Arango CVE Processor is built into Vulmatch which also handles the download of CVE objects (what you need for ACVEP to work). As such, Vulmatch is probably better suited to what you're looking for.
A small script that enriches CVEs to other sources with all data stored as STIX 2.1 objects.
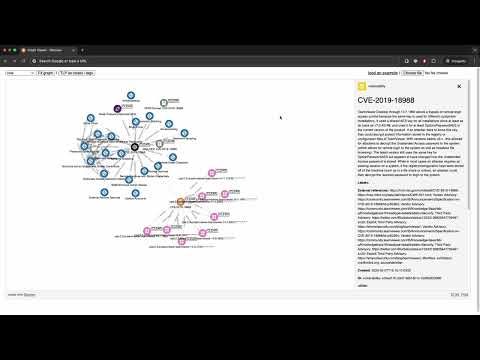
Here at DOGESEC we work with a lot of CVE data across our products. cve2stix generates core STIX 2.1 Vulnerability objects from CVE data.
However, we have lots of other sources (EPSS, KEV, ATT&CK...) that we want to enrich this data with.
We built Arango CVE Processor to handle the generation and maintenance of these enrichments.
In short, Arango CVE Processor is a script that;
- reads the ingested CVE STIX data in ArangoDB
- creates STIX objects to represent the relationships between CVE and other datasets
# clone the latest code
git clone https://github.com/muchdogesec/arango_cve_processor
# create a venv
cd arango_cve_processor
python3 -m venv arango_cve_processor-venv
source arango_cve_processor-venv/bin/activate
# install requirements
pip3 install -r requirements.txtArango CVE Processor has various settings that are defined in an .env file.
To create a template for the file:
cp .env.example .envTo see more information about how to set the variables, and what they do, read the .env.markdown file.
python3 arango_cve_processor.py \
MODE \
--
MODE OPTIONSThe following modes are available;
cve-cwe- links vulnerability objects to CWE objects
cve-capec(relies oncve-cwerun first)- links vulnerability objects to CAPEC objects
cve-attack(relies oncve-capecrun first)- links vulnerability objects to ATT&CK objects
cve-epss- creates/updates report objects linked to CVE representing one of more EPSS score for the time range run
cve-kev(relies oncve-cwerun first)- creates/updates report objects linked to CVE representing CISA KEV data
cve-vulncheck-kev(relies oncve-cwerun first)- creates/updates report objects linked to CVE representing Vulncheck KEV data
cpematch- creates/updates grouping objects (and linked software objects) representing CPE Matches tied to CPEs.
All modes have varying options, however, the following are available in all modes
--database(required): the arangoDB database name where the objects you want to link are found. It must contain the collectionsnvd_cve_vertex_collectionandnvd_cve_edge_collection--ignore_embedded_relationships(optional, boolean). Default isfalse. iftruepassed, this will stop any embedded relationships from being generated. This is a stix2arango feature where STIX SROs will also be created for_refand_refsproperties inside each object (e.g. if_refproperty =identity--1234and SRO between the object with the_refproperty andidentity--1234will be created). See stix2arango docs for more detail if required, essentially this a wrapper for the same--ignore_embedded_relationshipssetting implemented by stix2arango--ignore_embedded_relationships_sro(optional): boolean, iftruepassed, will stop any embedded relationships from being generated from SRO objects (type=relationship). Default isfalse--ignore_embedded_relationships_smo(optional): boolean, iftruepassed, will stop any embedded relationships from being generated from SMO objects (type=marking-definition,extension-definition,language-content). Default isfalse
To see the options available for each mode you can run with the help flag (-h), e.g.,
python3 arango_cve_processor.py \
cve-epss -hpython3 arango_cve_processor.py \
cve-cwe -hProcess CVE -> CWE relationships for all CVEs modified after 2024-02-01
python3 arango_cve_processor.py \
cve-cwe \
--database vulmatch_database \
--modified_min 2024-02-01 \
--ignore_embedded_relationships true \
--ignore_embedded_relationships_sro true \
--ignore_embedded_relationships_smo trueGet all EPSS scores for CVEs for each day in 2024
python3 arango_cve_processor.py \
cve-epss \
--database vulmatch_database \
--start_date 2024-01-01 \
--end_date 2024-12-31 \
--ignore_embedded_relationships true \
--ignore_embedded_relationships_sro true \
--ignore_embedded_relationships_smo trueUpdate all CPE Matches modified after 2024-02-01
python3 arango_cve_processor.py \
cpematch \
--database vulmatch_database \
--updated_after 2024-02-01 \
--ignore_embedded_relationships true \
--ignore_embedded_relationships_sro true \
--ignore_embedded_relationships_smo trueIf you would like to know how the logic of this script works in detail, please consult the /docs directory.
- To generate STIX 2.1 extensions: stix2 Python Lib
- STIX 2.1 specifications for objects: STIX 2.1 docs
- ArangoDB docs