You signed in with another tab or window. Reload to refresh your session.You signed out in another tab or window. Reload to refresh your session.You switched accounts on another tab or window. Reload to refresh your session.Dismiss alert
4. If Microsoft is your provider and your app is a bit older, you may need to add spn: to the beginning of the Entity ID string in Kinde, e.g. `spn:5836g209gbhw09r8y0913`. This is not required for newly created apps.
63
+
4. If Microsoft is your provider and your app is a bit older, you may need to add `spn:` to the beginning of the **Entity ID** string in Kinde, e.g. `spn:5836g209gbhw09r8y0913`. This is not required for newly created apps.
65
64
5. Enter the **IdP metadata URL**. This URL comes from your identity provider.
66
-
6. Enter an **Email key attribute**. This is the attribute in the SAML token that contains the user’s email. Setting this value ensures that the email address returned in the SAML response is correctly retrieved. We do not recommend leaving this field blank, but if you do we will set ‘email’ as the attribute.
67
-
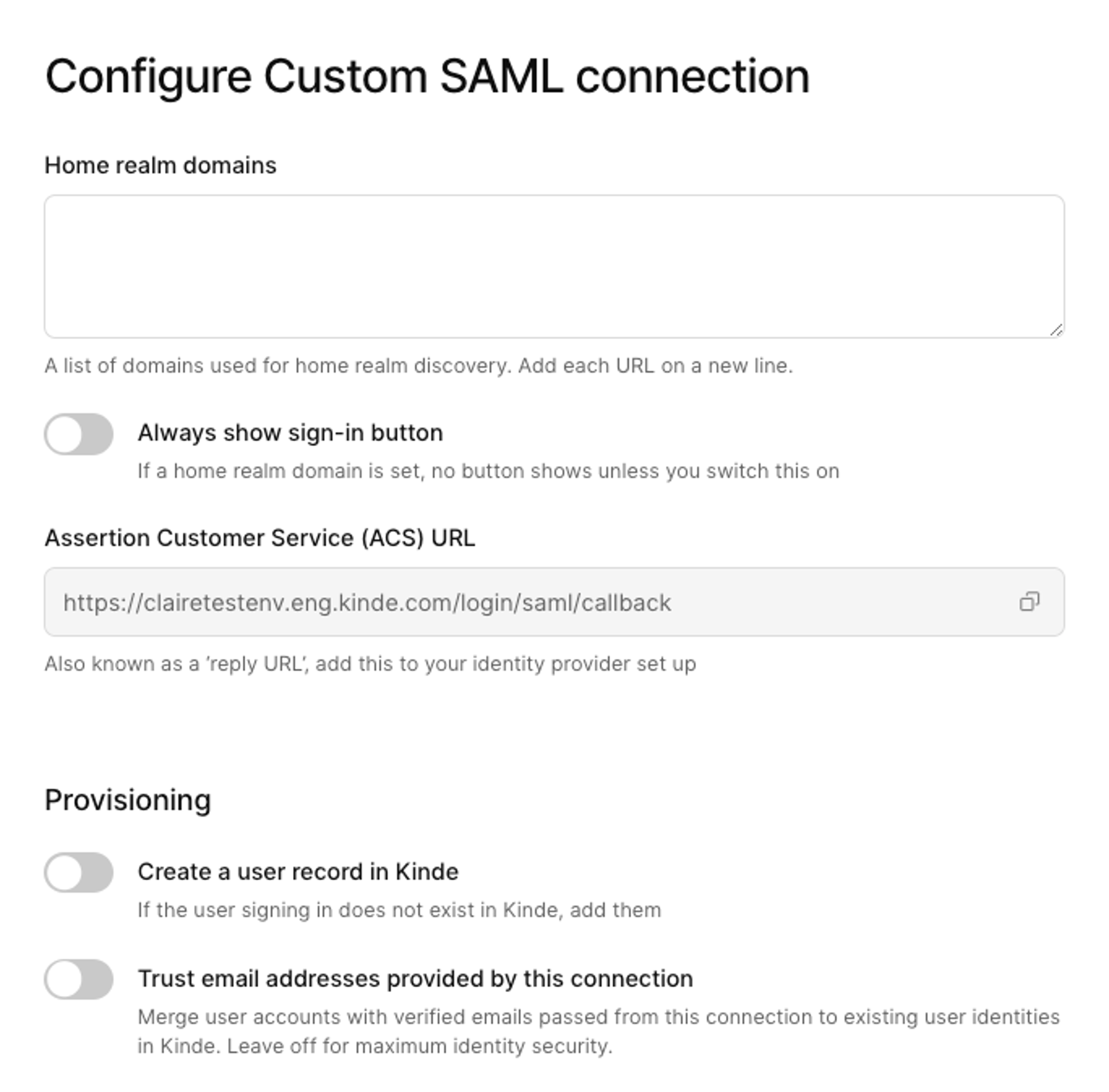
7. Enter any relevant **Home realm domains**. This is how SAML recognizes a user’s credentials and routes them to the correct sign in page. Note that home realm domains need to be unique across all connections in an environment. [Read more about home realm domains](/authenticate/enterprise-connections/home-realm-discovery/).
65
+
6. Enter a **sign in URL** if your IdP requires a specific URL.
66
+
7. Enter an **Email key attribute**. This is the attribute in the SAML token that contains the user’s email. Setting this value ensures that the email address returned in the SAML response is correctly retrieved. We do not recommend leaving this field blank, but if you do we will set ‘email’ as the attribute.
67
+
8. (Optional) add a first name and last name attribute.
68
+
9. Enter any relevant **Home realm domains**. This is how SAML recognizes a user’s credentials and routes them to the correct sign in page. Note that home realm domains need to be unique across all connections in an environment. [Read more about home realm domains](/authenticate/enterprise-connections/home-realm-discovery/).
68
69
69
70
70
71
71
-
8. If you use home realm domains, the sign in button is hidden on the auth screen by default. To show the SSO button, select the **Always show sign-in button** option.
72
+
10. If you use home realm domains, the sign in button is hidden on the auth screen by default. To show the SSO button, select the **Always show sign-in button** option.
72
73
73
-
9. Copy the **ACS URL**, which is also known as a reply URL. This will need to be copied to the relevant area of your identity provider configuration.
74
-
10. If you want to enable just-in-time (JIT) provisioning for users, select the **Create a user record in Kinde** option. This saves time adding users manually or via API later.
75
-
11. (Optional) In the **Sign SAML request** section, paste in the **Signed certificate** and **Private key**. You may have got these from your IdP or you may have generated yourself (see procedure above).
76
-
12. Switch on the connection. This will make it instantly available to users if this is your production environment.
74
+
11. Copy the **ACS URL**, which is also known as a reply URL. This will need to be copied to the relevant area of your identity provider configuration.
75
+
12. If you want to enable just-in-time (JIT) provisioning for users, select the **Create a user record in Kinde** option. This saves time adding users manually or via API later.
76
+
13. (Optional) In the **Sign SAML request** section, paste in the **Signed certificate** and **Private key**. You may have got these from your IdP or you may have generated yourself (see procedure above).
77
+
14. Switch on the connection. This will make it instantly available to users if this is your production environment.
77
78
1. For environment-level connections, scroll down and select the apps that will use the auth method.
78
79
2. For organization-level connections, scroll down and select if you want to switch this on for the org.
79
-
13. Select **Save**.
80
+
15. Select **Save**.
80
81
81
82
Next: Complete any additional configuration in your identity provider’s settings, such as adding the **Entity ID** and **ACS URL**.
82
83
83
-
## Test the connection
84
+
## Step 3: Test the connection
84
85
85
86
Once you have entered the ACS URL in your identity provider, the connection should be enabled.
0 commit comments