diff --git a/README.md b/README.md
index 27eb8e56a..46345450d 100644
--- a/README.md
+++ b/README.md
@@ -918,7 +918,7 @@ module "cluster_pattern" {
| [clusters](#input\_clusters) | A list describing clusters workloads to create |
list( object({ name = string # Name of Cluster vpc_name = string # Name of VPC subnet_names = list(string) # List of vpc subnets for cluster workers_per_subnet = number # Worker nodes per subnet. machine_type = string # Worker node flavor kube_type = string # iks or openshift kube_version = optional(string) # Can be a version from `ibmcloud ks versions` or `default` entitlement = optional(string) # entitlement option for openshift secondary_storage = optional(string) # Secondary storage type pod_subnet = optional(string) # Portable subnet for pods service_subnet = optional(string) # Portable subnet for services resource_group = string # Resource Group used for cluster cos_name = optional(string) # Name of COS instance Required only for OpenShift clusters access_tags = optional(list(string), []) boot_volume_crk_name = optional(string) # Boot volume encryption key name disable_public_endpoint = optional(bool, true) # disable cluster public, leaving only private endpoint disable_outbound_traffic_protection = optional(bool, false) # public outbound access from the cluster workers cluster_force_delete_storage = optional(bool, false) # force the removal of persistent storage associated with the cluster during cluster deletion operating_system = string # The operating system of the workers in the default worker pool. See https://cloud.ibm.com/docs/openshift?topic=openshift-openshift_versions#openshift_versions_available . kms_wait_for_apply = optional(bool, true) # make terraform wait until KMS is applied to master and it is ready and deployed verify_cluster_network_readiness = optional(bool, true) # Flag to run a script will run kubectl commands to verify that all worker nodes can communicate successfully with the master. If the runtime does not have access to the kube cluster to run kubectl commands, this should be set to false. use_ibm_cloud_private_api_endpoints = optional(bool, true) # Flag to force all cluster related api calls to use the IBM Cloud private endpoints. allow_default_worker_pool_replacement = optional(bool) # (Advanced users) Set to true to allow the module to recreate a default worker pool. If you wish to make any change to the default worker pool which requires the re-creation of the default pool follow these [steps](https://github.com/terraform-ibm-modules/terraform-ibm-base-ocp-vpc?tab=readme-ov-file#important-considerations-for-terraform-and-default-worker-pool). labels = optional(map(string)) # A list of labels that you want to add to the default worker pool. enable_ocp_console = optional(bool) # Flag to specify whether to enable or disable the OpenShift console. If set to `null` the module will not modify the setting currently set on the cluster. Bare in mind when setting this to `true` or `false` on a cluster with private only endpoint enabled, the runtime must be able to access the private endpoint. addons = optional(object({ # Map of OCP cluster add-on versions to install debug-tool = optional(string) image-key-synchronizer = optional(string) openshift-data-foundation = optional(string) vpc-file-csi-driver = optional(string) static-route = optional(string) cluster-autoscaler = optional(string) vpc-block-csi-driver = optional(string) ibm-storage-operator = optional(string) }), {}) manage_all_addons = optional(bool, false) # Instructs Terraform to manage all cluster addons, even if addons were installed outside of the module. If set to 'true' this module will destroy any addons that were installed by other sources. kms_config = optional( object({ crk_name = string # Name of key private_endpoint = optional(bool) # Private endpoint }) ) worker_pools = optional( list( object({ name = string # Worker pool name vpc_name = string # VPC name workers_per_subnet = number # Worker nodes per subnet flavor = string # Worker node flavor subnet_names = list(string) # List of vpc subnets for worker pool entitlement = optional(string) # entitlement option for openshift secondary_storage = optional(string) # Secondary storage type boot_volume_crk_name = optional(string) # Boot volume encryption key name operating_system = string # The operating system of the workers in the worker pool. See https://cloud.ibm.com/docs/openshift?topic=openshift-openshift_versions#openshift_versions_available . labels = optional(map(string)) # A list of labels that you want to add to all the worker nodes in the worker pool. }) ) ) }) )
| n/a | yes |
| [cos](#input\_cos) | Object describing the cloud object storage instance, buckets, and keys. Set `use_data` to false to create instance |
list( object({ name = string use_data = optional(bool) resource_group = string plan = optional(string) random_suffix = optional(bool) # Use a random suffix for COS instance access_tags = optional(list(string), []) skip_kms_s2s_auth_policy = optional(bool, false) # skip auth policy between this instance and kms instance, useful if existing resources are used skip_flowlogs_s2s_auth_policy = optional(bool, false) # skip auth policy between flow logs service and this instance, set to true if this policy is already in place on account skip_atracker_s2s_auth_policy = optional(bool, false) # skip auth policyt between atracker service and this instance, set to true if this is existing recipient of atracker already buckets = list(object({ name = string storage_class = string endpoint_type = string force_delete = bool single_site_location = optional(string) region_location = optional(string) cross_region_location = optional(string) kms_key = optional(string) access_tags = optional(list(string), []) allowed_ip = optional(list(string), []) hard_quota = optional(number) archive_rule = optional(object({ days = number archive_filter_prefix = optional(string) enable = bool rule_id = optional(string) type = string })) expire_rule = optional(object({ days = optional(number) expire_filter_prefix = optional(string) date = optional(string) enable = bool expired_object_delete_marker = optional(string) prefix = optional(string) rule_id = optional(string) })) activity_tracking = optional(object({ activity_tracker_crn = string read_data_events = bool write_data_events = bool management_events = bool })) metrics_monitoring = optional(object({ metrics_monitoring_crn = string request_metrics_enabled = optional(bool) usage_metrics_enabled = optional(bool) })) })) keys = optional( list(object({ name = string role = string enable_HMAC = bool })) )
}) )
| n/a | yes |
| [enable\_transit\_gateway](#input\_enable\_transit\_gateway) | Create transit gateway | `bool` | `true` | no |
-| [existing\_vpc\_cbr\_zone\_id](#input\_existing\_vpc\_cbr\_zone\_id) | ID of the existing CBR (Context-based restrictions) network zone, with context set to the VPC. This zone is used in a CBR rule, which allows traffic to flow only from the landing zone VPCs to specific cloud services. | `string` | `null` | no |
+| [existing\_vpc\_cbr\_zone\_id](#input\_existing\_vpc\_cbr\_zone\_id) | ID of the existing CBR (Context-based restrictions) network zone, with context set to the VPC. This zone is used in a CBR rule, which allows traffic to flow only from the landing zone VPCs to specific cloud services. [Learn more](https://github.com/terraform-ibm-modules/terraform-ibm-landing-zone/blob/main/patterns/DA-cbr-tutorial.md). | `string` | `null` | no |
| [f5\_template\_data](#input\_f5\_template\_data) | Data for all f5 templates |
object({ name = optional(string) resource_group = optional(string) use_data = optional(bool) use_hs_crypto = optional(bool) access_tags = optional(list(string), []) service_endpoints = optional(string, "public-and-private") keys = optional( list( object({ name = string root_key = optional(bool) payload = optional(string) key_ring = optional(string) # Any key_ring added will be created force_delete = optional(bool) existing_key_crn = optional(string) # CRN of an existing key in the same or different account. endpoint = optional(string) # can be public or private iv_value = optional(string) # (Optional, Forces new resource, String) Used with import tokens. The initialization vector (IV) that is generated when you encrypt a nonce. The IV value is required to decrypt the encrypted nonce value that you provide when you make a key import request to the service. To generate an IV, encrypt the nonce by running ibmcloud kp import-token encrypt-nonce. Only for imported root key. encrypted_nonce = optional(string) # The encrypted nonce value that verifies your request to import a key to Key Protect. This value must be encrypted by using the key that you want to import to the service. To retrieve a nonce, use the ibmcloud kp import-token get command. Then, encrypt the value by running ibmcloud kp import-token encrypt-nonce. Only for imported root key. policies = optional( object({ rotation = optional( object({ interval_month = number }) ) dual_auth_delete = optional( object({ enabled = bool }) ) }) ) }) ) ) })
| n/a | yes |
diff --git a/patterns/DA-cbr-tutorial.md b/patterns/DA-cbr-tutorial.md
new file mode 100644
index 000000000..532de2c20
--- /dev/null
+++ b/patterns/DA-cbr-tutorial.md
@@ -0,0 +1,61 @@
+
+# Configuring Landing Zone with Cloud automation for account configuration to create CBR VPC Zone
+
+This tutorial provides step-by-step instructions for using the [Cloud automation for account configuration](https://cloud.ibm.com/catalog/7a4d68b4-cf8b-40cd-a3d1-f49aff526eb3/architecture/deploy-arch-ibm-account-infra-base-63641cec-6093-4b4f-b7b0-98d2f4185cd6-global?kind=terraform&format=terraform&version=93c7f855-881d-459b-8999-4567a4883f57-global) to provision a [Context-Based Restriction (CBR)](https://cloud.ibm.com/docs/account?topic=account-context-restrictions-whatis) VPC network [zone](https://cloud.ibm.com/docs/account?topic=account-context-restrictions-whatis#network-zones-whatis) and to configure `existing_vpc_cbr_zone_id` to add VPCs created by [Red Hat OpenShift Container Platform on VPC landing zone](https://cloud.ibm.com/catalog/architecture/deploy-arch-ibm-slz-ocp-95fccffc-ae3b-42df-b6d9-80be5914d852-global), a [VPC landing zone](https://cloud.ibm.com/catalog/architecture/deploy-arch-ibm-slz-vpc-9fc0fa64-27af-4fed-9dce-47b3640ba739-global), or a [VSI on VPC landing zone](https://cloud.ibm.com/catalog/architecture/deploy-arch-ibm-slz-vsi-ef663980-4c71-4fac-af4f-4a510a9bcf68-global) to the [CBR VPC network zone](https://cloud.ibm.com/docs/account?topic=account-context-restrictions-whatis#vpc-attribute). The Cloud automation for account configuration creates a predefined network zones (a zone for each [service](https://github.com/terraform-ibm-modules/terraform-ibm-cbr/blob/main/modules/fscloud/README.md#input_zone_service_ref_list)) and a [VPC zone](https://github.com/terraform-ibm-modules/terraform-ibm-cbr/blob/main/modules/fscloud/README.md#input_zone_vpc_crn_list), and the objective of this tutorial is to add the VPCs created and managed by landing zone automation to the predefined [CBR VPC zone]((https://github.com/terraform-ibm-modules/terraform-ibm-cbr/blob/main/modules/fscloud/README.md#input_zone_vpc_crn_list)).
+
+
+## Prerequisites
+- The Editor role on the [Projects]((https://cloud.ibm.com/docs/secure-enterprise?topic=secure-enterprise-understanding-projects)) service
+- The Editor and Manager role on the [Schematics](https://cloud.ibm.com/docs/schematics) service
+- The Viewer role on the resource group for the project
+
+For more information, see [Assigning users access to projects](https://cloud.ibm.com/docs/secure-enterprise?topic=secure-enterprise-access-project).
+
+## Step 1: Deploy the Cloud automation for account configuration
+
+1. Navigate to the IBM Cloud Catalog using this URL:
+ [Cloud automation for account configuration](https://cloud.ibm.com/catalog/7a4d68b4-cf8b-40cd-a3d1-f49aff526eb3/architecture/deploy-arch-ibm-account-infra-base-63641cec-6093-4b4f-b7b0-98d2f4185cd6-global?kind=terraform&format=terraform&version=93c7f855-881d-459b-8999-4567a4883f57-global)
+
+2. Click on **Add to [project](https://cloud.ibm.com/docs/secure-enterprise?topic=secure-enterprise-understanding-projects)** to start the deployment process
+
+3. Configure the deployment parameters:
+ - Enter the name for the project
+ - Enter the description (optional)
+ - Enter the configuration name
+ - Select the region
+ - Select the resource group
+
+4. Review your configuration and click **Create**
+
+5. Configure the required variables present under **security**, **required** and **optional** sections.
+
+6. Click on deploy.
+
+## Step 2: Retrieve the CBR VPC Zone ID
+
+To access the CBR VPC Zone ID, which becomes available as an output after the Account Base DA deployment completes -
+
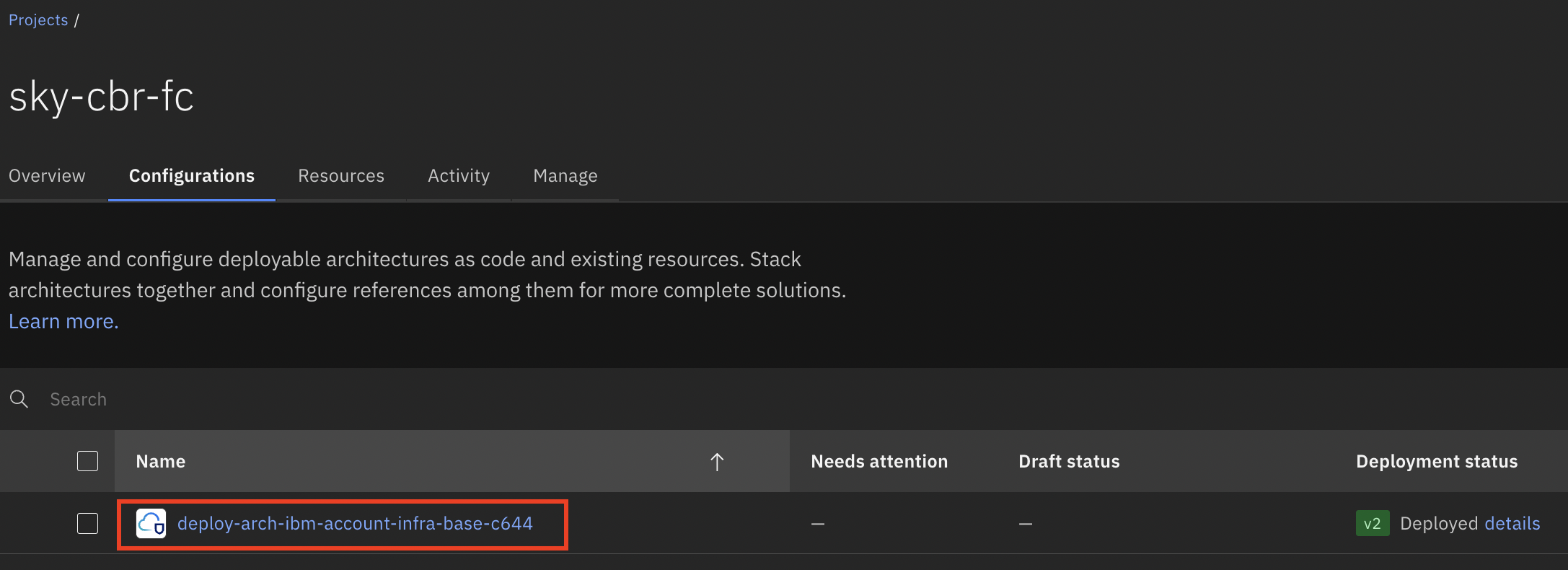
+1. Navigate to Account Infrastructure Base deployment and select the configuration as shown in the reference image below.
+
+
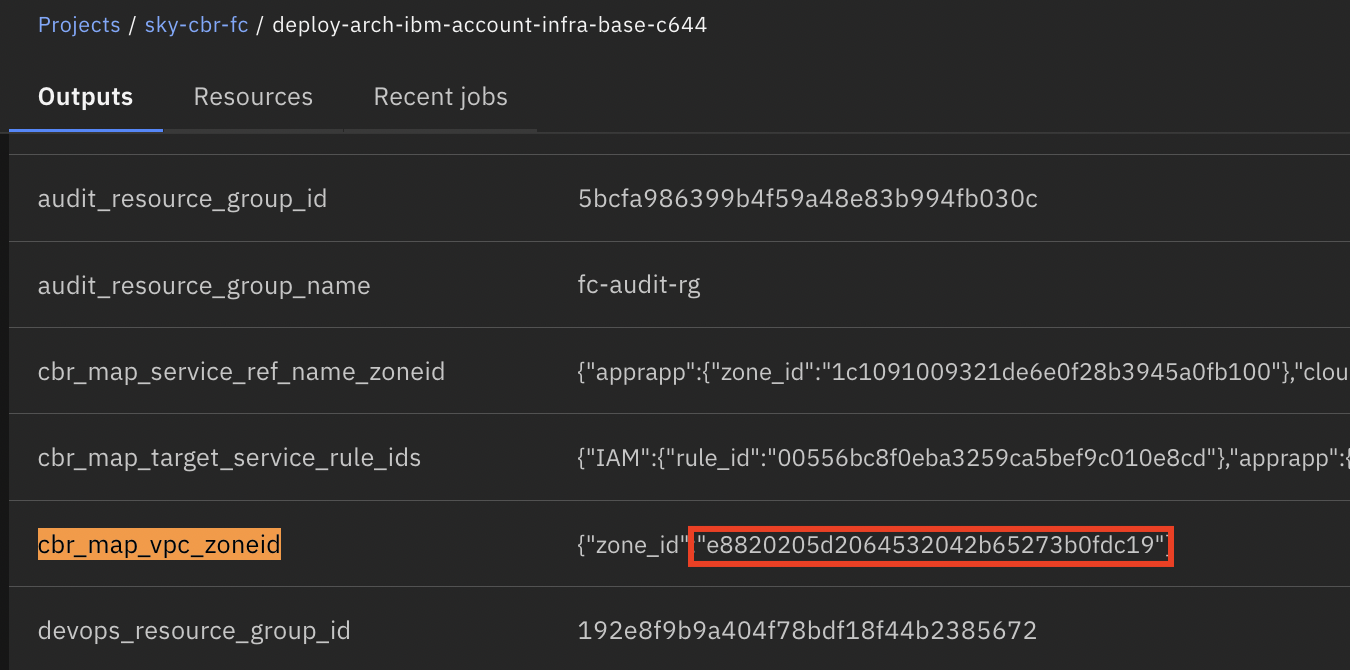
+2.In the outputs section, locate the output variable named `cbr_map_vpc_zoneid` and copy the `zone_id` value as illustrated below.
+
+
+## Step 3: Configure Landing Zone with the CBR Zone ID
+
+To properly configure landing zone with the retrieved CBR Zone ID -
+
+1. Select the appropriate landing zone automation from one of the following options:
+ - [Red Hat OpenShift Container Platform on VPC landing zone](https://cloud.ibm.com/catalog/architecture/deploy-arch-ibm-slz-ocp-95fccffc-ae3b-42df-b6d9-80be5914d852-global)
+ - [VPC landing zone](https://cloud.ibm.com/catalog/architecture/deploy-arch-ibm-slz-vpc-9fc0fa64-27af-4fed-9dce-47b3640ba739-global)
+ - [VSI on VPC landing zone](https://cloud.ibm.com/catalog/architecture/deploy-arch-ibm-slz-vsi-ef663980-4c71-4fac-af4f-4a510a9bcf68-global)
+
+2. Configure the required variables present under **security**, **required** and **optional** sections.
+
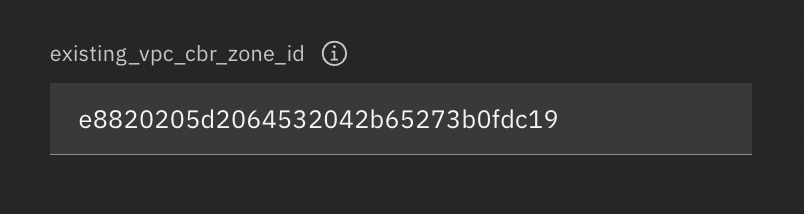
+3. Within the **optional** section, locate the field labeled `existing_vpc_cbr_zone_id` and paste the `zone_id` value copied in step 2, as shown below.
+
+
+4. Click on deploy.
+
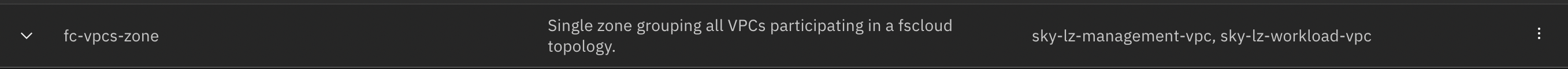
+5. Once deployed, CBR VPC zone will contain the required VPCs IDs as shown below.
+
diff --git a/patterns/roks/variables.tf b/patterns/roks/variables.tf
index ac5a55878..90525e51b 100644
--- a/patterns/roks/variables.tf
+++ b/patterns/roks/variables.tf
@@ -696,7 +696,7 @@ variable "IC_SCHEMATICS_WORKSPACE_ID" {
##############################################################################
variable "existing_vpc_cbr_zone_id" {
type = string
- description = "ID of the existing CBR (Context-based restrictions) network zone, with context set to the VPC. This zone is used in a CBR rule, which allows traffic to flow only from the landing zone VPCs to specific cloud services."
+ description = "ID of the existing CBR (Context-based restrictions) network zone, with context set to the VPC. This zone is used in a CBR rule, which allows traffic to flow only from the landing zone VPCs to specific cloud services. [Learn more](https://github.com/terraform-ibm-modules/terraform-ibm-landing-zone/blob/main/patterns/DA-cbr-tutorial.md)."
default = null
}
diff --git a/patterns/vpc/variables.tf b/patterns/vpc/variables.tf
index 127a34100..5b6a7c4a2 100644
--- a/patterns/vpc/variables.tf
+++ b/patterns/vpc/variables.tf
@@ -487,7 +487,7 @@ variable "IC_SCHEMATICS_WORKSPACE_ID" {
##############################################################################
variable "existing_vpc_cbr_zone_id" {
type = string
- description = "ID of the existing CBR (Context-based restrictions) network zone, with context set to the VPC. This zone is used in a CBR rule, which allows traffic to flow only from the landing zone VPCs to specific cloud services."
+ description = "ID of the existing CBR (Context-based restrictions) network zone, with context set to the VPC. This zone is used in a CBR rule, which allows traffic to flow only from the landing zone VPCs to specific cloud services. [Learn more](https://github.com/terraform-ibm-modules/terraform-ibm-landing-zone/blob/main/patterns/DA-cbr-tutorial.md)."
default = null
}
diff --git a/patterns/vsi/variables.tf b/patterns/vsi/variables.tf
index 504773c47..c9d18a408 100644
--- a/patterns/vsi/variables.tf
+++ b/patterns/vsi/variables.tf
@@ -535,7 +535,7 @@ variable "IC_SCHEMATICS_WORKSPACE_ID" {
variable "existing_vpc_cbr_zone_id" {
type = string
- description = "ID of the existing CBR (Context-based restrictions) network zone, with context set to the VPC. This zone is used in a CBR rule, which allows traffic to flow only from the landing zone VPCs to specific cloud services."
+ description = "ID of the existing CBR (Context-based restrictions) network zone, with context set to the VPC. This zone is used in a CBR rule, which allows traffic to flow only from the landing zone VPCs to specific cloud services. [Learn more](https://github.com/terraform-ibm-modules/terraform-ibm-landing-zone/blob/main/patterns/DA-cbr-tutorial.md)."
default = null
}
diff --git a/reference-architectures/cbr-vpc-zone.png b/reference-architectures/cbr-vpc-zone.png
new file mode 100644
index 000000000..c69ec54bd
Binary files /dev/null and b/reference-architectures/cbr-vpc-zone.png differ
diff --git a/reference-architectures/existing_vpc_cbr_zone_id.png b/reference-architectures/existing_vpc_cbr_zone_id.png
new file mode 100644
index 000000000..81193a970
Binary files /dev/null and b/reference-architectures/existing_vpc_cbr_zone_id.png differ
diff --git a/reference-architectures/infra-base-cbr-vpc-zone-id.png b/reference-architectures/infra-base-cbr-vpc-zone-id.png
new file mode 100644
index 000000000..71df245cc
Binary files /dev/null and b/reference-architectures/infra-base-cbr-vpc-zone-id.png differ
diff --git a/reference-architectures/infra-base-deployed.png b/reference-architectures/infra-base-deployed.png
new file mode 100644
index 000000000..3270e7da2
Binary files /dev/null and b/reference-architectures/infra-base-deployed.png differ
diff --git a/reference-architectures/roks.drawio.svg b/reference-architectures/roks.drawio.svg
index 4801350e3..c921f10af 100644
--- a/reference-architectures/roks.drawio.svg
+++ b/reference-architectures/roks.drawio.svg
@@ -1,4 +1,4 @@
-
\ No newline at end of file
+
\ No newline at end of file
diff --git a/reference-architectures/vpc.drawio.svg b/reference-architectures/vpc.drawio.svg
index 4b2eb8737..95f76b8ca 100644
--- a/reference-architectures/vpc.drawio.svg
+++ b/reference-architectures/vpc.drawio.svg
@@ -1,4 +1,4 @@
-
\ No newline at end of file
+
\ No newline at end of file
diff --git a/reference-architectures/vsi-vsi.drawio.svg b/reference-architectures/vsi-vsi.drawio.svg
index 43cfc7057..0200fe971 100644
--- a/reference-architectures/vsi-vsi.drawio.svg
+++ b/reference-architectures/vsi-vsi.drawio.svg
@@ -1,4 +1,4 @@
-
\ No newline at end of file
+
\ No newline at end of file
diff --git a/variables.tf b/variables.tf
index 214022477..3199a94a1 100644
--- a/variables.tf
+++ b/variables.tf
@@ -1374,7 +1374,7 @@ variable "skip_all_s2s_auth_policies" {
##############################################################################
variable "existing_vpc_cbr_zone_id" {
type = string
- description = "ID of the existing CBR (Context-based restrictions) network zone, with context set to the VPC. This zone is used in a CBR rule, which allows traffic to flow only from the landing zone VPCs to specific cloud services."
+ description = "ID of the existing CBR (Context-based restrictions) network zone, with context set to the VPC. This zone is used in a CBR rule, which allows traffic to flow only from the landing zone VPCs to specific cloud services. [Learn more](https://github.com/terraform-ibm-modules/terraform-ibm-landing-zone/blob/main/patterns/DA-cbr-tutorial.md)."
default = null
}