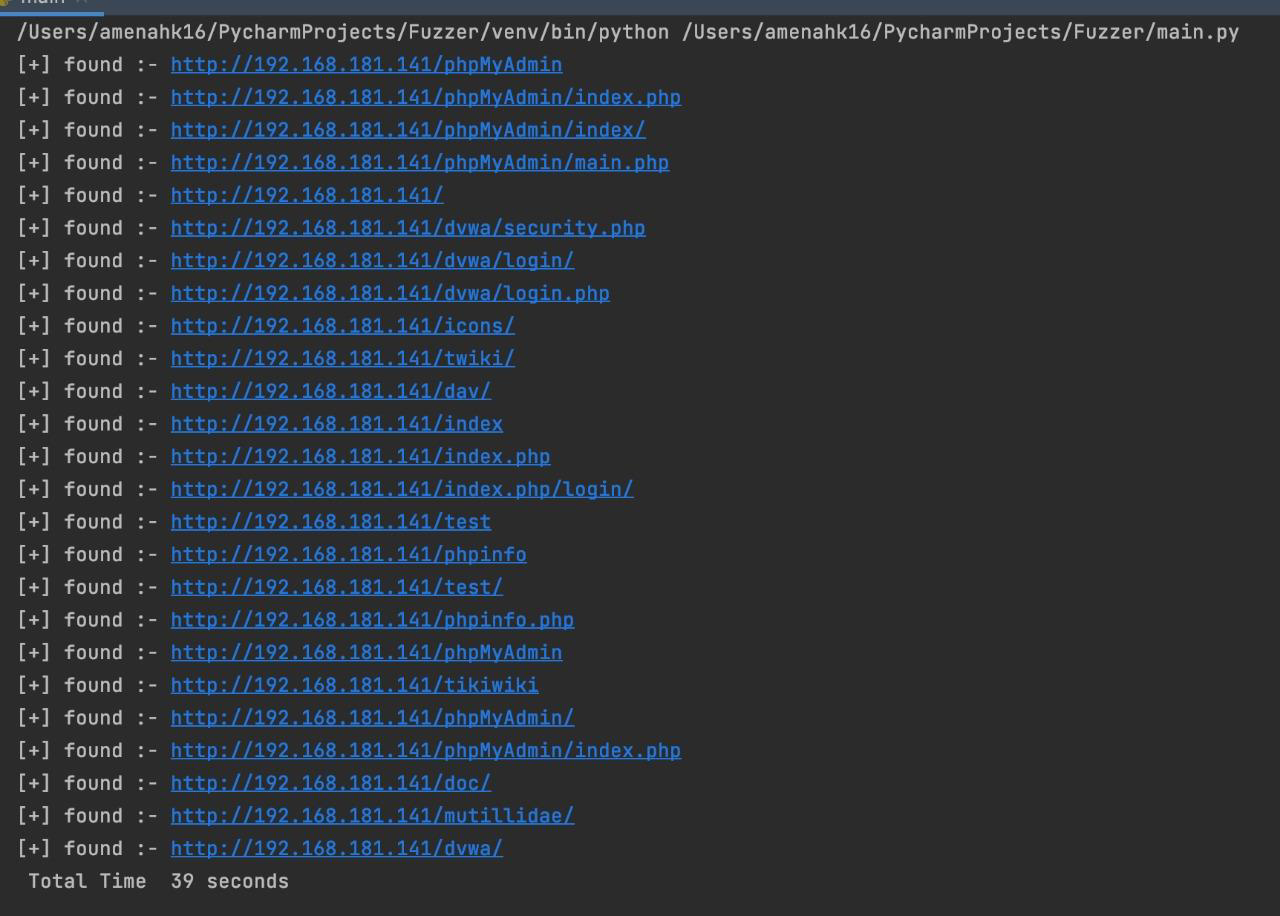
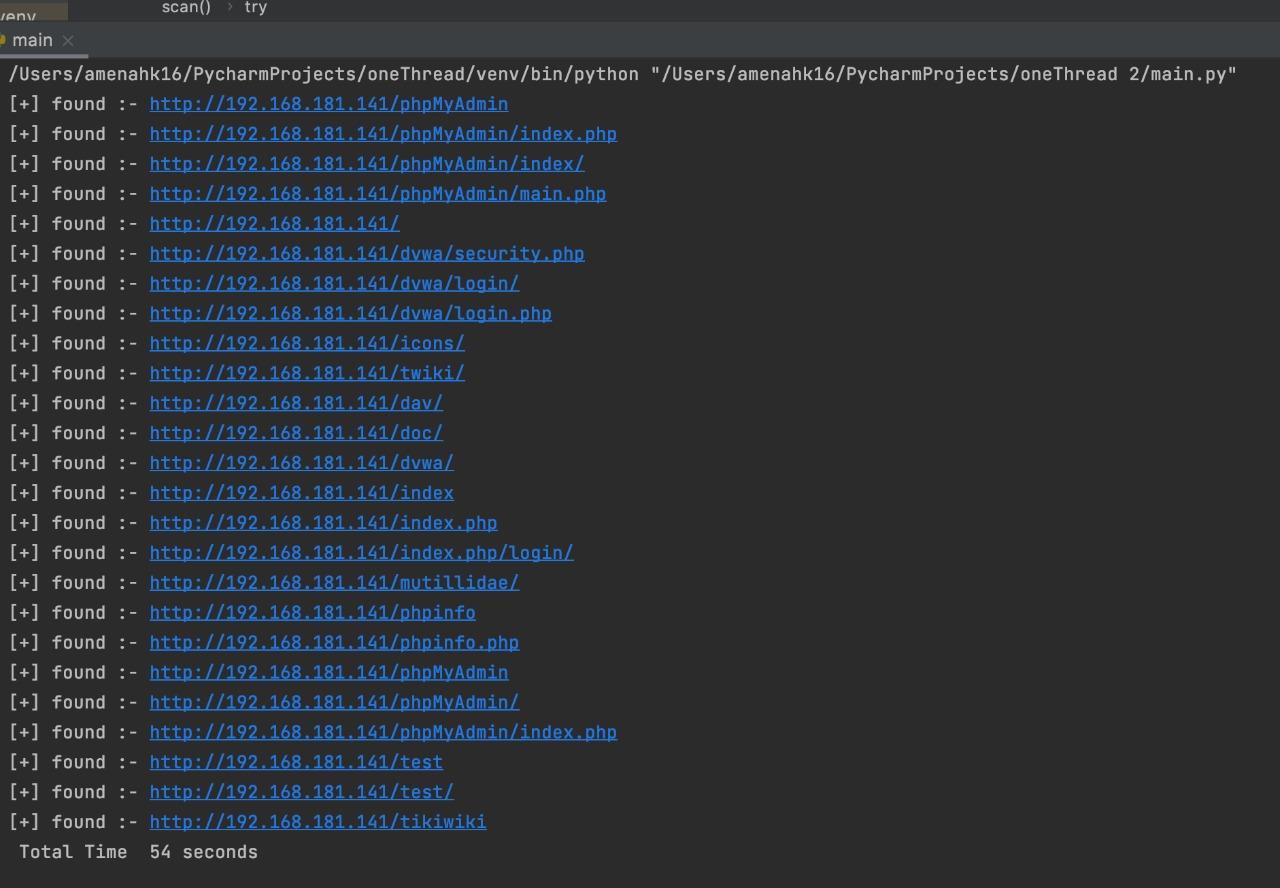
Fuzzing directories is a tool for exposing hidden paths by sending a request to a target URL using a payload wordlist line by line. The request will be made to see if this page exists depending on the status code of the response
- Identify the Metasploitable IP address
- Use the Metasploitable IP address as the target URL to fuzz it •
- Creating five threads to reduce running time
- Scan the URL
- Inject the URLs with payload wordlist line by line
- Send GET request with the injected URLs
- Check responds status code if it is = 200
- Print the URLs that matched status code 200
- Save the reachable URL after injected with payloads into a text file
Amenah Albuainain - Jana Alansari - Jana Alshaya - Samiyah ALrashidi - Wasmiyah Alqahtani