|
1 | | -# Sysdig CloudVision for AWS |
| 1 | +# Sysdig Secure for Cloud in AWS - Cloudformation Templates |
2 | 2 |
|
3 | | -This repository contains the CloudFormation templates to deploy the Sysdig |
4 | | -CloudVision suite in an AWS Account using ECS or AppRunner. |
| 3 | +This repository contains the CloudFormation templates to deploy [Sysdig Secure for Cloud](https://docs.sysdig.com/en/docs/sysdig-secure/sysdig-secure-for-cloud/) |
| 4 | +suite. |
5 | 5 |
|
6 | | -**[Deploy ECS latest version!](https://console.aws.amazon.com/cloudformation/home#/stacks/quickCreate?stackName=Sysdig-CloudVision&templateURL=https://cf-templates-cloudvision-ci.s3-eu-west-1.amazonaws.com/ecs/latest/entry-point.yaml)** |
| 6 | +## UseCases |
7 | 7 |
|
8 | | -**[Deploy AppRunner latest version!](https://console.aws.amazon.com/cloudformation/home#/stacks/quickCreate?stackName=Sysdig-CloudVision&templateURL=https://cf-templates-cloudvision-ci.s3-eu-west-1.amazonaws.com/apprunner/latest/entry-point.yaml)** |
| 8 | +If you're unsure about what/how to use this module, please fill the [questionnaire](https://github.com/sysdiglabs/terraform-aws-secure-for-cloud/blob/master/use-cases/_questionnaire.md) report as an issue and let us know your context, we will be happy to help and improve our module. |
9 | 9 |
|
10 | | -## Contribute |
| 10 | +### Single-Account |
11 | 11 |
|
| 12 | +Deploy the latest versions using one of the workloads that most suit you: |
12 | 13 |
|
13 | | -### Release |
| 14 | +#### ECS-based workload |
14 | 15 |
|
15 | | -Templates are [uploaded on the CI release cycle](https://github.com/sysdiglabs/aws-cloudvision-templates/blob/main/.github/workflows/release.yaml#L63) to `cf-templates-cloudvision-ci` on Sysdig `draios-demo` account. |
| 16 | +[Template for ECS workload](https://console.aws.amazon.com/cloudformation/home#/stacks/quickCreate?stackName=Sysdig-CloudVision&templateURL=https://cf-templates-cloudvision-ci.s3-eu-west-1.amazonaws.com/ecs/latest/entry-point.yaml) |
| 17 | + |
| 18 | +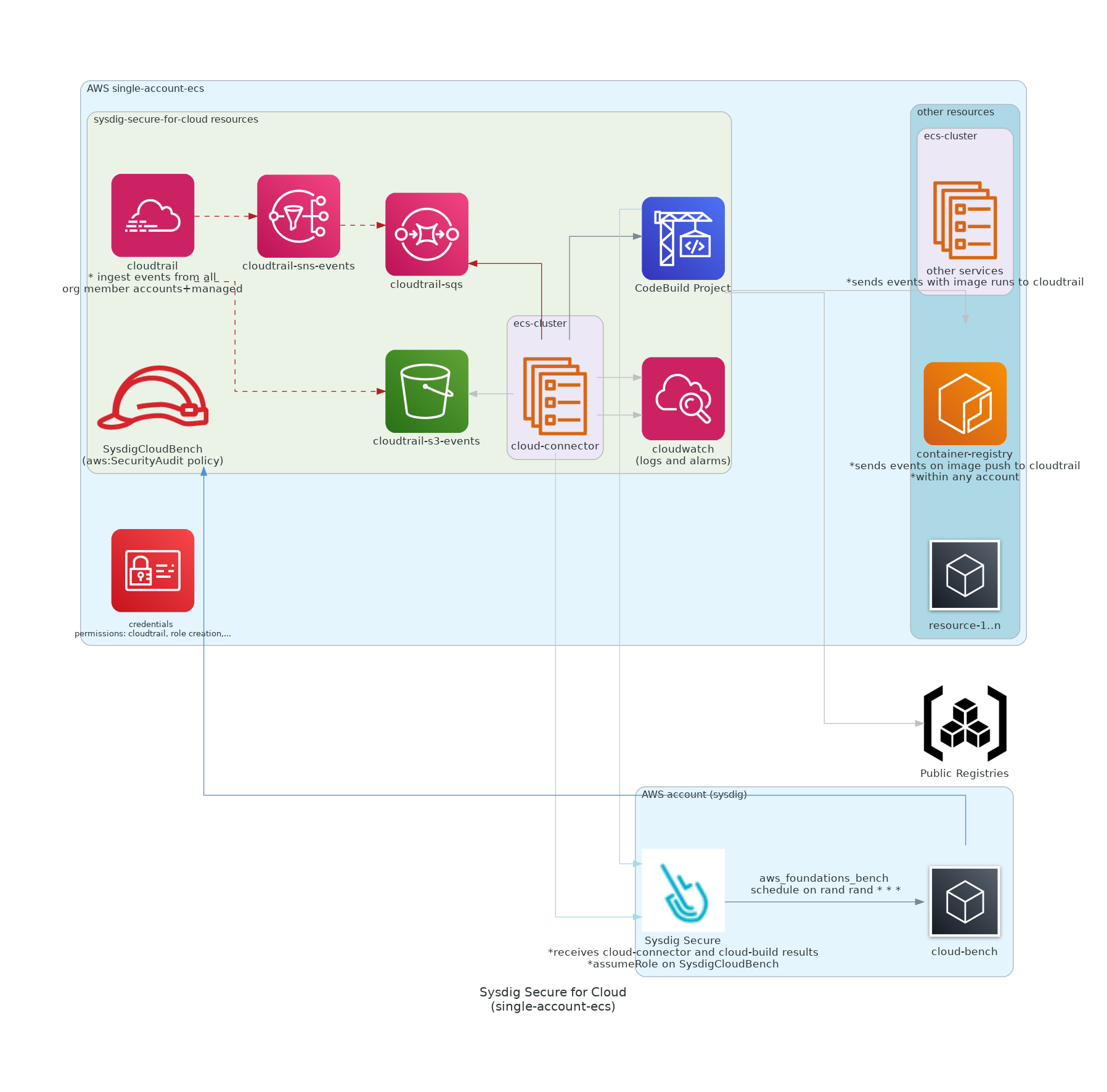 |
16 | 19 |
|
17 | | -Leading to the latest entry-point, which will be used on the Sysdig Secure > Getting Started > AWS Cloudformation |
18 | | -<br/>`https://cf-templates-cloudvision-ci.s3-eu-west-1.amazonaws.com/master/entry-point.yaml` |
19 | 20 |
|
| 21 | +#### AppRunner-based workload |
20 | 22 |
|
21 | | -### Pull Request |
| 23 | +Less resource-demanding and economic deployment (ECS requires VPCs and Gateways), but Apprunner is not available on all regions yet |
22 | 24 |
|
23 | | -When the PR is drafted, a new template will be available for testing: |
24 | | -- For ECS |
25 | | - <br/>`https://cf-templates-cloudvision-ci.s3-eu-west-1.amazonaws.com/ecs/pr/<PR_NAME>/entry-point.yaml` |
26 | | -- For AppRunner |
27 | | - <br/>`https://cf-templates-cloudvision-ci.s3-eu-west-1.amazonaws.com/apprunner/pr/<PR_NAME>/entry-point.yaml` |
| 25 | +[Template for AppRunner workload](https://console.aws.amazon.com/cloudformation/home#/stacks/quickCreate?stackName=Sysdig-CloudVision&templateURL=https://cf-templates-cloudvision-ci.s3-eu-west-1.amazonaws.com/apprunner/latest/entry-point.yaml) |
28 | 26 |
|
| 27 | +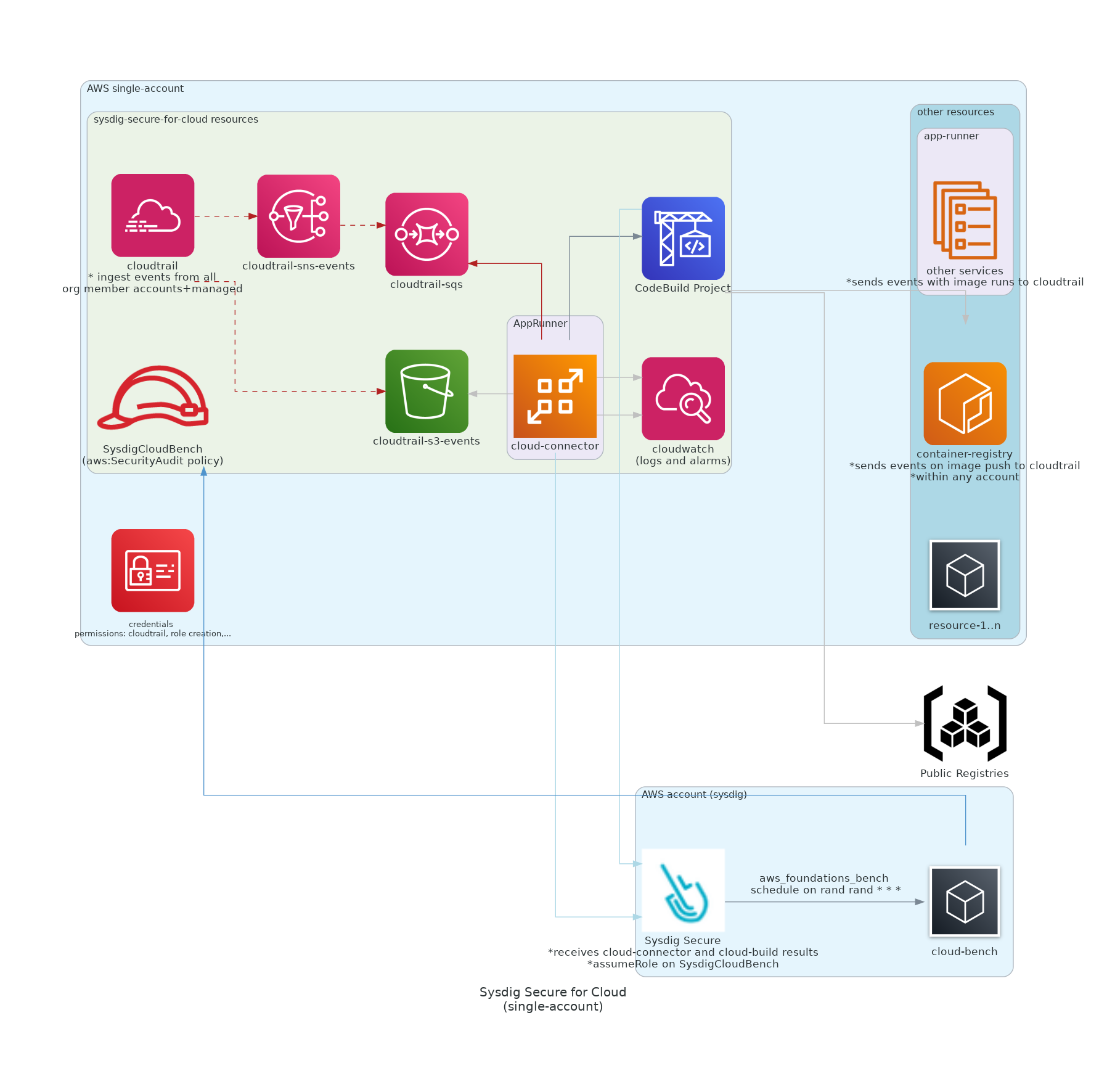 |
29 | 28 |
|
30 | | -### Testing |
31 | 29 |
|
32 | | -see [Makefile](templates_ecs/Makefile) |
| 30 | +If needed, we also have an <a href="https://github.com/sysdiglabs/terraform-aws-secure-for-cloud">Sysdig Secure for Cloud Terraform version</a> |
33 | 31 |
|
34 | | -#### Validation |
35 | 32 |
|
36 | | -ECS: |
| 33 | +## Organizational |
37 | 34 |
|
38 | | -```bash |
39 | | -$ aws cloudformation validate-template --template-body file://./templates_ecs/CloudVision.yaml |
40 | | -``` |
| 35 | +No official templates available yet. |
41 | 36 |
|
42 | | -AppRunner: |
| 37 | +Find some [organizational use-case](./use_cases/org-k8s) as reference and contact us for support. |
43 | 38 |
|
44 | | -```bash |
45 | | -$ aws cloudformation validate-template --template-body file://./templates_apprunner/SecureForCloudAppRunner.yaml |
46 | | -``` |
| 39 | +--- |
| 40 | +## Authors |
47 | 41 |
|
48 | | -#### Launch Template |
| 42 | +Module is maintained and supported by [Sysdig](https://sysdig.com). |
49 | 43 |
|
50 | | -ECS full cycle: |
51 | | - |
52 | | -``` |
53 | | --- test |
54 | | -$ aws cloudformation delete-stack --stack-name test ; \ |
55 | | -sleep 10 ; \ |
56 | | -aws cloudformation deploy --template-file templates_ecs/CloudVision.yaml --stack-name test ; \ |
57 | | -aws cloudformation describe-stack-events --stack-name test |
58 | | -``` |
59 | | - |
60 | | -AppRunner full cycle: |
61 | | - |
62 | | -``` |
63 | | --- test |
64 | | -$ aws cloudformation delete-stack --stack-name test ; \ |
65 | | -sleep 10 ; \ |
66 | | -aws cloudformation deploy --template-file templates_apprunner/SecureForCloudAppRunner.yaml --stack-name test ; \ |
67 | | -aws cloudformation describe-stack-events --stack-name test |
68 | | -``` |
69 | | - |
70 | | -#### Test Template wizard (UI) |
71 | | - ``` |
72 | | - Aws console > cloudformation > create new stack (template, upload template: select ./templates/Cloudvision.yaml) |
73 | | - ``` |
74 | | - - note: this will upload the template into an s3 bucket, remember to delete it afterwards |
75 | | - |
76 | | - |
77 | | -#### Cleanup |
78 | | - |
79 | | -Delete stack to clean test environment. [CFT limitation does not allow to automatically delete non-empty S3 bucket](https://docs.aws.amazon.com/AWSCloudFormation/latest/UserGuide/aws-properties-s3-bucket.html), so Stack deletion will fail when you request it. Delete S3 bucket manually and relaunch deletion for a full cleanup. |
| 44 | +## License |
80 | 45 |
|
| 46 | +Apache 2 Licensed. See LICENSE for full details. |
0 commit comments