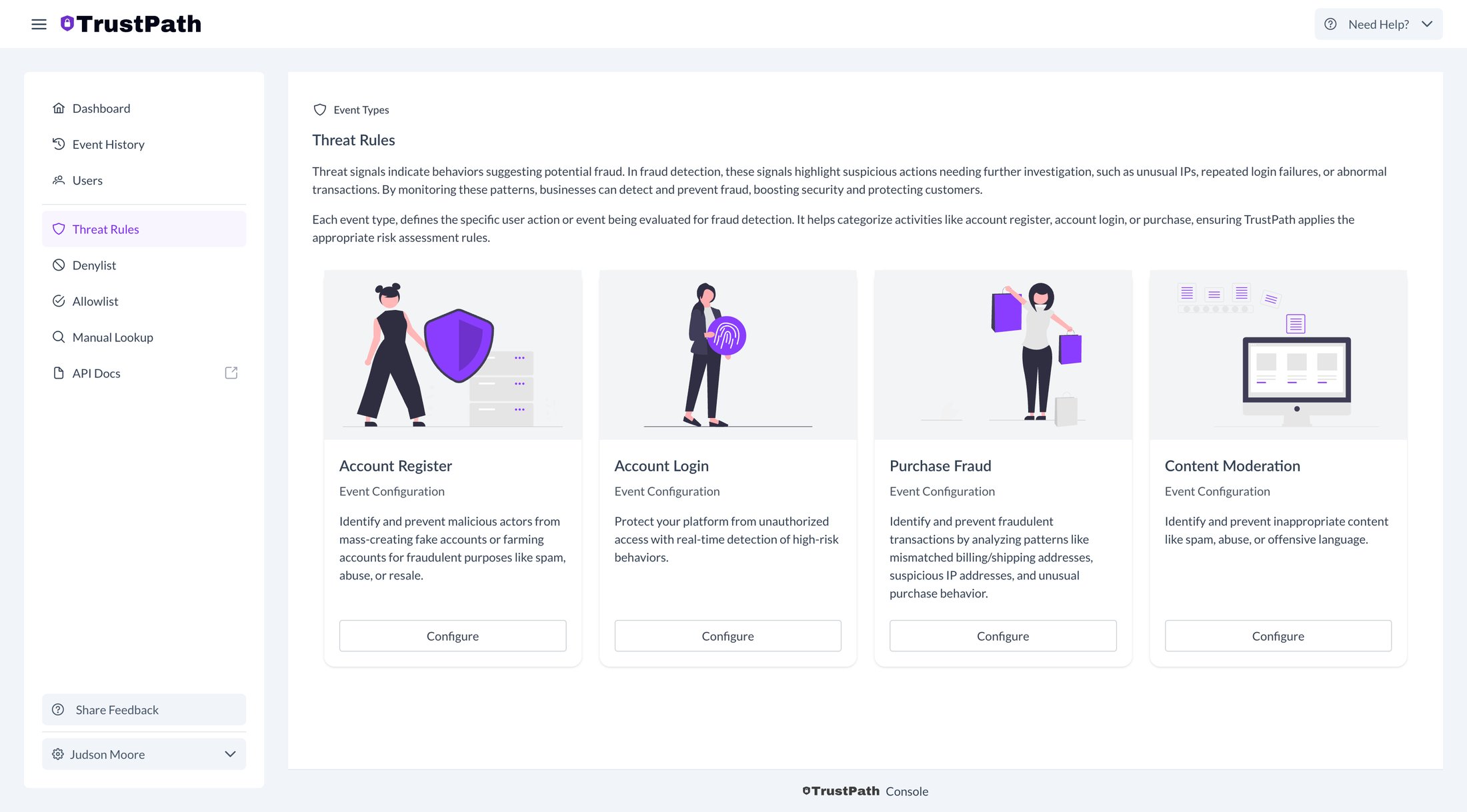 |
| 119 | +
|
| 120 | + |
| 121 | +
|
| 122 | +Here’s an example of how to add a rule for the account register event. |
| 123 | +
|
| 124 | +1. Select **Add Rule From Library** in the top right corner. |
| 125 | +2. From the list, select the following rules by clicking on each rule: |
| 126 | + - Email addresses are disposable. |
| 127 | + - IP Address is a Tor exit node. |
| 128 | + - Email server IP addresses have abuse reports. |
| 129 | +
|
| 130 | +This will enable any new account registration on Kinde to perform IP and email threat signal checks. |
| 131 | +
|
| 132 | +Next, configure rules for the account log in event. For this, we want to prevent users from entering the system with disposable email addresses, as well as detect rapid IP changes, which can be a sign of unusual behavior. |
| 133 | +
|
| 134 | +Here’s where you configure rules for the `account_login` event. |
| 135 | +
|
| 136 | +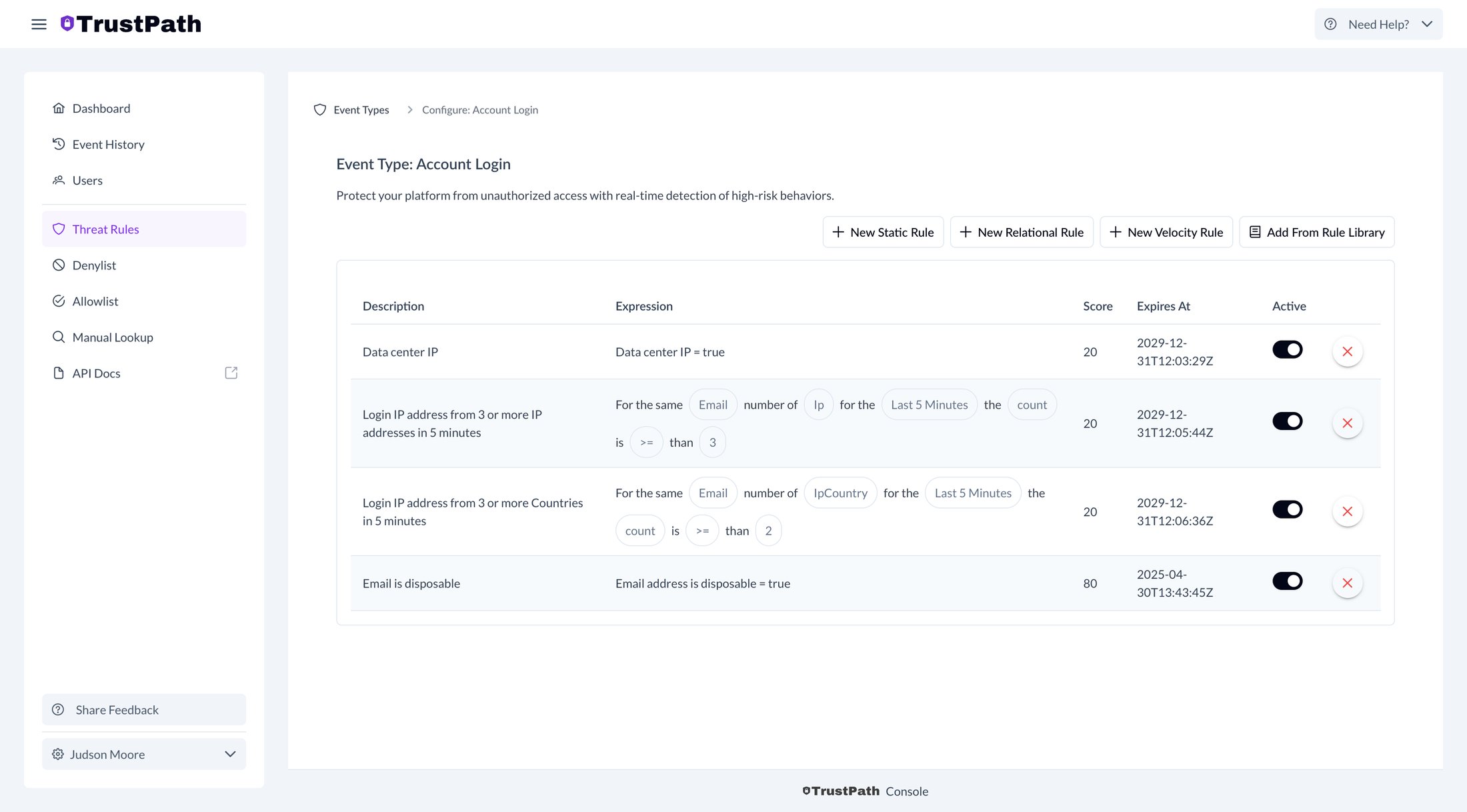 |
| 137 | +
|
| 138 | +You can see we have some rules switched on, and each rule has a score. |
| 139 | +
|
| 140 | +The example above detects rapid IP changes and blocks users by assigning a high risk score, which signals potential issues. |
| 141 | +
|
| 142 | +### Advanced rule configuration |
| 143 | +
|
| 144 | +The above rule can be strengthened by adding browser fingerprinting to IP change detection. For instance, the rule might be: “*if the same user email sees more than three different IP addresses within five minutes **and** also has a new browser fingerprint”*, it’s a stronger signal of suspicious activity. |
| 145 | +
|
| 146 | +When set up, this detects a user logging in from multiple locations or while traveling—where the IP may change, but the browser fingerprint typically remains consistent if they’re using the same device. |
| 147 | +
|
| 148 | +TrustPath supports many advanced configurations like this. You can contact their team to help you set up any complex rules you want. |
| 149 | +
|
| 150 | +## Step 7: Build the request body |
| 151 | +
|
| 152 | +Now that we have the user info and event type, we can build the payload to send to TrustPath when the workflow is triggered. |
| 153 | +
|
| 154 | +```js |
| 155 | +const requestBody = { |
| 156 | +ip: event.request.ip.split(",")[0].trim(), // Handles cases where multiple IPs are forwarded |
| 157 | +email: user.preferred_email, |
| 158 | +user: { |
| 159 | +user_id: event.context.user.id, |
| 160 | +first_name: user.first_name, |
| 161 | +last_name: user.last_name, |
| 162 | + |
| 163 | +}, |
| 164 | +event_type: eventType, |
| 165 | +}; |
| 166 | +``` |
| 167 | +
|
| 168 | +This information passed in the request body allows TrustPath to cross-reference behavioral history, analyze IP risk, and more. |
| 169 | +
|
| 170 | +## Step 8: Call the TrustPath Risk API |
| 171 | +
|
| 172 | +Once the connection is set up between APIs, data is ready to be sent to TrustPath via a standard HTTP POST request. Here’s an example: |
| 173 | +
|
| 174 | +```js |
| 175 | +const response = await kinde.fetch( |
| 176 | + "https://api.trustpath.io/v1/risk/evaluate", |
| 177 | + { |
| 178 | + method: "POST", |
| 179 | + responseFormat: "json", |
| 180 | + headers: { |
| 181 | + Authorization: `Bearer ${trustPathAPIKey}`, |
| 182 | + "Content-Type": "application/json", |
| 183 | + }, |
| 184 | + body: JSON.stringify(requestBody), |
| 185 | + } |
| 186 | +); |
| 187 | +``` |
| 188 | +
|
| 189 | +This request is made using `kinde.fetch`, which handles outbound API calls securely within the workflow context. |
| 190 | +
|
| 191 | +## Step 9: Evaluate the response and take action |
| 192 | +
|
| 193 | +When the API call to TrustPath comes back, the response will include a state field showing one of three values: |
| 194 | +
|
| 195 | +- **approve** - let the user through |
| 196 | +- **review** - optionally flags cases for manual review |
| 197 | +- **decline** - block access |
| 198 | +
|
| 199 | +Here's how to enforce a block for declined requests: |
| 200 | +
|
| 201 | +```js |
| 202 | +const state = response.json.data.score.state; |
| 203 | + |
| 204 | +if (state === "decline") { |
| 205 | +denyAccess( |
| 206 | +"You are not allowed to access this resource. Request declined by TrustPath.io" |
| 207 | +); |
| 208 | +} |
| 209 | +``` |
| 210 | +
|
| 211 | +You can adapt this to handle review flags differently, or to just mark it for review. |
| 212 | +
|
| 213 | +## Step 10: Test your fraud detection setup |
| 214 | +
|
| 215 | +Now that everything is set up, we can test the entire flow. Starting with the `account_register event`, select a disposable email address (choosing any from your favorite search engine should be sufficient) and try to create a new account on Kinde. |
| 216 | +
|
| 217 | +Once everything is set up and deployed: |
| 218 | +
|
| 219 | +1. Log in or register using your test account |
| 220 | +2. Check TrustPath's Event History to see the result |
| 221 | +3. By default, new accounts will return **approve** until you define threat rules in TrustPath. |
| 222 | +
|
| 223 | +You can also test the `account_login` event by simulating logins from different IP addresses—using a VPN is a simple way to do this. |
| 224 | +
|
| 225 | +## Support |
| 226 | +
|
| 227 | +If you need extra support, here’s where to get it. |
| 228 | +
|
| 229 | +- **TrustPath support:** For questions related to fraud detection rules, API integration, or threat analysis, visit **TrustPath**, [contact the TrustPath team](https://trustpath.io/contact), or view the TrustPath [API docs](https://docs.trustpath.io/). |
| 230 | +- **Kinde support:** For help with authentication workflows, triggers, or general setup, refer to the [Kinde docs](https://docs.kinde.com/) or reach out to [our support team](https://kinde.com/support/). |
| 231 | +
|
| 232 | +TrustPath is a German-based company. Their team wrote this guide to help Kinde users. |
0 commit comments