Is it fine for the next-auth.session-token to be publicly visible?
#2533
-
|
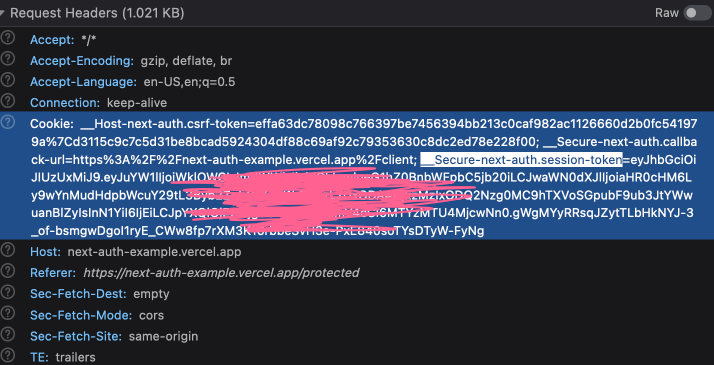
I'm working on a Twitter based app which also uses user's access token and secret. The issue is in the session and other API route which accesses JWT token, their response has response headers something like below(this is from Twitter login on https://next-auth-example.vercel.app/ example): My question is I'm able to use the |
Beta Was this translation helpful? Give feedback.
Replies: 2 comments 1 reply
-
|
The token is saved as a JWT by default, signed but not encrypted in an HTTPOnly secure cookie, which can only be read server-side. If you take that cookie though and paste it into https://jwt.io/ for example, you will be able to see the content pretty easily. JWTs are meant to be self-contained, meaning once issued, they don't need communication with any server to be valid. They come with an expiry date, after which the server shouldn't accept them anymore. Some services can also revoke tokens, by maintaining a list of the revoked tokens until they expire, but this adds extra processing time. Alternatively, you can use a database persisted session, which has its own drawbacks/advantages. |
Beta Was this translation helpful? Give feedback.
-
|
I fixed the issue by adding a check for session in the API route so only the app can make request. This is the video I followed for ref: https://www.youtube.com/watch?v=5wjuar9AU-0 |
Beta Was this translation helpful? Give feedback.
The token is saved as a JWT by default, signed but not encrypted in an HTTPOnly secure cookie, which can only be read server-side. If you take that cookie though and paste it into https://jwt.io/ for example, you will be able to see the content pretty easily.
JWTs are meant to be self-contained, meaning once issued, they don't need communication with any server to be valid. They come with an expiry date, after which the server shouldn't accept them anymore. Some services can also revoke tokens, by maintaining a list of the revoked tokens until they expire, but this adds extra processing time.
next-authlets you encrypt that JWT optionally https://next-auth.js.org/configuration/options#jso…