Add this suggestion to a batch that can be applied as a single commit.
This suggestion is invalid because no changes were made to the code.
Suggestions cannot be applied while the pull request is closed.
Suggestions cannot be applied while viewing a subset of changes.
Only one suggestion per line can be applied in a batch.
Add this suggestion to a batch that can be applied as a single commit.
Applying suggestions on deleted lines is not supported.
You must change the existing code in this line in order to create a valid suggestion.
Outdated suggestions cannot be applied.
This suggestion has been applied or marked resolved.
Suggestions cannot be applied from pending reviews.
Suggestions cannot be applied on multi-line comments.
Suggestions cannot be applied while the pull request is queued to merge.
Suggestion cannot be applied right now. Please check back later.
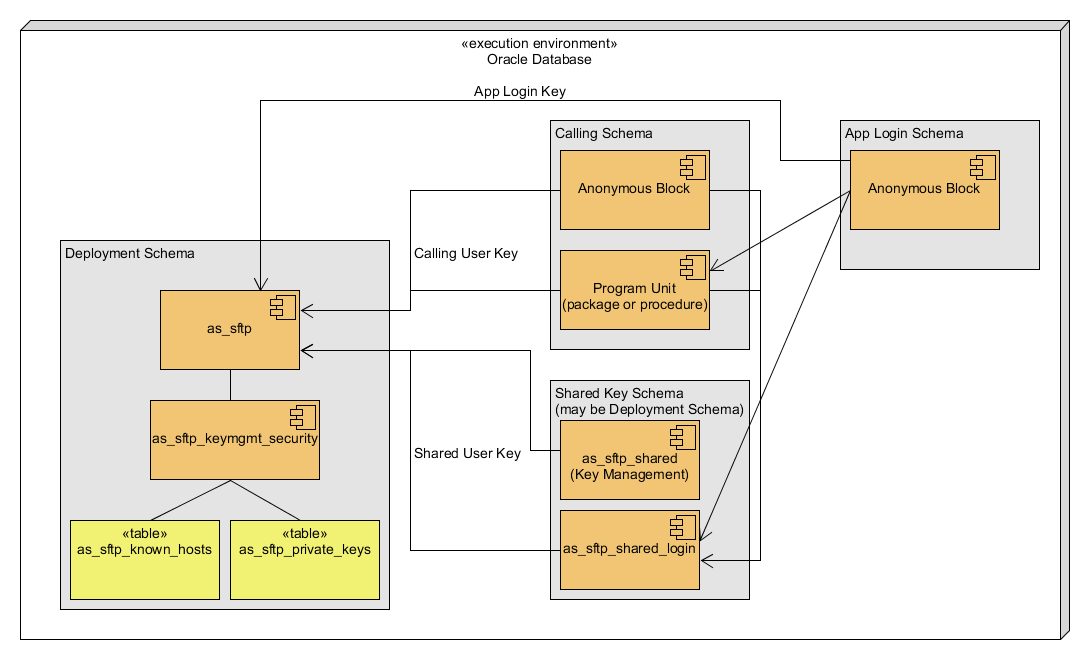
Resolves #16
I have not tested extensively with other user accounts (only 1 from anonymous sql). An implementer can allow each login user to manage their own keys/known hosts, or else can create a 2nd package for them to use that will centralize everything under the username of that package owner (can be same as owner of as_sftp).
The fine grained access control is optional. The key management works without it, but anyone who can select from the table will be able to obtain the private keys.
I did not add anything to the README.md or usage.md. My style is very different from yours and I don't want to presume.
I would be happy to create a document similar to others you can see it my github repository, but I'm not sure you want to maintain something like that.
I won't object if you reject the pull request but use my work to do it your way. I had fun and that was enough.
HTH.