CrushFTP11 before 11.3.7_57 is vulnerable to stored HTML injection in the CrushFTP Admin Panel (Reports / "Who Created Folder"), enabling persistent HTML execution in admin sessions.
CWE-79 — Improper Neutralization of Input During Web Page Generation (Cross-site Scripting)
AV:N/AC:L/PR:L/UI:R/S:C/C:N/I:L/A:NAs noted in the vendor changelog ( https://crushftp.com/version11_build.html ) Versions 11.3.7_57 and later are not affected.
_57:login URL fix and session kicking fix, and a minor HTMLi for reports: CVE-2025-63420
A stored HTMLi vulnerability in the CrushFTP Admin Panel (Reports / 'Who Created Folder') allows authenticated attackers with permissions to create folders to inject malicious HTML codes.
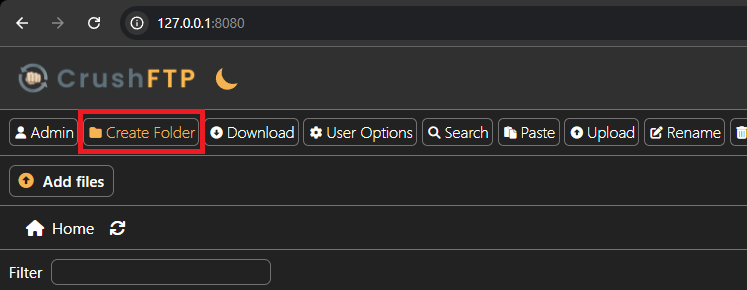
- Navigate to http://127.0.0.1:8080/
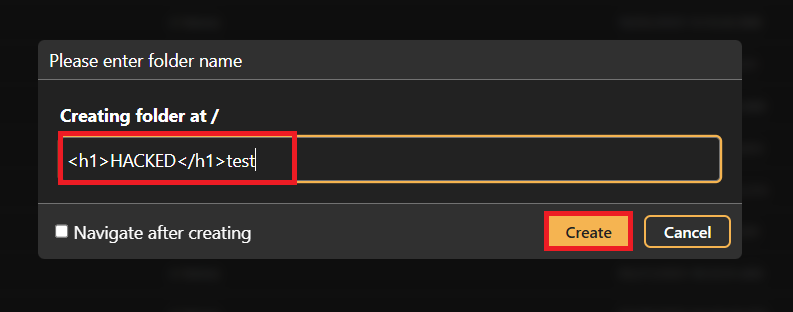
- Create a new Folder with the following payload:
<h1>HACKED</h1>test- Navigate to http://127.0.0.1:8080/WebInterface/admin/index.html, Click on "Reports" and select "Who Created Folder":
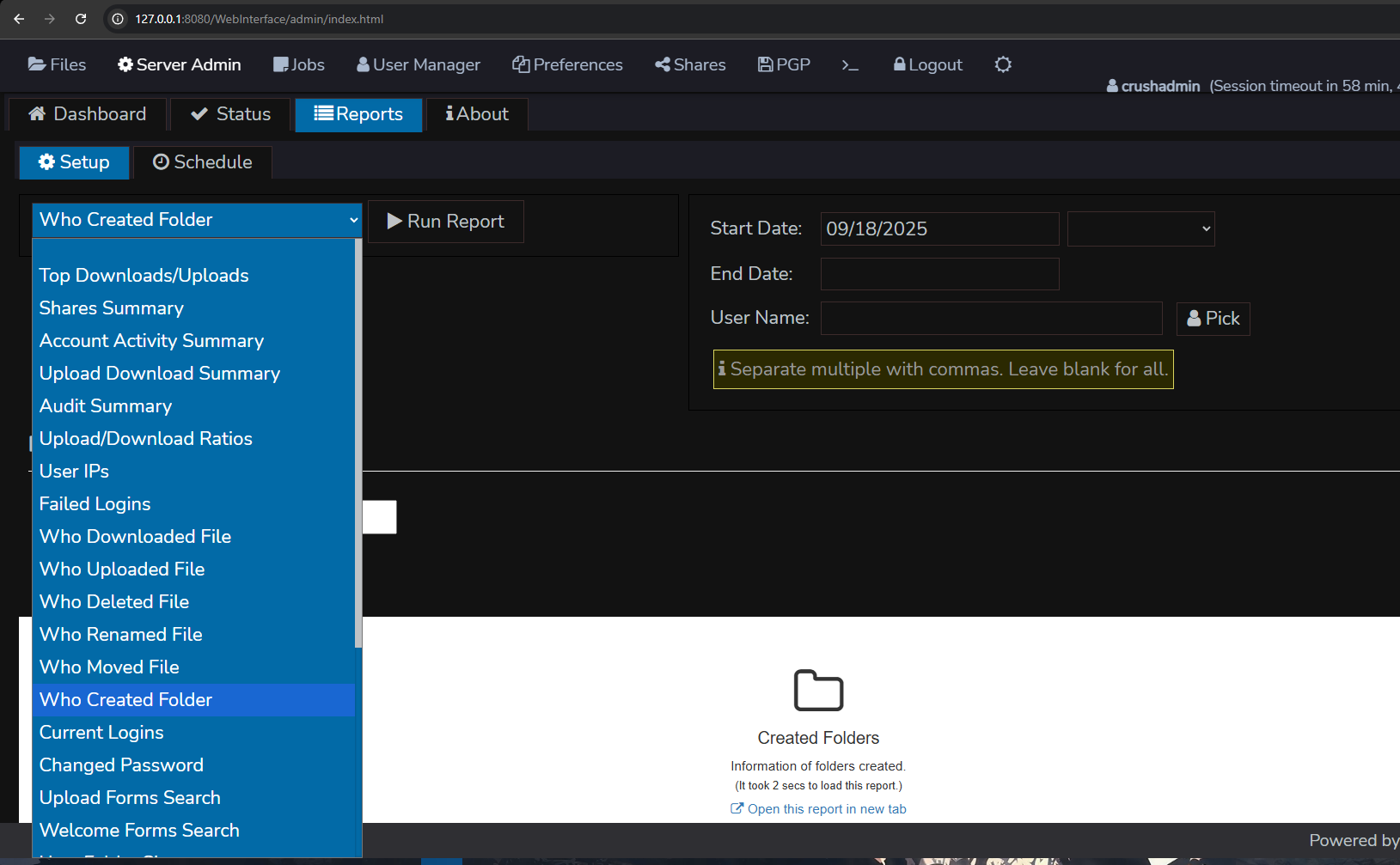
- Click on "Run Report"
- Wait for the report to load, after the report is loaded, scroll down and observe the HTMLi:
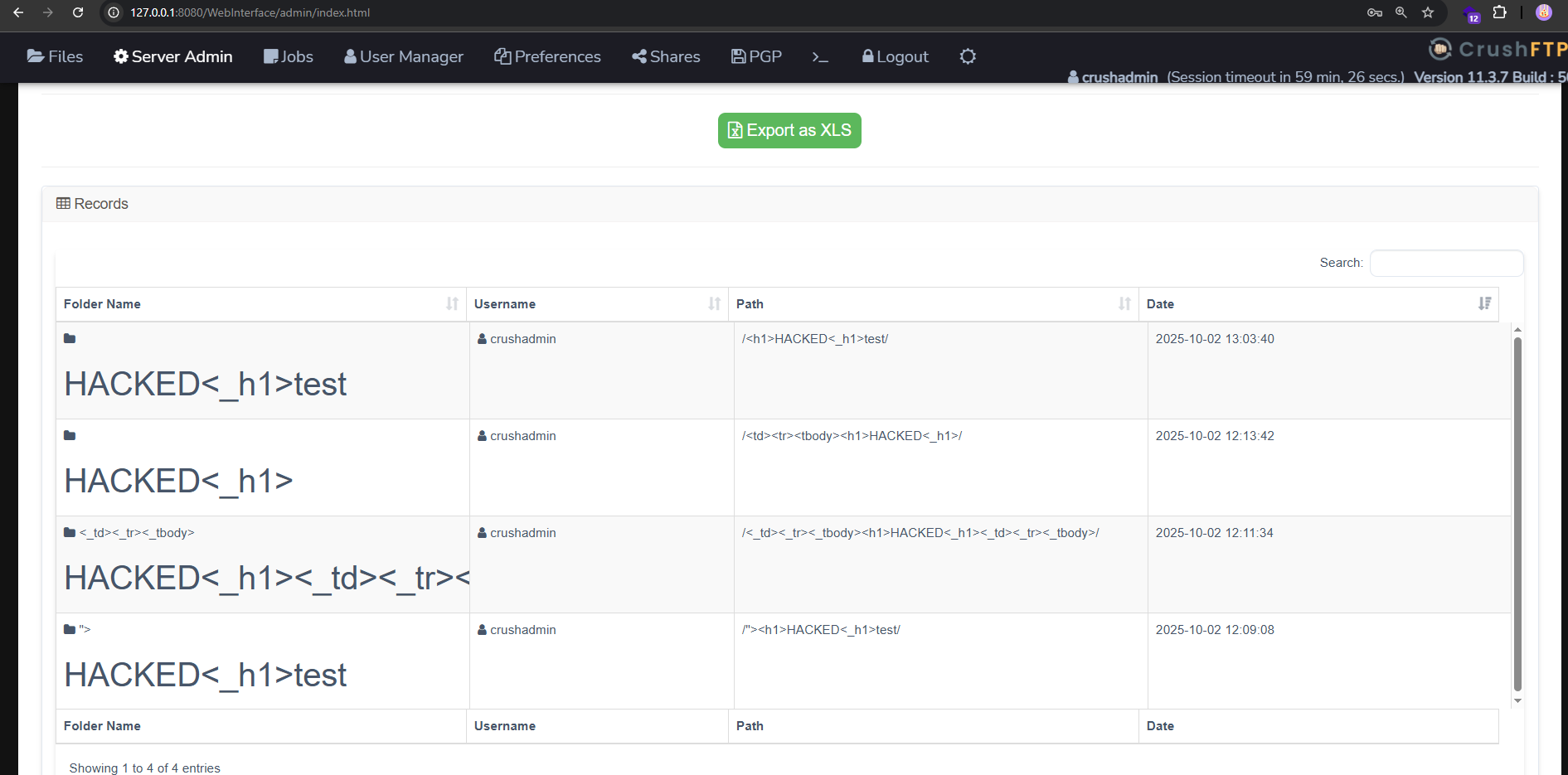
- For some UI Reasons, you might wanna create 2 folders within the same payload for the HTMLi to show.
Muntadhar M. Ahmed (almuntadhar0x01)