Releases: opf/openproject
OpenProject 17.1.1
Release date: 2026-02-18
We released OpenProject OpenProject 17.1.1.
The release contains several bug fixes and we recommend updating to the newest version.
Below you will find a complete list of all changes and bug fixes.
Security fixes
CVE-2026-26966 - Improper Access Control on OpenProject through /api/v3/queries via POST request allows unauthorized users to create project queries
A broken access control vulnerability exists in the /api/v3/queries endpoint that allows a normal authenticated user, without sufficient permissions, to create private project queries.
By reusing a valid request generated by an administrator and replacing the session cookie and CSRF token with those of a low-privileged user, the backend accepts the request and successfully creates the query.
This action should be restricted to authorized roles only. The issue demonstrates missing or improper authorization checks on query creation.
This vulnerability was reported by user slashx0x as part of the [YesWeHack.com OpenProject Bug Bounty program](https://yeswehack.com/programs/openproject), sponsored by the European Commission.
For more information, please see the GitHub advisory #GHSA-5m66-2gm7-6jcc
CVE-2026-26968 - Improper Access Control on OpenProject instance through /api/v3/capabilities
The /api/v3/capabilities endpoint allows unauthorized enumeration of private project names and detailed permissions by specifying the built-in admin user ID as the principal.
While the API correctly prevents querying the capabilities of other users, the built-in Admin account remains resolvable.
Since projects use incremental values, and the built-in admin has visibility on all projects, this facilitates mapping of the entire openproject instance.
This vulnerability was reported by users syndrome_impostor and noidont as part of the YesWeHack.com OpenProject Bug Bounty program, sponsored by the European Commission.
For more information, please see the GitHub advisory #GHSA-g62r-9rgf-h53q
CVE-2026-26969 - HTML Injection on OpenProject instance through project name
The application is vulnerable to HTML injection due to improper sanitization of user-supplied input for the project name.
An attacker can inject arbitrary HTML tags into the response, altering the structure of the page. and later while creating workpackages payload is executed.
This vulnerability was reported by user roro1702
as part of the [YesWeHack.com OpenProject Bug Bounty program](https://yeswehack.com/programs/openproject), sponsored by the European Commission.
For more information, please see the GitHub advisory #GHSA-r4v5-h2fp-fhxf
CVE-2026-26970 - HTML injection on wiki updated mailer
An HTML injection vulnerability occurs in the wiki updated mailer function of OpenProject The application does not properly escape HTML tags, an attacker with invitation rights or users themselves when registrations are open can create a user name containing the HTML tags. If they then gain the permission to add or edit wiki pages, their author tag is not properly escaped in emails.
This vulnerability was reported by user yokokho as part of the [YesWeHack.com OpenProject Bug Bounty program](https://yeswehack.com/programs/openproject), sponsored by the European Commission.
For more information, please see the GitHub advisory #GHSA-jrhg-mx22-57rm
CVE-2026-26971 - IDOR on Hourly Rates Controller allows deletion of Hourly Rates on other projects
A project-scoped hourly rates update endpoint in the Costs module allows deleting a target user’s hourly rates across all projects by sending a crafted request that omits the user parameter. The request is authorized only against the URL project (:project_id), but the deletion query is not scoped to that project, resulting in cross-project broken access control (horizontal privilege escalation).
This vulnerability was reported by user sam91281 as part of the YesWeHack.com OpenProject Bug Bounty program, sponsored by the European Commission.
For more information, please see the GitHub advisory #GHSA-xh2h-jfr6-3qhc
CVE-2026-26976 - HTML Injection via Email Field in User Registration Leading to Malicious Notification Email to Instance Owner (Admin)
When anonymous registration is enabled, an unauthenticated attacker can submit a malicious payload in the email field during registration attempt (/account/register). Even when the registration fails due to the free plan user limit (10 active users), the system sends a notification email to the instance owner/admin warning that the user limit is reached. This email reflects the malicious email payload unescaped in the body/subject/content, allowing HTML injection.
This enables phishing, content spoofing, or (in rare cases with permissive email clients) limited XSS-like behavior in the admin's inbox.
This vulnerability was reported by user pdowski as part of the YesWeHack.com OpenProject Bug Bounty program, sponsored by the European Commission.
For more information, please see the GitHub advisory #GHSA-6m5j-mp2j-cgmm
CVE-2026-27006 - Path Traversal on OpenProject BIM Edition leads to Arbitrary File upload on BCF module, resulting in possible RCE when using file-based caching
An authenticated attacker with BCF module access can write arbitrary files to any writable directory on the server through a path traversal vulnerability in the BCF import functionality. For docker-compose based installations, this can be expanded to a remote code execution using cache deserialization.
This vulnerability was reported by user shafouzzz as part of the YesWeHack.com OpenProject Bug Bounty program, sponsored by the European Commission.
For more information, please see the GitHub advisory #GHSA-4fvm-rrc8-mgch
CVE-2026-27019 - Path Traversal via Incoming Email Attachments Leads to Arbitrary File Write and RCE
When OpenProject is configured to accept and handle incoming emails, it was possible that an attacker could send an email with a specially crafted attachment that would be written to a predefined location in the filesystem. All files that can be written by the openproject system user could be written. This could even be evaluated to a Remote Code Execution vulnerability.
This vulnerability was reported by user sam91281 as part of the YesWeHack.com OpenProject Bug Bounty program, sponsored by the European Commission.
For more information, please see the GitHub advisory #GHSA-r85w-rv9m-q784
Bug fixes and changes
- Bugfix: Documents: zooming in issue on iOS [#71023]
- Bugfix: Seeding in zh-TW fails [#71869]
- Bugfix: Default document types are recreated after every OpenProject update [#71877]
- Bugfix: External links in notification emails not captured [#71907]
- Bugfix: External links with encoded space in path lead to OpenProject home page [#71931]
- Bugfix: Error in meeting PDF exports if cover image file storage is broken [#71945]
- Bugfix: Last admin can delete themselves [#71980]
Contributions
A big thanks to our Community members for reporting bugs and helping us identify and provide fixes.
This release, special thanks for reporting and finding bugs go to Andreas H..
OpenProject 17.0.4
Release date: 2026-02-18
We released OpenProject OpenProject 17.0.4.
The release contains several bug fixes and we recommend updating to the newest version.
Below you will find a complete list of all changes and bug fixes.
Security fixes
CVE-2026-26966 - Improper Access Control on OpenProject through /api/v3/queries via POST request allows unauthorized users to create project queries
A broken access control vulnerability exists in the /api/v3/queries endpoint that allows a normal authenticated user, without sufficient permissions, to create private project queries.
By reusing a valid request generated by an administrator and replacing the session cookie and CSRF token with those of a low-privileged user, the backend accepts the request and successfully creates the query.
This action should be restricted to authorized roles only. The issue demonstrates missing or improper authorization checks on query creation.
This vulnerability was reported by user slashx0x as part of the [YesWeHack.com OpenProject Bug Bounty program](https://yeswehack.com/programs/openproject), sponsored by the European Commission.
For more information, please see the GitHub advisory #GHSA-5m66-2gm7-6jcc
CVE-2026-26968 - Improper Access Control on OpenProject instance through /api/v3/capabilities
The /api/v3/capabilities endpoint allows unauthorized enumeration of private project names and detailed permissions by specifying the built-in admin user ID as the principal.
While the API correctly prevents querying the capabilities of other users, the built-in Admin account remains resolvable.
Since projects use incremental values, and the built-in admin has visibility on all projects, this facilitates mapping of the entire openproject instance.
This vulnerability was reported by users syndrome_impostor and noidont as part of the YesWeHack.com OpenProject Bug Bounty program, sponsored by the European Commission.
For more information, please see the GitHub advisory #GHSA-g62r-9rgf-h53q
CVE-2026-26969 - HTML Injection on OpenProject instance through project name
The application is vulnerable to HTML injection due to improper sanitization of user-supplied input for the project name.
An attacker can inject arbitrary HTML tags into the response, altering the structure of the page. and later while creating workpackages payload is executed.
This vulnerability was reported by user roro1702
as part of the [YesWeHack.com OpenProject Bug Bounty program](https://yeswehack.com/programs/openproject), sponsored by the European Commission.
For more information, please see the GitHub advisory #GHSA-r4v5-h2fp-fhxf
CVE-2026-26970 - HTML injection on wiki updated mailer
An HTML injection vulnerability occurs in the wiki updated mailer function of OpenProject The application does not properly escape HTML tags, an attacker with invitation rights or users themselves when registrations are open can create a user name containing the HTML tags. If they then gain the permission to add or edit wiki pages, their author tag is not properly escaped in emails.
This vulnerability was reported by user yokokho as part of the [YesWeHack.com OpenProject Bug Bounty program](https://yeswehack.com/programs/openproject), sponsored by the European Commission.
For more information, please see the GitHub advisory #GHSA-jrhg-mx22-57rm
CVE-2026-26971 - IDOR on Hourly Rates Controller allows deletion of Hourly Rates on other projects
A project-scoped hourly rates update endpoint in the Costs module allows deleting a target user’s hourly rates across all projects by sending a crafted request that omits the user parameter. The request is authorized only against the URL project (:project_id), but the deletion query is not scoped to that project, resulting in cross-project broken access control (horizontal privilege escalation).
This vulnerability was reported by user sam91281 as part of the YesWeHack.com OpenProject Bug Bounty program, sponsored by the European Commission.
For more information, please see the GitHub advisory #GHSA-xh2h-jfr6-3qhc
CVE-2026-26976 - HTML Injection via Email Field in User Registration Leading to Malicious Notification Email to Instance Owner (Admin)
When anonymous registration is enabled, an unauthenticated attacker can submit a malicious payload in the email field during registration attempt (/account/register). Even when the registration fails due to the free plan user limit (10 active users), the system sends a notification email to the instance owner/admin warning that the user limit is reached. This email reflects the malicious email payload unescaped in the body/subject/content, allowing HTML injection.
This enables phishing, content spoofing, or (in rare cases with permissive email clients) limited XSS-like behavior in the admin's inbox.
This vulnerability was reported by user pdowski as part of the YesWeHack.com OpenProject Bug Bounty program, sponsored by the European Commission.
For more information, please see the GitHub advisory #GHSA-6m5j-mp2j-cgmm
CVE-2026-27006 - Path Traversal on OpenProject BIM Edition leads to Arbitrary File upload on BCF module, resulting in possible RCE when using file-based caching
An authenticated attacker with BCF module access can write arbitrary files to any writable directory on the server through a path traversal vulnerability in the BCF import functionality. For docker-compose based installations, this can be expanded to a remote code execution using cache deserialization.
This vulnerability was reported by user shafouzzz as part of the YesWeHack.com OpenProject Bug Bounty program, sponsored by the European Commission.
For more information, please see the GitHub advisory #GHSA-4fvm-rrc8-mgch
CVE-2026-27019 - Path Traversal via Incoming Email Attachments Leads to Arbitrary File Write and RCE
When OpenProject is configured to accept and handle incoming emails, it was possible that an attacker could send an email with a specially crafted attachment that would be written to a predefined location in the filesystem. All files that can be written by the openproject system user could be written. This could even be evaluated to a Remote Code Execution vulnerability.
This vulnerability was reported by user sam91281 as part of the YesWeHack.com OpenProject Bug Bounty program, sponsored by the European Commission.
For more information, please see the GitHub advisory #GHSA-r85w-rv9m-q784
Bug fixes and changes
OpenProject 16.6.8
Release date: 2026-02-18
We released OpenProject OpenProject 16.6.8.
The release contains several bug fixes and we recommend updating to the newest version.
Below you will find a complete list of all changes and bug fixes.
Security fixes
CVE-2026-27006 - Path Traversal on OpenProject BIM Edition leads to Arbitrary File upload on BCF module, resulting in possible RCE when using file-based caching
An authenticated attacker with BCF module access can write arbitrary files to any writable directory on the server through a path traversal vulnerability in the BCF import functionality. For docker-compose based installations, this can be expanded to a remote code execution using cache deserialization.
This vulnerability was reported by user shafouzzz as part of the YesWeHack.com OpenProject Bug Bounty program, sponsored by the European Commission.
For more information, please see the GitHub advisory #GHSA-4fvm-rrc8-mgch
CVE-2026-27019 - Path Traversal via Incoming Email Attachments Leads to Arbitrary File Write and RCE
When OpenProject is configured to accept and handle incoming emails, it was possible that an attacker could send an email with a specially crafted attachment that would be written to a predefined location in the filesystem. All files that can be written by the openproject system user could be written. This could even be evaluated to a Remote Code Execution vulnerability.
This vulnerability was reported by user sam91281 as part of the YesWeHack.com OpenProject Bug Bounty program, sponsored by the European Commission.
For more information, please see the GitHub advisory #GHSA-r85w-rv9m-q784
Bug fixes and changes
OpenProject 17.1.0
Release date: 2026-02-11
We released OpenProject 17.1.0. The release contains several bug fixes and we recommend updating to the newest version. In these Release Notes, we will give an overview of important feature changes. At the end, you will find a complete list of all changes and bug fixes.
Important feature changes
Take a look at our release video showing the most important features introduced in OpenProject 17.1.0:
Release video of OpenProject 17.1
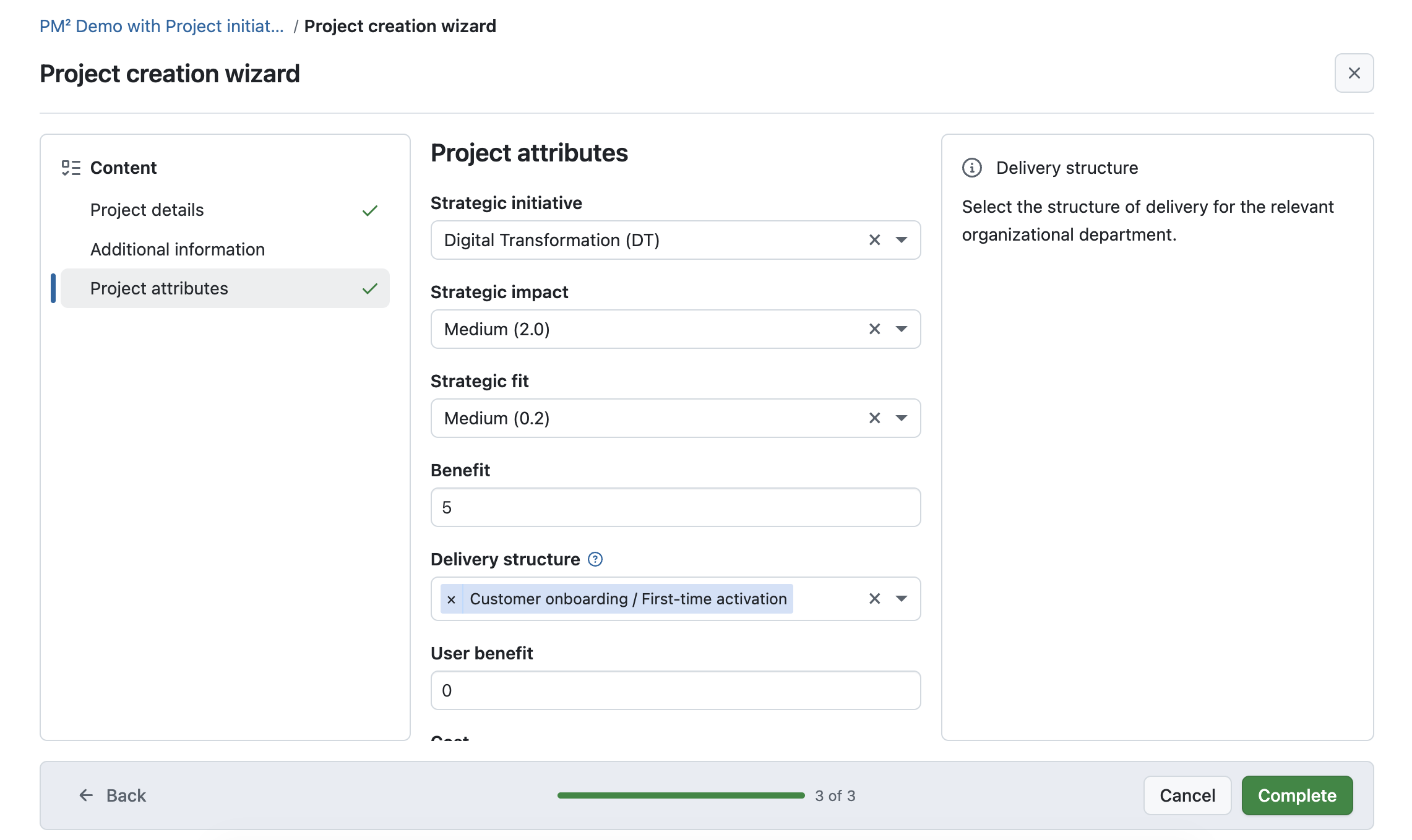
Automated project initiation request with a guided wizard (Enterprise add-on)
OpenProject introduces a configurable wizard for project initiation requests. The wizard can be enabled per template project.
See our documentation to learn how to use the automated project initiation request with OpenProject.
Configurable project initiation wizard
Administrators can configure a project initiation wizard to define how new project requests are submitted. This includes selecting which project attributes and sections are shown in the wizard, and which fields are required or optional.
The wizard guides users step by step through the initiation process using a fullscreen, three-column layout with section navigation, contextual help, and a progress indicator. Instead of completing required project attributes during project creation, users provide this information as part of the initiation request.
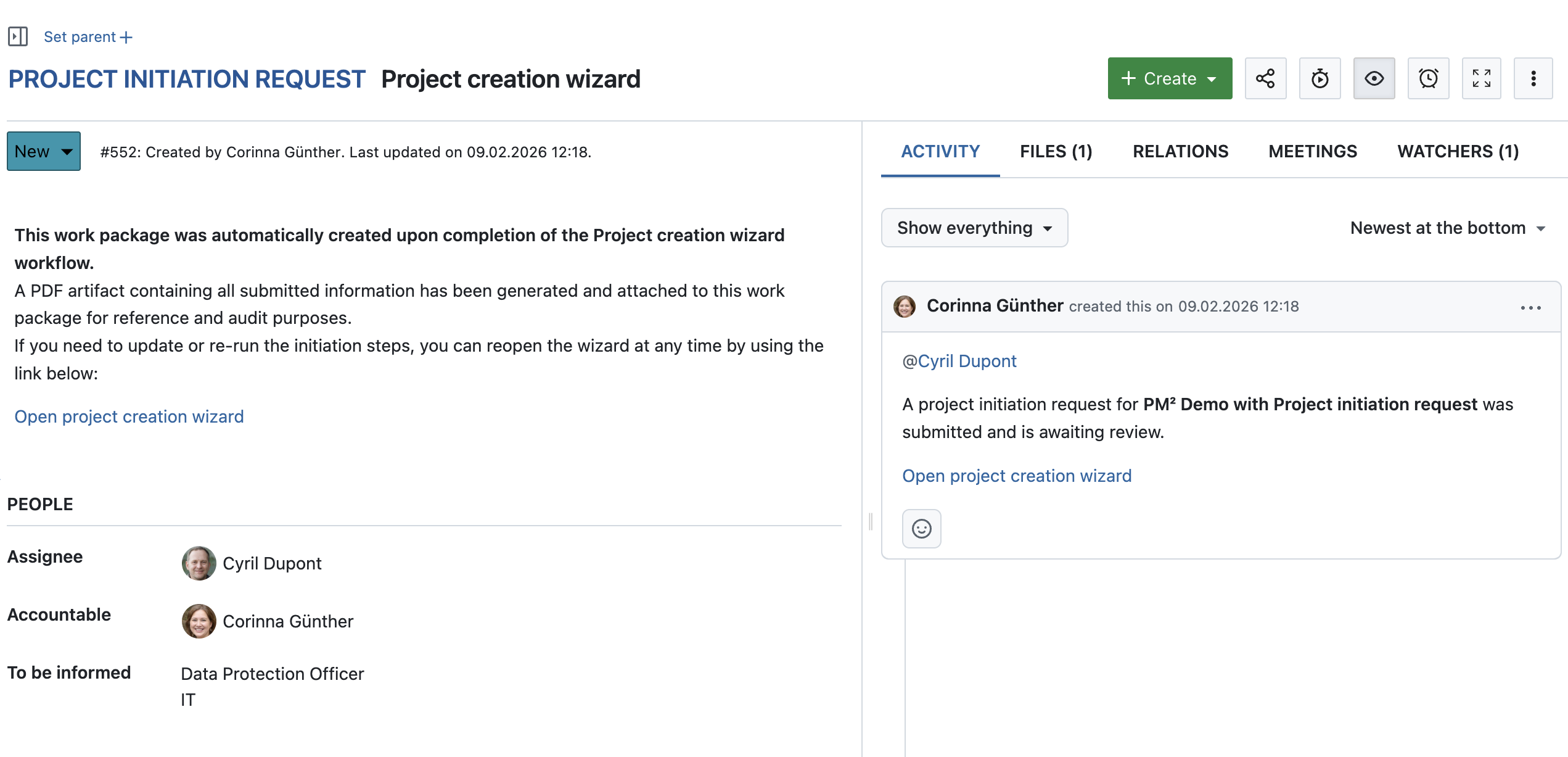
Work package created for a project initiation request
When a project initiation request is submitted for the first time, OpenProject automatically creates a work package that represents the request and serves as its central tracking artifact.
The work package is created once based on the wizard configuration at the time of the initial submission, including the work package type, status, and initial assignee. The assignee can be derived from a project attribute or a project role, such as a project owner.
Note
If the project initiation request is submitted again later, the changes (like different assignee) might not be automatically displayed in the work package and need to be manually updated. However, each submission generates a new PDF artifact, which is uploaded and linked to the existing work package. This allows changes to be reviewed and documented over time, while keeping the work package as the central place for processing the request using existing workflows.
Automatically generated project initiation artifact (PDF)
Upon submission of the project initiation request, a PDF artifact is automatically generated. The artifact contains all information entered in the wizard and is attached to the corresponding work package for documentation and audit purposes.
The artifact is updated automatically whenever the status of the project initiation request work package changes, ensuring that the documentation always reflects the current state.
Note
The project initiation request workflow is particularly well suited for structured frameworks such as PM² or PMflex, while remaining flexible enough to be used independently of any specific methodology. Read this blog article for more information.
Updates for the Meetings module
The Meetings module received several improvements that extend how meeting results are documented, reused, and shared.
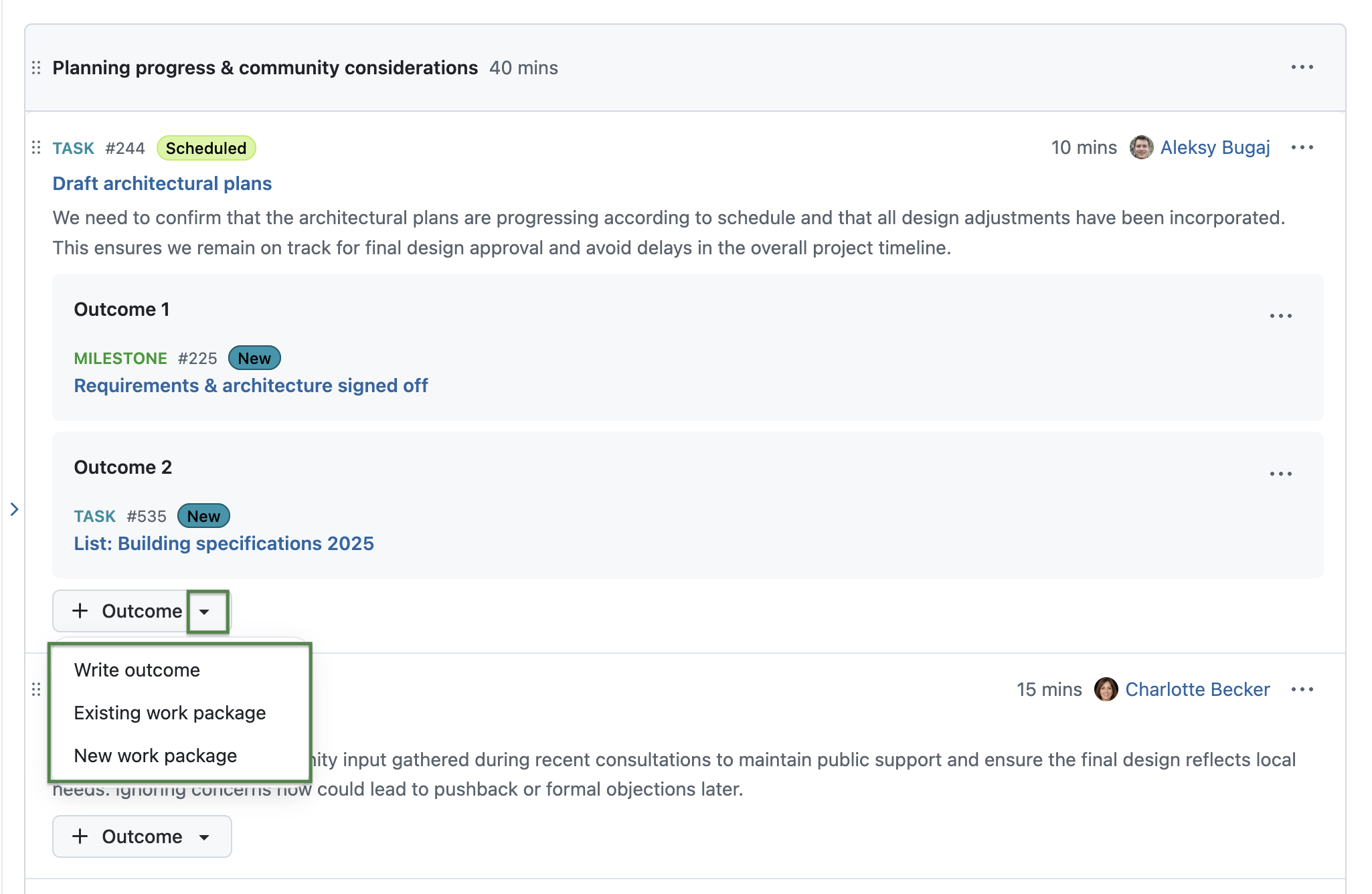
Add new or existing work packages as meeting outcomes
Users can now add work packages as meeting outcomes, allowing teams to turn meeting results into actionable follow-up items without leaving the meeting context. They can either:
- link an existing work package, or
- create a new work package as an outcome.
Each linked work package automatically shows a reference to the meeting in its Meetings tab, making the connection between the agenda item and the follow-up item explicit.
Since we already introduced multiple outcomes per agenda item in OpenProject 17.0, it is now also possible to link multiple work packages to the same agenda item.
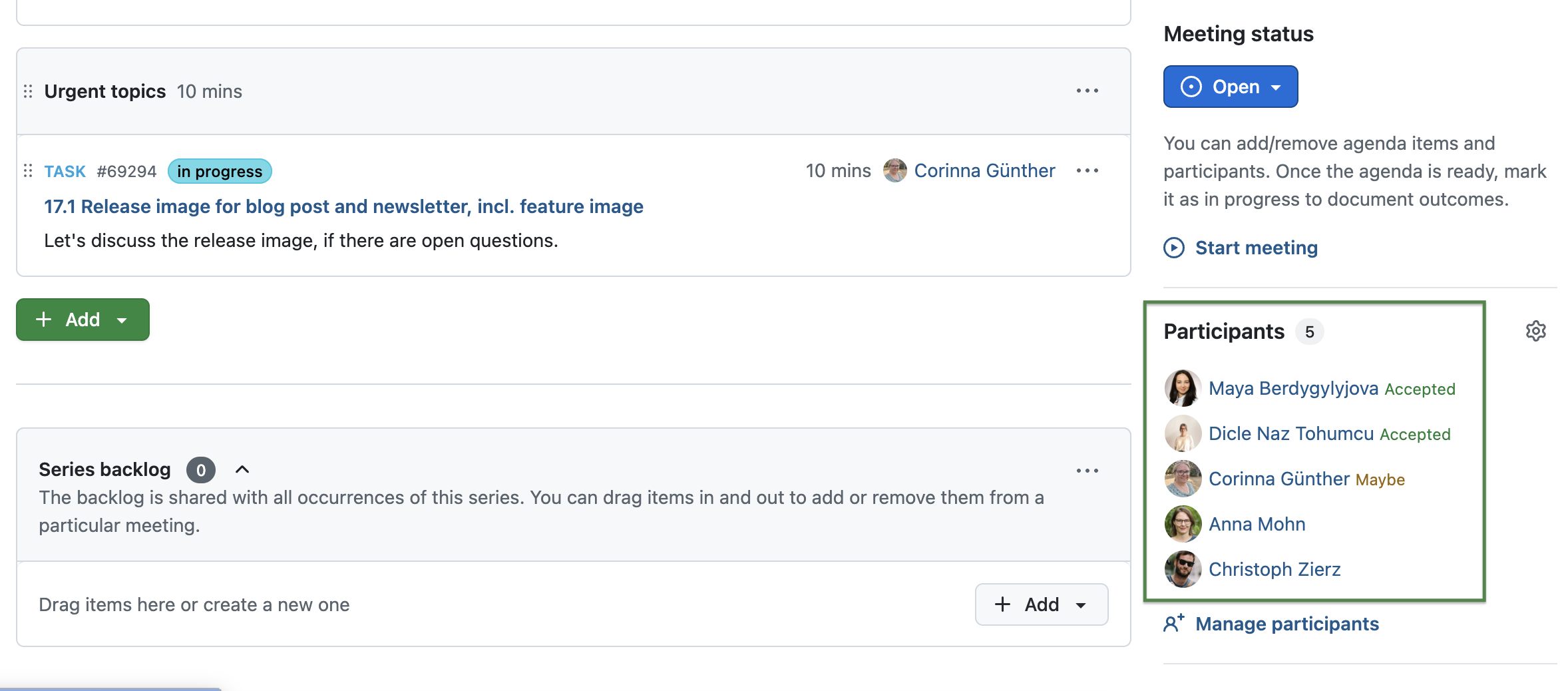
Show iCal responses in OpenProject
Meeting participant responses such as accepted, declined, or tentative are now visible directly in the meeting sidebar. These responses are collected from calendar invitations (for example when an ICS event is sent by email or downloaded and shared), making it easier to see the current participation status of all attendees in OpenProject.
Duplicate agenda items to the next recurring meeting occurrence
Users can now duplicate agenda items to the next occurrence of a recurring meeting. This makes it possible to carry over open topics or recurring discussion points without recreating them manually.
To duplicate an agenda item, users can select the corresponding option from the agenda item actions menu. The duplicated agenda item is added to the next meeting occurrence and can be edited independently.
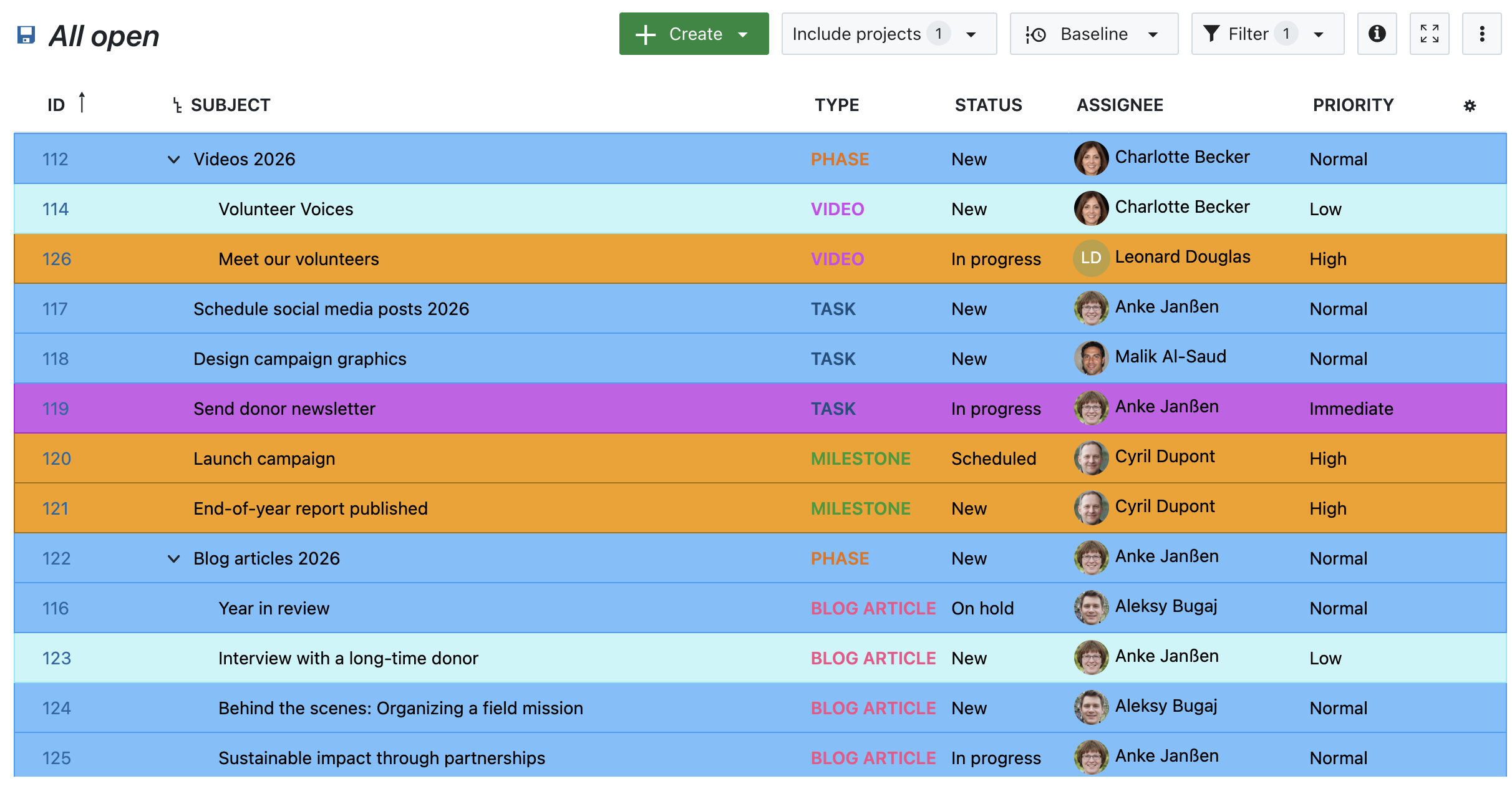
Release Attribute highlighting to Community
The Attribute highlighting feature, previously available only as an Enterprise add-on, is now included in the free Community plan.
Users can configure attribute highlighting in work package table views by opening the table configuration and selecting the Highlighting tab. Attributes such as Status, Priority, and Finish date can be highlighted inline or applied as full-row highlights based on attribute values. This makes key attributes visually distinguishable directly in the work package list without opening individual items.
Read more about attribute highlighting in our documentation.
Here's an example of highlighting work packages by priority:
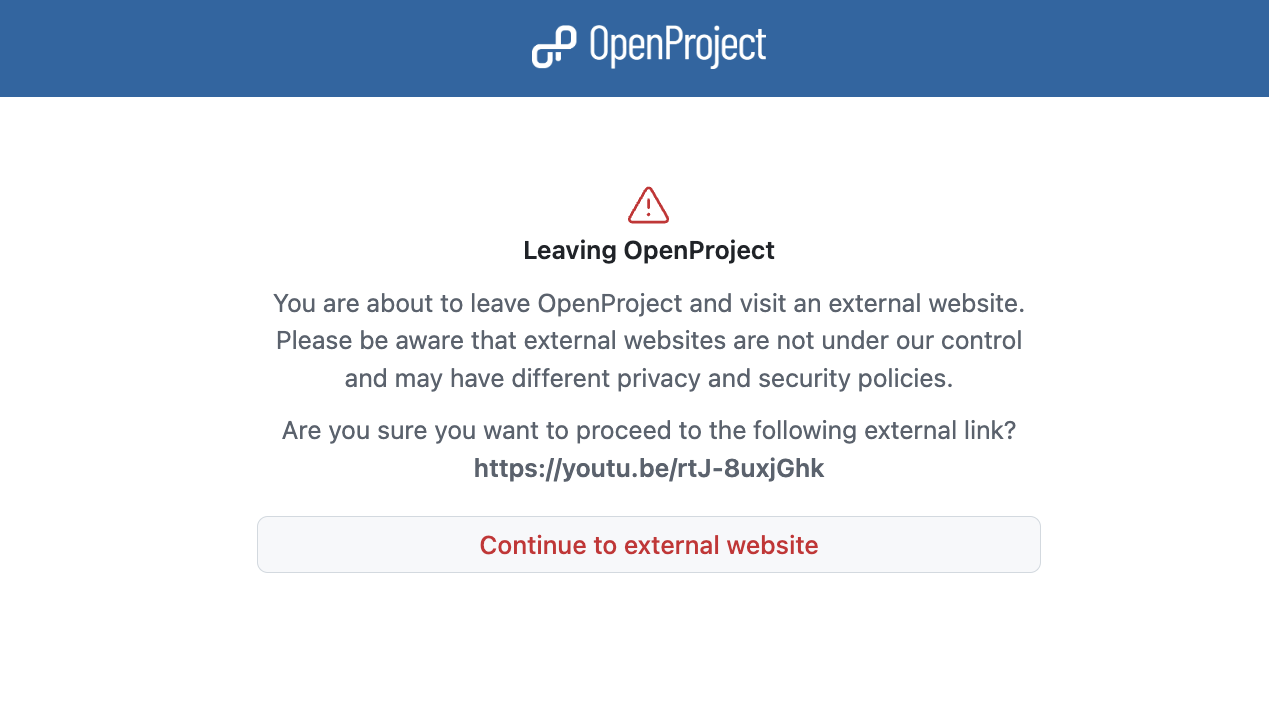
Capture external links (Enterprise add-on)
With 17.1 OpenProject introduces an option to add a warning when accessing external links from formatted text, such as project descriptions, comments or wiki pages. The warning adds an additional security layer by making users aware that they are about to leave OpenProject.
When users click on an external link, a confirmation dialog is displayed indicating that the link leads outside of OpenProject. This applies to links added by users, for example in descriptions, comments, or other text fields. In SaaS trial environments, external link handling is enforced to ensure that warnings for user-provided external links cannot be bypassed.
Read more about this warning on external links in our documentation.
Show short and weight values for Hierarchy and Weighted item list fields (Enterprise add-on)
Users now see an item’s short or weight wherever values from Hierarchy or Weighted item list custom fields (work packages) and project attributes are shown. This provides an extra hint to confirm that the right item was selected.
This information is displayed in:
- Work package details (for assigned values).
- Work package tables (for assigned values).
- Project attributes (for assigned values).
- The tree view selector while selecting a value (work packages and projects).
- The admin Items tab when editing the field, including the tree overview.
Read more about custom fields in OpenProject.
![OpenProject administration for custom fields, example of "Ben...
OpenProject 17.0.3
Release date: 2026-02-06
We released OpenProject OpenProject 17.0.3.
The release contains several bug fixes and we recommend updating to the newest version.
Below you will find a complete list of all changes and bug fixes.
Security fixes
GHSA-q523-c695-h3hp - Stored HTML injection on time tracking
An HTML injection vulnerability occurs in the time tracking function of OpenProject version 17.0.2. The application does not escape HTML tags, an attacker with administrator privileges can create a work package with the name containing the HTML tags and add it to the Work package section when creating time tracking.
Responsibly disclosed by Researcher: Nguyen Truong Son (truongson526@gmail.com) through the GitHub advisory.
For more information, please see the GitHub advisory #GHSA-q523-c695-h3hp
GHSA-x37c-hcg5-r5m7 - Command Injection on OpenProject repositories leads to Remote Code Execution
An arbitrary file write vulnerability exists in OpenProject’s repository changes endpoint (/projects/:project_id/repository/changes) when rendering the “latest changes” view via git log.
By supplying a specially crafted rev value (for example, rev=--output=/tmp/poc.txt), an attacker can inject git log command-line options. When OpenProject executes the SCM command, Git interprets the attacker-controlled rev as an option and writes the output to an attacker-chosen path.
As a result, any user with the :browse_repository permission on the project can create or overwrite arbitrary files that the OpenProject process user is permitted to write. The written contents consist of git log output, but by crafting custom commits the attacker can still upload valid shell scripts, ultimately leading to RCE. The RCE lets the attacker create a reverse shell to the target host and view confidential files outside of OpenProject, such as /etc/passwd.
This vulnerability was reported by user sam91281 as part of the YesWeHack.com OpenProject Bug Bounty program, sponsored by the European Commission.
For more information, please see the GitHub advisory #GHSA-x37c-hcg5-r5m7
Bug fixes and changes
- Bugfix: Unable to change to earlier finish date for automatically scheduled successor [#65130]
- Bugfix: DPA/AVV cannot be downloaded [#67323]
- Bugfix: hocupocus logs [onAuthenticate] fetch failed and connection to collaboration server not possible [#70542]
- Bugfix: Wrong sidebar sort order in System Admin Guide -> Authentication [#70914]
- Bugfix: "form_configuration-status=422" Unable to Change Custom fields in Work Packages without Enterprise Plan [#71093]
Contributions
A big thanks to our Community members for reporting bugs and helping us identify and provide fixes.
This release, special thanks for reporting and finding bugs go to Stefan Weiberg, Christoph Withers.
OpenProject 16.6.7
Release date: 2026-02-06
We released OpenProject OpenProject 16.6.7.
The release contains several bug fixes and we recommend updating to the newest version.
Below you will find a complete list of all changes and bug fixes.
Security fixes
GHSA-q523-c695-h3hp - Stored HTML injection on time tracking
An HTML injection vulnerability occurs in the time tracking function of OpenProject version 17.0.2. The application does not escape HTML tags, an attacker with administrator privileges can create a work package with the name containing the HTML tags and add it to the Work package section when creating time tracking.
Responsibly disclosed by Researcher: Nguyen Truong Son (truongson526@gmail.com) through the GitHub advisory.
For more information, please see the GitHub advisory #GHSA-q523-c695-h3hp
GHSA-x37c-hcg5-r5m7 - Command Injection on OpenProject repositories leads to Remote Code Execution
An arbitrary file write vulnerability exists in OpenProject’s repository changes endpoint (/projects/:project_id/repository/changes) when rendering the “latest changes” view via git log.
By supplying a specially crafted rev value (for example, rev=--output=/tmp/poc.txt), an attacker can inject git log command-line options. When OpenProject executes the SCM command, Git interprets the attacker-controlled rev as an option and writes the output to an attacker-chosen path.
As a result, any user with the :browse_repository permission on the project can create or overwrite arbitrary files that the OpenProject process user is permitted to write. The written contents consist of git log output, but by crafting custom commits the attacker can still upload valid shell scripts, ultimately leading to RCE. The RCE lets the attacker create a reverse shell to the target host and view confidential files outside of OpenProject, such as /etc/passwd.
This vulnerability was reported by user sam91281 as part of the YesWeHack.com OpenProject Bug Bounty program, sponsored by the European Commission.
For more information, please see the GitHub advisory #GHSA-x37c-hcg5-r5m7
Bug fixes and changes
OpenProject 17.0.2
Release date: 2026-01-27
We released OpenProject OpenProject 17.0.2.
The release contains sa security fix and several bug fixes and we strongly recommend updating to the newest version.
Below you will find a complete list of all changes and bug fixes.
Security fixes
CVE-2026-24685 - Argument Injection on Repository Diff allows Arbitrary File Write and Remote Code Execution
An arbitrary file write vulnerability exists in OpenProject’s repository diff download endpoint (/projects/:project_id/repository/diff.diff) when rendering a single revision via git show. By supplying a specially crafted rev value (for example, rev=--output=/tmp/poc.txt), an attacker can inject git show command-line options. When OpenProject executes the SCM command, Git interprets the attacker-controlled rev as an option and writes the output to an attacker-chosen path.
As a result, any user with the :browse_repository permission on the project can create or overwrite arbitrary files that the OpenProject process user is permitted to write. The written contents consist of git show output (commit metadata and patch), but overwriting application or configuration files still leads to data loss and denial of service, impacting integrity and availability.
When the user has permissions to write into the repository, they can craft a specific commit to result in a RCE with permission scope of the OpenProject application.
This vulnerability was responsibly disclosed by sam91281 as part of the YesWeHack.com OpenProject Bug Bounty program, sponsored by the European Commission. Thank you for your collaboration.
For more information, please see the GitHub advisory #GHSA-74p5-9pr3-r6pw
CVE-2026-24772 - SSRF and CSWSH in Hocuspocus Synchronization Server
To enable the real time collaboration on documents, OpenProject 17.0 introduced a synchronization server. The OpenPrioject backend generates an authentication token that is currently valid for 24 hours, encrypts it with a shared secret only known to the synchronization server. The frontend hands this encrypted token and the backend URL over to the synchronization server to check user's ability to work on the document and perform intermittent saves while editing.
The synchronization server does not properly validate the backend URL and sends a request with the decrypted authentication token to the endpoint that was given to the server. An attacker could use this vulnerability to decrypt a token that he intercepted by other means to gain an access token to interact with OpenProject on the victim's behalf.
The vulnerability has been responsibly disclosed through the YesWeHack bounty program for OpenProject by Scott Curtis (syndrome_impostor). Thank you for the responsible disclosure and your collaboration in this report!
For more information, please see the GitHub advisory #GHSA-r854-p5qj-x974
CVE-2026-24775 - Forced Actions, Content Spoofing, and Persistent DoS via ID Manipulation in OpenProject Blocknote Editor Extension
In the new editor for collaborative documents based on BlockNote we added a custom extension that allows to mention OpenProject work packages in the document. To show work package details, the editor loads details about the work package via the OpenProject API. For this API call, the extension to the BlockNote editor did not properly validate the given work package ID to be only a number. This allowed an attacker to generate a document with relative links that upon opening could make arbitrary GET requests to any URL within the OpenProject instance.
The vulnerability has been responsibly disclosed through the YesWeHack bounty program for OpenProject by Scott Curtis (syndrome_impostor). Thank you two for the responsible disclosure and your collaboration in this report!
For more information, please see the GitHub advisory #GHSA-35c6-x276-2pvc
Bug fixes and changes
- Bugfix: Unable to change to earlier finish date for automatically scheduled successor [#65130]
- Bugfix: Meeting outcomes cannot be saved with ctrl/cmd+enter [#69974]
- Bugfix: AXe Accessibility error: invalid list structure [#70573]
- Bugfix: Fix AXe Accessibility error: Navigation toggler must have discernible text [#70574]
- Bugfix: Documents module is missing meaningfull html title [#70614]
- Bugfix: Users with the "Manage Users" permission did not see links to Lock/Unlock users [#70796]
- Bugfix: Cannot authorise OpenProject app with OpenProject when user has 2FA enabled [#70966]
- Bugfix: Running docker slim image, runs slim-bim one [#70980]
- Bugfix: 'For all projects' project attributes are not displayed during new project creation [#70982]
- Bugfix: Fix revision parsing in git diff output [#71020]
OpenProject 16.6.6
Release date: 2026-01-27
We released OpenProject OpenProject 16.6.6.
The release contains security related bug fixes and we strongly urge you to update to the newest version.
Below you will find a complete list of all changes and bug fixes.
Security fixes
CVE-2026-24685 - Argument Injection on Repository Diff allows Arbitrary File Write and Remote Code Execution
An arbitrary file write vulnerability exists in OpenProject’s repository diff download endpoint (/projects/:project_id/repository/diff.diff) when rendering a single revision via git show. By supplying a specially crafted rev value (for example, rev=--output=/tmp/poc.txt), an attacker can inject git show command-line options. When OpenProject executes the SCM command, Git interprets the attacker-controlled rev as an option and writes the output to an attacker-chosen path.
As a result, any user with the :browse_repository permission on the project can create or overwrite arbitrary files that the OpenProject process user is permitted to write. The written contents consist of git show output (commit metadata and patch), but overwriting application or configuration files still leads to data loss and denial of service, impacting integrity and availability.
When the user has permissions to write into the repository, they can craft a specific commit to result in a RCE with permission scope of the OpenProject application.
This vulnerability was responsibly disclosed by sam91281 as part of the YesWeHack.com OpenProject Bug Bounty program, sponsored by the European Commission. Thank you for your collaboration.
For more information, please see the GitHub advisory #GHSA-74p5-9pr3-r6pw
Bug fixes and changes
- Bugfix: Fix revision parsing in git diff output [#71019]
OpenProject 17.0.1
Release date: 2026-01-16
We released OpenProject OpenProject 17.0.1.
The release contains several bug fixes and we recommend updating to the newest version.
Below you will find a complete list of all changes and bug fixes.
Security fixes
CVE-2026-23646 - Users can delete other user's session, causing them to be logged out
Users in OpenProject have the ability to view and end their active sessions via Account Settings → Sessions. When deleting a session, it was not properly checked if the session belongs to the user. As the ID that is used to identify these session objects use incremental integers, users could iterate requests using DELETE /my/sessions/:id and thus unauthenticate other users.
Users did not have access to any sensitive information (like browser identifier, IP addresses, etc) of other users that are stored in the session.
This vulnerability was assigned as CVE-2026-23646.
For more information, please see the GitHub Advisory GHSA-w422-xf8f-v4vp).
The vulnerability has been responsibly disclosed through the YesWeHack bounty program for OpenProject. This bug bounty program is being sponsored by the European Commission.
CVE-2026-23721 - Users with "View Members" permission in any project can view all Group memberships
When using groups in OpenProject to manage users, the group members should only be visible to users that have the View Members permission in any project that the group is also a member of.
Due to a failed permission check, if a user had the View Members permission in any project, they could enumerate all Groups and view which other users are part of the group.
This vulnerability was assigned as CVE-2026-23721.
For more information, please see the GitHub Advisory GHSA-vj77-wrc2-5h5h).
The vulnerability has been responsibly disclosed through the YesWeHack bounty program for OpenProject. This bug bounty program is being sponsored by the European Commission.
CVE-2026-23625 - Stored XSS regression on OpenProject using attachments and script-src self
OpenProject versions >= 16.3.0, < 16.6.5, < 17.0.1 is affected by a stored XSS vulnerability in the Roadmap view. OpenProject’s roadmap view renders the “Related work packages” list for each version. When a version contains work packages from a different project (e.g., a subproject), the helper link_to_work_package prepends package.project.to_s to the link and returns the entire string with .html_safe. Because project names are user-controlled and no escaping happens before calling html_safe, any HTML placed in a subproject name is injected verbatim into the page.
This vulnerability was assigned as CVE-2026-23625.
For more information, please see the GitHub Advisory GHSA-cvpq-cc56-gwxx).
The vulnerability has been responsibly disclosed through the YesWeHack bounty program for OpenProject. This bug bounty program is being sponsored by the European Commission.
Bug fixes and changes
- Bugfix: BlockNote: OpenProject work packages are sorted by their ID instead of the last updated by [#67536]
- Bugfix: Required project attributes not enforced on POST /api/v3/projects [#70107]
- Bugfix: NoMethodError in Storages::Admin::AccessManagementController#update [#70492]
- Bugfix: Form Configuration for Work Package Types does not properly validate Enterprise Plan [#70503]
- Bugfix: PDF export with custom uploaded logo/fonts fails with some storage configurations (S3) [#70560]
OpenProject 16.6.5
Release date: 2026-01-16
We released OpenProject OpenProject 16.6.5.
The release contains several bug fixes and we recommend updating to the newest version.
Below you will find a complete list of all changes and bug fixes.
Security Fixes
CVE-2026-23646 - Users can delete other user's session, causing them to be logged out
Users in OpenProject have the ability to view and end their active sessions via Account Settings → Sessions. When deleting a session, it was not properly checked if the session belongs to the user. As the ID that is used to identify these session objects use incremental integers, users could iterate requests using DELETE /my/sessions/:id and thus unauthenticate other users.
Users did not have access to any sensitive information (like browser identifier, IP addresses, etc) of other users that are stored in the session.
This vulnerability was assigned as CVE-2026-23646.
For more information, please see the GitHub Advisory GHSA-w422-xf8f-v4vp).
The vulnerability has been responsibly disclosed through the YesWeHack bounty program for OpenProject. This bug bounty program is being sponsored by the European Commission.
CVE-2026-23721 - Users with "View Members" permission in any project can view all Group memberships
When using groups in OpenProject to manage users, the group members should only be visible to users that have the View Members permission in any project that the group is also a member of.
Due to a failed permission check, if a user had the View Members permission in any project, they could enumerate all Groups and view which other users are part of the group.
This vulnerability was assigned as CVE-2026-23721.
For more information, please see the GitHub Advisory GHSA-vj77-wrc2-5h5h).
The vulnerability has been responsibly disclosed through the YesWeHack bounty program for OpenProject. This bug bounty program is being sponsored by the European Commission.
CVE-2026-23625 - Stored XSS regression on OpenProject using attachments and script-src self
OpenProject versions >= 16.3.0, < 16.6.5, < 17.0.1 is affected by a stored XSS vulnerability in the Roadmap view. OpenProject’s roadmap view renders the “Related work packages” list for each version. When a version contains work packages from a different project (e.g., a subproject), the helper link_to_work_package prepends package.project.to_s to the link and returns the entire string with .html_safe. Because project names are user-controlled and no escaping happens before calling html_safe, any HTML placed in a subproject name is injected verbatim into the page.
This vulnerability was assigned as CVE-2026-23625.
For more information, please see the GitHub Advisory GHSA-cvpq-cc56-gwxx).
The vulnerability has been responsibly disclosed through the YesWeHack bounty program for OpenProject. This bug bounty program is being sponsored by the European Commission.
Bug fixes and changes
- Bugfix: Add default framework headers removed in secure_headers [#70384]